-
 Feel like I just took 2 steps back..
Feel like I just took 2 steps back..
After complete all the tasks you had requested I took one on the chin. The computer locked up after combo fix had displayed the log. So I had to reboot with hopes of recovering the log to send to you. As I was in the process of doing this I got the blue screen indicating to shut down and reboot in safe mode. Now back online in safe mode computer is moving superfast, ie: the internet and when I click on a program it prompts quickly. The log from the last combo fix run is MIA so I will do it again and post shortly.....oh and the killer is still not working...
-

Why dont you try Combofix in Safemode
C:\ComboFix.txt <-- The log may be here
-
 Combo fix, in Safe Mode
Combo fix, in Safe Mode
Out of Safe Mode, did it by itself during the combo fix: See Log.
ComboFix 11-06-04.02 - Tim 06/04/2011 13:39:43.6.1 - x86 NETWORK
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.254.151 [GMT -4:00]
Running from: c:\documents and settings\Tim\Desktop\ComboFix.exe
AV: AntiVir Desktop *Disabled/Updated* {AD166499-45F9-482A-A743-FDD3350758C7}
FW: Outpost Security Suite *Disabled* {8A20CA2A-9E02-4A64-923B-0A38208EB7FD}
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
C:\RECYCLER(2)
c:\recycler(2)\S-1-5-21-2392168675-1175828863-1792882590-1007(2)\INFO2
.
Infected copy of c:\windows\system32\userinit.exe was found and disinfected
Restored copy from - c:\windows\ERDNT\cache\userinit.exe
.
.
((((((((((((((((((((((((( Files Created from 2011-05-04 to 2011-06-04 )))))))))))))))))))))))))))))))
.
.
2011-06-03 19:06 . 2011-06-03 19:06 260 ----a-w- c:\windows\system32\cmdVBS.vbs
2011-06-03 19:06 . 2011-06-03 19:06 256 ----a-w- c:\windows\system32\MSIevent.bat
2011-06-03 18:58 . 2011-06-03 18:58 65536 ----a-r- c:\documents and settings\Tim\Application Data\Microsoft\Installer\{730EF0E8-8B8E-4054-B2CE-5D4BA3BCE510}\NewShortcut1_011BB310849E4442B8017718F2C57FE0.exe
2011-06-03 18:58 . 2011-06-03 18:58 65536 ----a-r- c:\documents and settings\Tim\Application Data\Microsoft\Installer\{730EF0E8-8B8E-4054-B2CE-5D4BA3BCE510}\NewShortcut1_9E64A938C044442B9C8C104AA62BD820.exe
2011-06-03 18:58 . 2011-06-03 18:58 65536 ----a-r- c:\documents and settings\Tim\Application Data\Microsoft\Installer\{730EF0E8-8B8E-4054-B2CE-5D4BA3BCE510}\ARPPRODUCTICON.exe
2011-06-03 18:57 . 2011-06-03 19:06 -------- d-----w- c:\program files\Verizon
2011-06-03 00:44 . 2011-06-03 00:44 -------- d-----w- c:\windows\system32\wbem\Repository
2011-06-02 22:48 . 2011-06-02 22:48 -------- d-----w- c:\program files\ESET
2011-05-29 15:35 . 2011-06-03 00:41 -------- d-----w- c:\program files\ERUNT
2011-05-14 17:01 . 2011-05-14 17:01 404640 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2011-05-05 19:14 . 2011-05-05 19:14 -------- d-sh--w- c:\documents and settings\LocalService\IETldCache
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2011-03-16 21:13 . 2011-01-03 21:44 137656 ----a-w- c:\windows\system32\drivers\avipbb.sys
2011-03-07 05:33 . 2004-06-07 19:19 692736 ----a-w- c:\windows\system32\inetcomm.dll
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\Outpost]
@="{33C9E362-3EDA-4930-8AFE-5DA39A8BB77A}"
[HKEY_CLASSES_ROOT\CLSID\{33C9E362-3EDA-4930-8AFE-5DA39A8BB77A}]
c:\program files\Agnitum\Outpost Security Suite Free\op_shell.dll [BU]
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"ISUSPM"="c:\program files\Common Files\InstallShield\UpdateService\ISUSPM.exe" [2006-09-11 218032]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"avgnt"="c:\program files\Avira\AntiVir Desktop\avgnt.exe" [2010-12-13 281768]
"OutpostMonitor"="c:\progra~1\Agnitum\OUTPOS~1\op_mon.exe" [BU]
"OutpostFeedBack"="c:\program files\Agnitum\Outpost Security Suite Free\feedback.exe" [BU]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-05-26 413696]
.
[HKEY_LOCAL_MACHINE\system\currentcontrolset\control\session manager]
BootExecute REG_MULTI_SZ autocheck autochk *\0c:\progra~1\AVG\AVG10\avgchsvx.exe /sync\0c:\progra~1\AVG\AVG10\avgrsx.exe /sync /restart
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Adobe Reader Speed Launch.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\Adobe Reader Speed Launch.lnk
backup=c:\windows\pss\Adobe Reader Speed Launch.lnkCommon Startup
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Desktop Manager.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\Desktop Manager.lnk
backup=c:\windows\pss\Desktop Manager.lnkCommon Startup
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Digital Imaging Monitor.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Digital Imaging Monitor.lnk
backup=c:\windows\pss\HP Digital Imaging Monitor.lnkCommon Startup
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Photosmart Premier Fast Start.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Photosmart Premier Fast Start.lnk
backup=c:\windows\pss\HP Photosmart Premier Fast Start.lnkCommon Startup
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Kodak EasyShare software.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\Kodak EasyShare software.lnk
backup=c:\windows\pss\Kodak EasyShare software.lnkCommon Startup
.
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Quicken Scheduled Updates.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\Quicken Scheduled Updates.lnk
backup=c:\windows\pss\Quicken Scheduled Updates.lnkCommon Startup
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe ARM]
2010-10-07 15:10 932288 ----a-w- c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe Reader Speed Launcher]
2010-09-24 09:15 40368 ----a-w- c:\program files\Adobe\Reader 8.0\Reader\reader_sl.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\ArcSoft Connection Service]
2009-07-06 18:30 195072 ----a-w- c:\program files\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\ctfmon.exe]
2008-04-14 00:12 15360 ----a-w- c:\windows\SYSTEM32\ctfmon.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\dla]
2004-03-15 06:04 122933 ----a-w- c:\windows\SYSTEM32\dla\tfswctrl.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\HP Software Update]
2006-02-19 07:41 49152 ----a-w- c:\program files\HP\HP Software Update\hpwuSchd2.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\igfxhkcmd]
2005-09-20 13:32 77824 ----a-w- c:\windows\SYSTEM32\hkcmd.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\igfxpers]
2005-09-20 13:36 114688 ----a-w- c:\windows\SYSTEM32\igfxpers.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\igfxtray]
2005-09-20 13:35 94208 ----a-w- c:\windows\SYSTEM32\igfxtray.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\IntelMeM]
2003-09-04 01:12 221184 ----a-w- c:\program files\Intel\Modem Event Monitor\IntelMEM.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\iTunesHelper]
2009-07-13 18:03 292128 ----a-w- c:\program files\iTunes\iTunesHelper.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\MSMSGS]
2008-04-14 00:12 1695232 ----a-w- c:\program files\Messenger\msmsgs.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Nikon Transfer Monitor]
2009-09-15 23:47 479232 ----a-w- c:\program files\Common Files\Nikon\Monitor\NkMonitor.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\PCMService]
c:\program files\Dell\Media Experience\PCMService.exe [BU]
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\QuickTime Task]
2009-05-26 21:18 413696 ----a-w- c:\program files\QuickTime\QTTask.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\RoxWatchTray]
2007-08-16 12:56 236016 ----a-w- c:\program files\Common Files\Roxio Shared\9.0\SharedCOM\RoxWatchTray9.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched]
2010-05-14 15:44 248552 ----a-w- c:\program files\Common Files\Java\Java Update\jusched.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\UpdateManager]
2003-08-19 06:01 110592 ----a-w- c:\program files\Common Files\Sonic\Update Manager\sgtray.exe
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"c:\\WINDOWS\\SYSTEM32\\LEXPPS.EXE"=
"c:\\Program Files\\Common Files\\AOL\\System Information\\sinf.exe"=
"c:\\Program Files\\Dell Computer\\Dell Picture Studio v2.0\\launch.exe"=
"c:\\Program Files\\Kodak\\Kodak EasyShare software\\bin\\EasyShare.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
"c:\\Program Files\\Roxio\\Media Manager 9\\MediaManager9.exe"=
"c:\\Program Files\\Roxio\\Digital Home 9\\RoxioUPnPRenderer9.exe"=
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"50000:UDP"= 50000:UDP:IHA_MessageCenter
.
R2 acssrv;Agnitum Client Security Service;c:\progra~1\Agnitum\OUTPOS~1\acs.exe [x]
R2 mrtRate;mrtRate; [x]
R3 afw;Agnitum firewall driver;c:\windows\system32\DRIVERS\afw.sys [2010-04-20 34280]
R3 afwcore;afwcore;c:\windows\system32\drivers\afwcore.sys [2010-09-27 267624]
R3 ASWFilt;ASWFilt;c:\windows\system32\Filt\ASWFilt.dll [2010-11-26 72352]
R3 FlyUsb;FLY Fusion;c:\windows\system32\DRIVERS\FlyUsb.sys [2009-11-10 18560]
R3 nosGetPlusHelper;getPlus(R) Helper 3004;c:\windows\System32\svchost.exe [2008-04-14 14336]
R3 VBEngNT;VBEngNT;c:\windows\system32\drivers\VBEngNT.sys [2010-06-09 241088]
R3 VBFilt;VBFilt;c:\windows\system32\Filt\VBFilt.dll [2010-11-26 36288]
S1 SandBox;SandBox;c:\windows\system32\drivers\SandBox.sys [2010-11-26 710696]
S2 AntiVirSchedulerService;Avira AntiVir Scheduler;c:\program files\Avira\AntiVir Desktop\sched.exe [2011-04-27 136360]
S2 IHA_MessageCenter;IHA_MessageCenter;c:\program files\Verizon\IHA_MessageCenter\Bin\Verizon_IHAMessageCenter.exe [2011-05-24 143360]
.
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\svchost]
nosGetPlusHelper REG_MULTI_SZ nosGetPlusHelper
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.app.com/
mStart Page = hxxp://www.msn.com
uInternet Settings,ProxyOverride = localhost
TCP: DhcpNameServer = 192.168.1.1 71.250.0.12
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2011-06-04 14:27
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'explorer.exe'(1236)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\mshtml.dll
c:\windows\system32\msls31.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
------------------------ Other Running Processes ------------------------
.
c:\windows\system32\LEXBCES.EXE
c:\windows\system32\LEXPPS.EXE
c:\program files\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
c:\program files\Avira\AntiVir Desktop\avguard.exe
c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
c:\program files\Avira\AntiVir Desktop\avshadow.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\windows\system32\HPZipm12.exe
c:\program files\Internet Explorer\IEXPLORE.EXE
c:\program files\Internet Explorer\IEXPLORE.EXE
.
**************************************************************************
.
Completion time: 2011-06-04 14:38:51 - machine was rebooted
ComboFix-quarantined-files.txt 2011-06-04 18:38
ComboFix2.txt 2011-06-04 16:38
ComboFix3.txt 2011-06-02 14:34
ComboFix4.txt 2011-01-03 03:20
.
Pre-Run: 16,284,446,720 bytes free
Post-Run: 16,007,987,200 bytes free
.
- - End Of File - - 7B79A21C2016DD38C3C655A63CE566D3
-


This was the culprit
Infected copy of c:\windows\system32\userinit.exe was found and disinfected
Restored copy from - c:\windows\ERDNT\cache\userinit.exe
Try running TDSSKiller, it may run now
-
 Back in safemode.
Back in safemode.
I re-installed a fresh copy of the TDSSKiller, but once again it will not perform after I click the run tab. In addition it appears that all other functions are working properly except for the sound. When I rebooted the Windows sound effect came through but if I pull up video on the Internet nothing comes through.
After I send the post I am going to restart and see what happens.
-
 Very Sluggish
Very Sluggish
Ken, I was able to reboot out of safemode mode but very sluggish. I then noticed a yellow triangle with an exclamation mark appear in the the toolbar. As soon as put the pointer over it without clicking it disappeared! It was the same icon as listed below. Still no sound...
-

Run aswMBR just to scan and let me see if anything changed. Make sure you post the new log, you can delete any others
-
 aswMBR3 log
aswMBR3 log
Still getting the redirect on a google search, and no sound from the internet.
aswMBR version 0.9.5.256 Copyright(c) 2011 AVAST Software
Run date: 2011-06-05 10:07:39
-----------------------------
10:07:39.421 OS Version: Windows 5.1.2600 Service Pack 3
10:07:39.421 Number of processors: 1 586 0x304
10:07:39.421 ComputerName: TORCHIA UserName: Tim
10:07:42.140 Initialize success
10:07:47.937 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3
10:07:47.937 Disk 0 Vendor: ST340014A 8.16 Size: 38146MB BusType: 3
10:07:49.968 Disk 0 MBR read successfully
10:07:49.968 Disk 0 MBR scan
10:07:49.984 Disk 0 Windows XP default MBR code
10:07:52.000 Disk 0 scanning sectors +78108030
10:07:52.015 Disk 0 scanning C:\WINDOWS\system32\drivers
10:08:02.093 Service scanning
10:08:05.437 Disk 0 trace - called modules:
10:08:05.453 ntoskrnl.exe CLASSPNP.SYS disk.sys >>UNKNOWN [0x81a871ed]<<
10:08:05.453 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x81b65030]
10:08:05.453 3 CLASSPNP.SYS[f9306fd7] -> nt!IofCallDriver -> \Device\Ide\IdeDeviceP0T0L0-3[0x81af4700]
10:08:05.453 \Driver\atapi[0x81af4f38] -> IRP_MJ_INTERNAL_DEVICE_CONTROL -> 0x81a871ed
10:08:05.468 Scan finished successfully
10:08:26.343 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\Tim\Desktop\MBR.dat"
10:08:26.343 The log file has been saved successfully to "C:\Documents and Settings\Tim\Desktop\aswMBR3.txt"
-

Lets run some more scans
Open Malwarebytes, check for updates and run the Quick Scan, if nothing is found no need for the log but let me know
Please download DeFogger to your desktop.
Double click DeFogger to run the tool.
- The application window will appear
- Click the Disable button to disable your CD Emulation drivers
- Click Yes to continue
- A 'Finished!' message will appear
- Click OK
- DeFogger will now ask to reboot the machine - click OK
IMPORTANT! If you receive an error message while running DeFogger, please post the log defogger_disable which will appear on your desktop.
Do not re-enable these drivers until otherwise instructed.
Next:
Download the GMER Rootkit Scanner. Unzip it to your Desktop.
Before scanning, make sure all other running programs are closed and no other actions like a scheduled antivirus scan will occur while the scan is being performed. Do not use your computer for anything else during the scan.
- Double click GMER.exe.

- If it gives you a warning about rootkit activity and asks if you want to run a full scan...click on NO, then use the following settings for a more complete scan..
- In the right panel, you will see several boxes that have been checked. Ensure the following are UNCHECKED ...
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
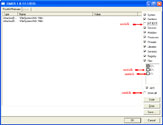
Click the image to enlarge it
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "ark.txt"
- Save the log where you can easily find it, such as your desktop.
**Caution**
Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Please copy and paste the report into your Post.
To re-enable your Emulation drivers, double click DeFogger to run the tool.
- The application window will appear
- Click the Re-enable button to re-enable your CD Emulation drivers
- Click Yes to continue
- A 'Finished!' message will appear
- Click OK
- DeFogger will now ask to reboot the machine - click OK
IMPORTANT! If you receive an error message while running DeFogger, please post the log defogger_enable which will appear on your desktop.
Your Emulation drivers are now re-enabled.
-
 Gmer and DeFogger complete.
Gmer and DeFogger complete.
Malwarebytes, No Malicious Threats found.
GMER 1.0.15.15640 - http://www.gmer.net
Rootkit scan 2011-06-05 12:23:03
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3 ST340014A rev.8.16
Running: gmer.exe; Driver: C:\DOCUME~1\Tim\LOCALS~1\Temp\fxrdipog.sys
---- System - GMER 1.0.15 ----
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwAllocateVirtualMemory [0xF8CEF6E0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwAssignProcessToJobObject [0xF8CEF610]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwClose [0xF8CED7E0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwConnectPort [0xF8CEF980]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwCreateFile [0xF8CED1B0]
SSDT EF2D1A66 ZwCreateKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwCreateProcess [0xF8CEEAB0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwCreateProcessEx [0xF8CEEBA0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwCreateSection [0xF8CECDE0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwCreateSymbolicLinkObject [0xF8CEDAB0]
SSDT EF2D1A5C ZwCreateThread
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwDebugActiveProcess [0xF8CEFFB0]
SSDT EF2D1A6B ZwDeleteKey
SSDT EF2D1A75 ZwDeleteValueKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwEnumerateKey [0xF8CEDE10]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwEnumerateValueKey [0xF8CEDEF0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwFsControlFile [0xF8CED0C0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwLoadDriver [0xF8CF2000]
SSDT EF2D1A7A ZwLoadKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwMakeTemporaryObject [0xF8CED9F0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwOpenFile [0xF8CED640]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwOpenKey [0xF8CEDC80]
SSDT EF2D1A48 ZwOpenProcess
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwOpenSection [0xF8CECEB0]
SSDT EF2D1A4D ZwOpenThread
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwProtectVirtualMemory [0xF8CEF8A0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwQueryKey [0xF8CEDFD0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwQueryValueKey [0xF8CEE0B0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwQueueApcThread [0xF8CEF540]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwRenameKey [0xF8CEE5B0]
SSDT EF2D1A84 ZwReplaceKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwRequestPort [0xF8CEFC50]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwRequestWaitReplyPort [0xF8CEFD20]
SSDT EF2D1A7F ZwRestoreKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSaveKey [0xF8CEE340]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSaveKeyEx [0xF8CEE410]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSecureConnectPort [0xF8CEFA70]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSetContextThread [0xF8CEF450]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSetInformationDebugObject [0xF8CF0080]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSetSecurityObject [0xF8CF0180]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSetSystemInformation [0xF8CEE760]
SSDT EF2D1A70 ZwSetValueKey
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSuspendProcess [0xF8CEF2A0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSuspendThread [0xF8CEF360]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwSystemDebugControl [0xF8CEFED0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwTerminateProcess [0xF8CEEF90]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwTerminateThread [0xF8CEF150]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwUnloadDriver [0xF8CEE830]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwWriteFile [0xF8CECFB0]
SSDT \??\C:\WINDOWS\system32\drivers\SandBox.sys (Host Protection Component/Agnitum Ltd.) ZwWriteVirtualMemory [0xF8CEF7C0]
---- Kernel code sections - GMER 1.0.15 ----
.text ntoskrnl.exe!_abnormal_termination + 108 804E2774 8 Bytes JMP EBA0F8CE
.text ntoskrnl.exe!_abnormal_termination + 440 804E2AAC 12 Bytes [A0, F2, CE, F8, 60, F3, CE, ...]
.text ntoskrnl.exe!_abnormal_termination + 464 804E2AD0 4 Bytes [30, E8, CE, F8] {XOR AL, CH; INTO ; CLC }
.text ntoskrnl.exe!_abnormal_termination + 4A0 804E2B0C 1 Byte [C0]
INITc VolSnap.sys F92F1BD0 4 Bytes [36, 9A, 4D, 80]
INITc VolSnap.sys F92F1BF8 4 Bytes [94, 87, 4E, 80] {XCHG ESP, EAX; XCHG [ESI-0x80], ECX}
INITc VolSnap.sys F92F1C20 4 Bytes [A0, C1, 4D, 80]
INITc VolSnap.sys F92F1C48 4 Bytes [B0, C8, 4D, 80]
INITc VolSnap.sys F92F1C70 4 Bytes [09, BF, 4D, 80]
INITc ...
init C:\WINDOWS\System32\DRIVERS\mohfilt.sys entry point in "init" section [0xF9641760]
? C:\DOCUME~1\Tim\LOCALS~1\Temp\aswMBR.sys The system cannot find the file specified. !
---- User code sections - GMER 1.0.15 ----
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!DialogBoxParamW 7E4247AB 5 Bytes JMP 3E2154BD C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 3E2E9B01 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!CallNextHookEx 7E42B3C6 5 Bytes JMP 3E2DD125 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!CreateWindowExW 7E42D0A3 5 Bytes JMP 3E2EDB5C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 3E254664 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!DialogBoxIndirectParamW 7E432072 5 Bytes JMP 3E3E5117 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!MessageBoxIndirectA 7E43A082 5 Bytes JMP 3E3E5049 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!DialogBoxParamA 7E43B144 5 Bytes JMP 3E3E50B4 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!MessageBoxExW 7E450838 5 Bytes JMP 3E3E4F1A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!MessageBoxExA 7E45085C 5 Bytes JMP 3E3E4F7C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!DialogBoxIndirectParamA 7E456D7D 5 Bytes JMP 3E3E517A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] USER32.dll!MessageBoxIndirectW 7E4664D5 5 Bytes JMP 3E3E4FDE C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] ole32.dll!CoCreateInstance 774FF1AC 5 Bytes JMP 3E2EDBB8 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] ole32.dll!OleLoadFromStream 7752981B 5 Bytes JMP 3E3E547F C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!getaddrinfo 71AB2A6F 5 Bytes JMP 00D5000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!closesocket 71AB3E2B 5 Bytes JMP 00D2000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!connect 71AB4A07 5 Bytes JMP 00D1000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!send 71AB4C27 5 Bytes JMP 00D3000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!gethostbyname 71AB5355 5 Bytes JMP 00D4000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WS2_32.dll!recv 71AB676F 5 Bytes JMP 00D0000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WININET.dll!HttpAddRequestHeadersA 3D94CF4E 5 Bytes JMP 00B16B70
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[1232] WININET.dll!HttpAddRequestHeadersW 3D94FE49 5 Bytes JMP 00B16D70
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!DialogBoxParamW 7E4247AB 5 Bytes JMP 3E2154BD C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!CreateWindowExW 7E42D0A3 5 Bytes JMP 3E2EDB5C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!DialogBoxIndirectParamW 7E432072 5 Bytes JMP 3E3E5117 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!MessageBoxIndirectA 7E43A082 5 Bytes JMP 3E3E5049 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!DialogBoxParamA 7E43B144 5 Bytes JMP 3E3E50B4 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!MessageBoxExW 7E450838 5 Bytes JMP 3E3E4F1A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!MessageBoxExA 7E45085C 5 Bytes JMP 3E3E4F7C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!DialogBoxIndirectParamA 7E456D7D 5 Bytes JMP 3E3E517A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] USER32.dll!MessageBoxIndirectW 7E4664D5 5 Bytes JMP 3E3E4FDE C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!getaddrinfo 71AB2A6F 5 Bytes JMP 00CF000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!closesocket 71AB3E2B 5 Bytes JMP 00B3000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!connect 71AB4A07 5 Bytes JMP 0059000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!send 71AB4C27 5 Bytes JMP 00B4000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!gethostbyname 71AB5355 5 Bytes JMP 00B5000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WS2_32.dll!recv 71AB676F 5 Bytes JMP 0058000A
.text C:\Program Files\internet explorer\iexplore.exe[1740] WININET.dll!HttpAddRequestHeadersA 3D94CF4E 5 Bytes JMP 00B16B70
.text C:\Program Files\internet explorer\iexplore.exe[1740] WININET.dll!HttpAddRequestHeadersW 3D94FE49 5 Bytes JMP 00B16D70
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!DialogBoxParamW 7E4247AB 5 Bytes JMP 3E2154BD C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!SetWindowsHookExW 7E42820F 5 Bytes JMP 3E2E9B01 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!CallNextHookEx 7E42B3C6 5 Bytes JMP 3E2DD125 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!CreateWindowExW 7E42D0A3 5 Bytes JMP 3E2EDB5C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!UnhookWindowsHookEx 7E42D5F3 5 Bytes JMP 3E254664 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!DialogBoxIndirectParamW 7E432072 5 Bytes JMP 3E3E5117 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!MessageBoxIndirectA 7E43A082 5 Bytes JMP 3E3E5049 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!DialogBoxParamA 7E43B144 5 Bytes JMP 3E3E50B4 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!MessageBoxExW 7E450838 5 Bytes JMP 3E3E4F1A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!MessageBoxExA 7E45085C 5 Bytes JMP 3E3E4F7C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!DialogBoxIndirectParamA 7E456D7D 5 Bytes JMP 3E3E517A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] USER32.dll!MessageBoxIndirectW 7E4664D5 5 Bytes JMP 3E3E4FDE C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] ole32.dll!CoCreateInstance 774FF1AC 5 Bytes JMP 3E2EDBB8 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] ole32.dll!OleLoadFromStream 7752981B 5 Bytes JMP 3E3E547F C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!getaddrinfo 71AB2A6F 5 Bytes JMP 00F0000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!closesocket 71AB3E2B 5 Bytes JMP 00B4000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!connect 71AB4A07 5 Bytes JMP 00B3000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!send 71AB4C27 5 Bytes JMP 00B5000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!gethostbyname 71AB5355 5 Bytes JMP 00EF000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WS2_32.dll!recv 71AB676F 5 Bytes JMP 0059000A
.text C:\Program Files\internet explorer\iexplore.exe[2148] WININET.dll!HttpAddRequestHeadersA 3D94CF4E 5 Bytes JMP 00B16B70
.text C:\Program Files\internet explorer\iexplore.exe[2148] WININET.dll!HttpAddRequestHeadersW 3D94FE49 5 Bytes JMP 00B16D70
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!DialogBoxParamW 7E4247AB 5 Bytes JMP 3E2154BD C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!CreateWindowExW 7E42D0A3 5 Bytes JMP 3E2EDB5C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!DialogBoxIndirectParamW 7E432072 5 Bytes JMP 3E3E5117 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!MessageBoxIndirectA 7E43A082 5 Bytes JMP 3E3E5049 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!DialogBoxParamA 7E43B144 5 Bytes JMP 3E3E50B4 C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!MessageBoxExW 7E450838 5 Bytes JMP 3E3E4F1A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!MessageBoxExA 7E45085C 5 Bytes JMP 3E3E4F7C C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!DialogBoxIndirectParamA 7E456D7D 5 Bytes JMP 3E3E517A C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] USER32.dll!MessageBoxIndirectW 7E4664D5 5 Bytes JMP 3E3E4FDE C:\WINDOWS\system32\IEFRAME.dll (Internet Explorer/Microsoft Corporation)
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!getaddrinfo 71AB2A6F 5 Bytes JMP 00CF000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!closesocket 71AB3E2B 5 Bytes JMP 00B3000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!connect 71AB4A07 5 Bytes JMP 0059000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!send 71AB4C27 5 Bytes JMP 00B4000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!gethostbyname 71AB5355 5 Bytes JMP 00B5000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WS2_32.dll!recv 71AB676F 5 Bytes JMP 0058000A
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WININET.dll!HttpAddRequestHeadersA 3D94CF4E 5 Bytes JMP 00B16B70
.text C:\Program Files\Internet Explorer\IEXPLORE.EXE[3680] WININET.dll!HttpAddRequestHeadersW 3D94FE49 5 Bytes JMP 00B16D70
---- Threads - GMER 1.0.15 ----
Thread System [4:120] 81A8BE7A
Thread System [4:124] 81A8E008
---- EOF - GMER 1.0.15 ----
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules





