Hi, I got a problem with Click.giftload. Spybot can't remove it. It seems that I'm not the only one with this problem.
Here is my DDS log, hope you will be able to help me.
Thanks
.
DDS (Ver_11-03-05.01) - NTFSx86
Run by Tatiana at 11:18:05,89 on 25/03/2011
Internet Explorer: 8.0.6001.18702
Microsoft Windows XP Professionnel 5.1.2600.3.1252.33.1036.18.2046.1451 [GMT 1:00]
.
AV: avast! Antivirus *Enabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
.
============== Running Processes ===============
.
C:\WINDOWS\system32\savedump.exe
C:\WINDOWS\system32\svchost -k DcomLaunch
C:\WINDOWS\system32\svchost -k rpcss
C:\WINDOWS\System32\svchost.exe -k netsvcs
C:\WINDOWS\system32\svchost.exe -k NetworkService
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\Program Files\Alwil Software\Avast5\AvastSvc.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\ehome\ehtray.exe
C:\WINDOWS\stsystra.exe
C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe
C:\Program Files\iTunes\iTunesHelper.exe
C:\Program Files\HP\HP Software Update\HPWuSchd2.exe
C:\Program Files\Fichiers communs\Java\Java Update\jusched.exe
C:\Program Files\Alwil Software\Avast5\avastUI.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\WINDOWS\system32\rundll32.exe
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\Program Files\Digital Line Detect\DLG.exe
C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe
C:\Program Files\HP\Digital Imaging\bin\hpqimzone.exe
C:\WINDOWS\TEMP\lryj\setup.exe
C:\Program Files\HP\Digital Imaging\bin\hpqnrs08.exe
C:\Program Files\Fichiers communs\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
C:\WINDOWS\eHome\ehRecvr.exe
C:\WINDOWS\eHome\ehSched.exe
C:\Documents and Settings\All Users\Application Data\EPSON\EPW!3 SSRP\E_S40RP7.EXE
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINDOWS\system32\libusbd-nt.exe
C:\Program Files\Fichiers communs\Microsoft Shared\VS7DEBUG\MDM.EXE
C:\WINDOWS\system32\nvsvc32.exe
C:\WINDOWS\system32\HPZipm12.exe
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\WINDOWS\ehome\mcrdsvc.exe
C:\Program Files\HP\Digital Imaging\bin\hpqSTE08.exe
C:\WINDOWS\system32\wuauclt.exe
C:\Program Files\iPod\bin\iPodService.exe
C:\WINDOWS\system32\dllhost.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\eHome\ehmsas.exe
C:\WINDOWS\system32\wbem\wmiprvse.exe
C:\Documents and Settings\Tatiana\Bureau\dds.com
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://www.google.fr/
uURLSearchHooks: Search Class: {08c06d61-f1f3-4799-86f8-be1a89362c85} - c:\program files\orange\connexion internet orange\searchurlhook\SearchPageURL.dll
BHO: Aide pour le lien d'Adobe PDF Reader: {06849e9f-c8d7-4d59-b87d-784b7d6be0b3} - c:\program files\fichiers communs\adobe\acrobat\activex\AcroIEHelper.dll
BHO: Spybot-S&D IE Protection: {53707962-6f74-2d53-2644-206d7942484f} - c:\progra~1\spybot~1\SDHelper.dll
BHO: {5C255C8A-E604-49b4-9D64-90988571CECB} - No File
BHO: {7E853D72-626A-48EC-A868-BA8D5E23E045} - No File
BHO: Programme d'aide de l'Assistant de connexion Windows Live: {9030d464-4c02-4abf-8ecc-5164760863c6} - c:\program files\fichiers communs\microsoft shared\windows live\WindowsLiveLogin.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {dbc80044-a445-435b-bc74-9c25c1c588a9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl Class: {e7e6f031-17ce-4c07-bc86-eabfe594f69c} - c:\program files\java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
uRun: [CTFMON.EXE] c:\windows\system32\ctfmon.exe
uRun: [EPSON Stylus DX4400 Series] c:\windows\system32\spool\drivers\w32x86\3\e_faticae.exe /fu "c:\windows\temp\E_SAB.tmp" /EF "HKCU"
uRun: [SpybotSD TeaTimer] c:\program files\spybot - search & destroy\TeaTimer.exe
uRun: [Vkonisayik] rundll32.exe "c:\windows\msaptil.dll",Startup
uRun: [Java] c:\docume~1\tatiana\locals~1\temp\KCO2E.exe
uRun: [Java] c:\docume~1\tatiana\locals~1\temp\KCO2E.exe
mRun: [ehTray] c:\windows\ehome\ehtray.exe
mRun: [NvCplDaemon] RUNDLL32.EXE c:\windows\system32\NvCpl.dll,NvStartup
mRun: [SigmatelSysTrayApp] stsystra.exe
mRun: [NeroFilterCheck] c:\program files\fichiers communs\ahead\lib\NeroCheck.exe
mRun: [Adobe Reader Speed Launcher] "c:\program files\adobe\reader 8.0\reader\Reader_sl.exe"
mRun: [iTunesHelper] "c:\program files\itunes\iTunesHelper.exe"
mRun: [HP Software Update] c:\program files\hp\hp software update\HPWuSchd2.exe
mRun: [ORAHSSSessionManager] "c:\program files\orange\connexion internet orange\sessionmanager\SessionManager.exe"
mRun: [SunJavaUpdateSched] "c:\program files\fichiers communs\java\java update\jusched.exe"
mRun: [QuickTime Task] "c:\program files\quicktime\qttask.exe" -atboottime
mRun: [avast5] "c:\program files\alwil software\avast5\avastUI.exe" /nogui
mRun: [KernelFaultCheck] %systemroot%\system32\dumprep 0 -k
dRun: [CTFMON.EXE] c:\windows\system32\CTFMON.EXE
dRun: [AMService] c:\windows\temp\lryj\setup.exe
StartupFolder: c:\docume~1\alluse~1\menudm~1\progra~1\dmarra~1\digita~1.lnk - c:\program files\digital line detect\DLG.exe
StartupFolder: c:\docume~1\alluse~1\menudm~1\progra~1\dmarra~1\dmarra~1.lnk - c:\program files\hp\digital imaging\bin\hpqthb08.exe
StartupFolder: c:\docume~1\alluse~1\menudm~1\progra~1\dmarra~1\hpdigi~1.lnk - c:\program files\hp\digital imaging\bin\hpqtra08.exe
IE: E&xporter vers Microsoft Excel - c:\progra~1\micros~2\office11\EXCEL.EXE/3000
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {FB5F1910-F110-11d2-BB9E-00C04F795683} - c:\program files\messenger\msmsgs.exe
IE: {92780B25-18CC-41C8-B9BE-3C9C571A8263} - {FF059E31-CC5A-4E2E-BF3B-96E929D65503} - c:\progra~1\micros~2\office11\REFIEBAR.DLL
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\progra~1\spybot~1\SDHelper.dll
DPF: {166B1BCA-3F9C-11CF-8075-444553540000} - hxxp://download.macromedia.com/pub/shockwave/cabs/director/sw.cab
DPF: {67DABFBF-D0AB-41FA-9C46-CC0F21721616} - hxxp://download.divx.com/player/DivXBrowserPlugin.cab
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_23-windows-i586.cab
DPF: {8FFBE65D-2C9C-4669-84BD-5829DC0B603C} - hxxp://fpdownload.macromedia.com/get/flashplayer/current/ultrashim.cab
DPF: {CAFEEFAC-0016-0000-0003-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_03-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0005-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0007-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_07-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0011-ABCDEFFEDCBA}
DPF: {CAFEEFAC-0016-0000-0012-ABCDEFFEDCBA}
DPF: {CAFEEFAC-0016-0000-0015-ABCDEFFEDCBA}
DPF: {CAFEEFAC-0016-0000-0017-ABCDEFFEDCBA}
DPF: {CAFEEFAC-0016-0000-0020-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_20-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0021-ABCDEFFEDCBA}
DPF: {CAFEEFAC-0016-0000-0023-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_23-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_23-windows-i586.cab
DPF: {CFCDAA03-8BE4-11CF-B84B-0020AFBBCCFA} - hxxp://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
TCP: {1062E4BC-2F27-4BDF-9FBB-F7A8150EBCAB} = 212.27.53.252,212.27.54.252
SecurityProviders: msapsspc.dll, schannel.dll, digest.dll, msnsspc.dll, maltrcgn.dll, mnrpaitr.dll
.
============= SERVICES / DRIVERS ===============
.
.
=============== Created Last 30 ================
.
.
==================== Find3M ====================
.
.
=================== ROOTKIT ====================
.
Stealth MBR rootkit/Mebroot/Sinowal/TDL4 detector 0.4.2 by Gmer, http://www.gmer.net
Windows 5.1.2600 Disk: Intel___ rev.1.0. -> Harddisk0\DR0 -> \Device\Ide\iaStor0
.
device: opened successfully
user: MBR read successfully
.
Disk trace:
called modules: ntkrnlpa.exe CLASSPNP.SYS disk.sys >>UNKNOWN [0x89C83439]<<
_asm { PUSH EBP; MOV EBP, ESP; PUSH ECX; MOV EAX, [EBP+0x8]; CMP EAX, [0x89c897d0]; MOV EAX, [0x89c8984c]; PUSH EBX; PUSH ESI; MOV ESI, [EBP+0xc]; MOV EBX, [ESI+0x60]; PUSH EDI; JNZ 0x20; MOV [EBP+0x8], EAX; }
1 ntkrnlpa!IofCallDriver[0x804EF1A6] -> \Device\Harddisk0\DR0[0x8A5C7AB8]
3 CLASSPNP[0xBA0E8FD7] -> ntkrnlpa!IofCallDriver[0x804EF1A6] -> [0x89CAE7B8]
\Driver\iastor[0x8A5EA938] -> IRP_MJ_CREATE -> 0x89C83439
kernel: MBR read successfully
_asm { XOR AX, AX; MOV SS, AX; MOV SP, 0x7c00; MOV ES, AX; MOV DS, AX; MOV SI, 0x7c00; MOV DI, 0x600; MOV CX, 0x200; CLD ; REP MOVSB ; PUSH AX; PUSH 0x61c; RETF ; STI ; PUSHA ; MOV CX, 0x147; MOV BP, 0x62a; ROR BYTE [BP+0x0], CL; INC BP; }
detected disk devices:
\Device\Ide\IAAStorageDevice-0 -> \??\IDE#DiskRAIDHOME1.0.00__#4&674c230&0&0.0.0#{53f56307-b6bf-11d0-94f2-00a0c91efb8b} device not found
detected hooks:
user != kernel MBR !!!
sectors 488275966 (+255): user != kernel
Warning: possible TDL4 rootkit infection !
TDL4 rootkit infection detected ! Use: "mbr.exe -f" to fix.
.
============= FINISH: 11:20:14,78 ===============






 and not the others dics ? Or do I have to reformat all the discs ?
and not the others dics ? Or do I have to reformat all the discs ?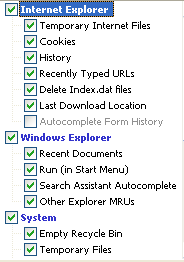



 (Selecting Uninstall application on close if you so wish)
(Selecting Uninstall application on close if you so wish)

