Patrick, its best to copy and paste the logs into the thread in lew of attaching them, its easier for me to analyze.
Looks like the Rootkit is gone
While I am looking over your Combofix log, run this program and post the log please
Please download Malwarebytes from Here or Here
Post the report please
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
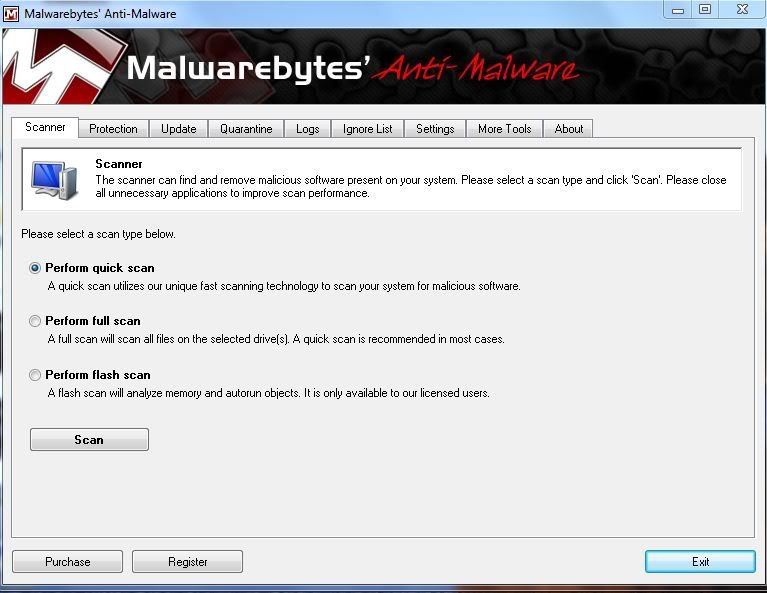
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected .
- When completed, a log will open in Notepad. Please save it to a convenient location and post the results.
- Note: If you receive a notice that some of the items couldn't be removed, that they have been added to the delete on reboot list, please reboot.



 button.
button. to download the ESET Smart Installer. Save it to your desktop.
to download the ESET Smart Installer. Save it to your desktop.
 button.
button.

 , and save the file to your desktop using a unique name, such as
, and save the file to your desktop using a unique name, such as button.
button.

