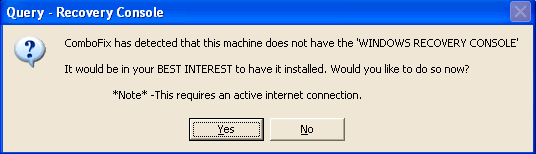
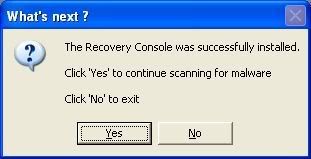
-
 nasty redirect in browswer: www.freeforfan.net
nasty redirect in browswer: www.freeforfan.net
I have installed and used both the S&D utilty, and the Auslogics utilties to try and correct.. this is tha latest attempt to fix my little problem. Any help would be appreciated!!
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 10:49:34 AM, on 6/25/2009
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Creative\Shared Files\CTAudSvc.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\WINDOWS\Explorer.EXE
C:\Program Files\Common Files\Creative Labs Shared\Service\CreativeLicensing.exe
C:\WINDOWS\system32\CTsvcCDA.exe
C:\WINDOWS\System32\GEARSec.exe
C:\Program Files\ATT-SST\McciTrayApp.exe
C:\Program Files\BellSouthWCC\McciTrayApp.exe
C:\Program Files\HP\HP Software Update\HPWuSchd2.exe
C:\WINDOWS\system32\CTXFIHLP.EXE
C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
C:\Program Files\Creative\MediaSource\Detector\CTDetect.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
C:\Program Files\Common Files\Motive\McciCMService.exe
C:\Documents and Settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe
C:\Program Files\Auslogics\Auslogics BoostSpeed\boostspeed.exe
C:\WINDOWS\SYSTEM32\CTXFISPI.EXE
C:\Program Files\Microsoft SQL Server\80\Tools\Binn\sqlmangr.exe
C:\Program Files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE
C:\Program Files\Microsoft SQL Server\MSSQL$MICROSOFTSMLBIZ\Binn\sqlservr.exe
C:\WINDOWS\system32\HPZipm12.exe
C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxWatch9.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Search Bar = http://us.rd.yahoo.com/customize/ie/...ch/search.html
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Search Page = http://us.rd.yahoo.com/customize/ie/.../www.yahoo.com
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.yahoo.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Bar = http://us.rd.yahoo.com/customize/ie/...ch/search.html
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKCU\Software\Microsoft\Internet Explorer\SearchURL,(Default) = http://us.rd.yahoo.com/customize/ie/.../www.yahoo.com
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = 127.0.0.1
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn\yt.dll
O1 - Hosts: 74.125.45.100 test1111.com
O1 - Hosts: 74.125.45.100 test1112.com
O1 - Hosts: 74.125.45.100 4-open-davinci.com
O1 - Hosts: 74.125.45.100 securitysoftwarepayments.com
O1 - Hosts: 74.125.45.100 privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 secure.privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 www.secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.securesoftwarebill.com
O1 - Hosts: 206.53.61.77 google.ae
O1 - Hosts: 206.53.61.77 google.as
O1 - Hosts: 206.53.61.77 google.at
O1 - Hosts: 206.53.61.77 google.az
O1 - Hosts: 206.53.61.77 google.ba
O1 - Hosts: 206.53.61.77 google.be
O1 - Hosts: 206.53.61.77 google.bg
O1 - Hosts: 206.53.61.77 google.bs
O1 - Hosts: 206.53.61.77 google.ca
O1 - Hosts: 206.53.61.77 google.cd
O1 - Hosts: 206.53.61.77 google.com.gh
O1 - Hosts: 206.53.61.77 google.com.hk
O1 - Hosts: 206.53.61.77 google.com.jm
O1 - Hosts: 206.53.61.77 google.com.mx
O1 - Hosts: 206.53.61.77 google.com.my
O1 - Hosts: 206.53.61.77 google.com.na
O1 - Hosts: 206.53.61.77 google.com.nf
O1 - Hosts: 206.53.61.77 google.com.ng
O1 - Hosts: 206.53.61.77 google.ch
O1 - Hosts: 206.53.61.77 google.com.np
O1 - Hosts: 206.53.61.77 google.com.pr
O1 - Hosts: 206.53.61.77 google.com.qa
O1 - Hosts: 206.53.61.77 google.com.sg
O1 - Hosts: 206.53.61.77 google.com.tj
O1 - Hosts: 206.53.61.77 google.com.tw
O1 - Hosts: 206.53.61.77 google.dj
O1 - Hosts: 206.53.61.77 google.de
O1 - Hosts: 206.53.61.77 google.dk
O1 - Hosts: 206.53.61.77 google.dm
O1 - Hosts: 206.53.61.77 google.ee
O1 - Hosts: 206.53.61.77 google.fi
O1 - Hosts: 206.53.61.77 google.fm
O1 - Hosts: 206.53.61.77 google.fr
O1 - Hosts: 206.53.61.77 google.ge
O1 - Hosts: 206.53.61.77 google.gg
O1 - Hosts: 206.53.61.77 google.gm
O1 - Hosts: 206.53.61.77 google.gr
O1 - Hosts: 206.53.61.77 google.ht
O1 - Hosts: 206.53.61.77 google.ie
O1 - Hosts: 206.53.61.77 google.im
O1 - Hosts: 206.53.61.77 google.in
O1 - Hosts: 206.53.61.77 google.it
O1 - Hosts: 206.53.61.77 google.ki
O1 - Hosts: 206.53.61.77 google.la
O1 - Hosts: 206.53.61.77 google.li
O1 - Hosts: 206.53.61.77 google.lv
O1 - Hosts: 206.53.61.77 google.ma
O1 - Hosts: 206.53.61.77 google.ms
O1 - Hosts: 206.53.61.77 google.mu
O1 - Hosts: 206.53.61.77 google.mw
O1 - Hosts: 206.53.61.77 google.nl
O1 - Hosts: 206.53.61.77 google.no
O1 - Hosts: 206.53.61.77 google.nr
O1 - Hosts: 206.53.61.77 google.nu
O1 - Hosts: 206.53.61.77 google.pl
O1 - Hosts: 206.53.61.77 google.pn
O1 - Hosts: 206.53.61.77 google.pt
O1 - Hosts: 206.53.61.77 google.ro
O1 - Hosts: 206.53.61.77 google.ru
O1 - Hosts: 206.53.61.77 google.rw
O1 - Hosts: 206.53.61.77 google.sc
O1 - Hosts: 206.53.61.77 google.se
O1 - Hosts: 206.53.61.77 google.sh
O1 - Hosts: 206.53.61.77 google.si
O1 - Hosts: 206.53.61.77 google.sm
O1 - Hosts: 206.53.61.77 google.sn
O1 - Hosts: 206.53.61.77 google.st
O1 - Hosts: 206.53.61.77 google.tl
O1 - Hosts: 206.53.61.77 google.tm
O1 - Hosts: 206.53.61.77 google.tt
O1 - Hosts: 206.53.61.77 google.us
O1 - Hosts: 206.53.61.77 google.vu
O1 - Hosts: 206.53.61.77 google.ws
O1 - Hosts: 206.53.61.77 google.co.ck
O1 - Hosts: 206.53.61.77 google.co.id
O1 - Hosts: 206.53.61.77 google.co.il
O1 - Hosts: 206.53.61.77 google.co.in
O1 - Hosts: 206.53.61.77 google.co.jp
O1 - Hosts: 206.53.61.77 google.co.kr
O1 - Hosts: 206.53.61.77 google.co.ls
O1 - Hosts: 206.53.61.77 google.co.ma
O1 - Hosts: 206.53.61.77 google.co.nz
O1 - Hosts: 206.53.61.77 google.co.tz
O1 - Hosts: 206.53.61.77 google.co.ug
O1 - Hosts: 206.53.61.77 google.co.uk
O1 - Hosts: 206.53.61.77 google.co.za
O1 - Hosts: 206.53.61.77 google.co.zm
O1 - Hosts: 206.53.61.77 google.com
O1 - Hosts: 206.53.61.77 google.com.af
O1 - Hosts: 206.53.61.77 google.com.ag
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn\yt.dll
O4 - HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [ATT-SST_McciTrayApp] "C:\Program Files\ATT-SST\McciTrayApp.exe"
O4 - HKLM\..\Run: [BellSouthWCC_McciTrayApp] C:\Program Files\BellSouthWCC\McciTrayApp.exe
O4 - HKLM\..\Run: [HP Software Update] C:\Program Files\HP\HP Software Update\HPWuSchd2.exe
O4 - HKLM\..\Run: [CTxfiHlp] CTXFIHLP.EXE
O4 - HKCU\..\Run: [Creative Detector] "C:\Program Files\Creative\MediaSource\Detector\CTDetect.exe" /R
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [Search Protection] C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
O4 - HKCU\..\Run: [YSearchProtection] C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
O4 - HKCU\..\Run: [Google Update] "C:\Documents and Settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe" /c
O4 - HKCU\..\Run: [Auslogics BoostSpeed 4] C:\Program Files\Auslogics\Auslogics BoostSpeed\boostspeed.exe
O4 - HKCU\..\RunOnce: [] C:\Program Files\Internet Explorer\iexplore.exe http://www.symantec.com/techsupp/ser...000d2.0000025e
O4 - Global Startup: Service Manager.lnk = C:\Program Files\Microsoft SQL Server\80\Tools\Binn\sqlmangr.exe
O6 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MI1933~1\OFFICE11\EXCEL.EXE/3000
O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_06\bin\npjpi150_06.dll
O9 - Extra 'Tools' menuitem: Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_06\bin\npjpi150_06.dll
O9 - Extra button: Yahoo! Services - {5BAB4B5B-68BC-4B02-94D6-2FC0DE4A7897} - C:\WINDOWS\system32\shdocvw.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MI1933~1\OFFICE11\REFIEBAR.DLL
O9 - Extra button: Real.com - {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - C:\WINDOWS\system32\Shdocvw.dll
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O16 - DPF: vzTCPConfig - http://www.verizon.net/checkmypc/fio...zTCPConfig.CAB
O16 - DPF: {1663ed61-23eb-11d2-b92f-008048fdd814} (MeadCo ScriptX Advanced) - https://www3.eleadcrm.com/evo2/fresh...ation/smsx.cab
O16 - DPF: {200B3EE9-7242-4EFD-B1E4-D97EE825BA53} (VerifyGMN Class) - http://h20270.www2.hp.com/ediags/gmn...taller_gmn.cab
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (Installation Support) - C:\Program Files\Yahoo!\Common\Yinsthelper.dll
O16 - DPF: {49232000-16E4-426C-A231-62846947304B} (SysData Class) - https://wimpro.cce.hp.com/ChatEntry/...ds/sysinfo.cab
O16 - DPF: {4C39376E-FA9D-4349-BACC-D305C1750EF3} (EPUImageControl Class) - http://tools.ebayimg.com/eps/wl/acti..._v1-0-3-48.cab
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5} (Symantec RuFSI Utility Class) - http://security.symantec.com/sscv6/S.../bin/cabsa.cab
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://update.microsoft.com/microsof...?1164731403000
O16 - DPF: {97BB6657-DC7F-4489-9067-51FAB9D8857E} (CWebLaunchCtl Object) - https://control.everdream.com/cf1liv...weblaunch2.cab
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/ge...sh/swflash.cab
O16 - DPF: {E06E2E99-0AA1-11D4-ABA6-0060082AA75C} (GpcContainer Class) - https://themeetingson.webex.com/clie...ex/ieatgpc.cab
O23 - Service: Creative Audio Engine Licensing Service - Creative Labs - C:\Program Files\Common Files\Creative Labs Shared\Service\CTAELicensing.exe
O23 - Service: Creative Labs Licensing Service - Creative Labs - C:\Program Files\Common Files\Creative Labs Shared\Service\CreativeLicensing.exe
O23 - Service: Creative Service for CDROM Access - Creative Technology Ltd - C:\WINDOWS\system32\CTsvcCDA.exe
O23 - Service: Creative Audio Service (CTAudSvcService) - Creative Technology Ltd - C:\Program Files\Creative\Shared Files\CTAudSvc.exe
O23 - Service: GEARSecurity - GEAR Software - C:\WINDOWS\System32\GEARSec.exe
O23 - Service: Google Update Service (gupdate1c9a7fe50862e34) (gupdate1c9a7fe50862e34) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Intel(R) Matrix Storage Event Monitor (IAANTMON) - Intel Corporation - C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\1150\Intel 32\IDriverT.exe
O23 - Service: McciCMService - Motive Communications, Inc. - C:\Program Files\Common Files\Motive\McciCMService.exe
O23 - Service: NVIDIA Display Driver Service (NVSvc) - NVIDIA Corporation - C:\WINDOWS\system32\nvsvc32.exe
O23 - Service: Pml Driver HPZ12 - HP - C:\WINDOWS\system32\HPZipm12.exe
O23 - Service: Roxio UPnP Renderer 9 - Sonic Solutions - C:\Program Files\Common Files\Sonic Shared\RoxioUPnPRenderer9.exe
O23 - Service: Roxio Upnp Server 9 - Sonic Solutions - C:\Program Files\Common Files\Sonic Shared\RoxioUpnpService9.exe
O23 - Service: LiveShare P2P Server 9 (RoxLiveShare9) - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxLiveShare9.exe
O23 - Service: RoxMediaDB9 - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe
O23 - Service: Roxio Hard Drive Watcher 9 (RoxWatch9) - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxWatch9.exe
O23 - Service: stllssvr - MicroVision Development, Inc. - C:\Program Files\Common Files\SureThing Shared\stllssvr.exe
O23 - Service: Yahoo! Updater (YahooAUService) - Yahoo! Inc. - C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
--
End of file - 14896 bytes
HERE IS MY HOSTS FILE
# Copyright (c) 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhost
74.125.45.100 test1111.com
74.125.45.100 test1112.com
74.125.45.100 4-open-davinci.com
74.125.45.100 securitysoftwarepayments.com
74.125.45.100 privatesecuredpayments.com
74.125.45.100 secure.privatesecuredpayments.com
74.125.45.100 getantivirusplusnow.com
74.125.45.100 secure-plus-payments.com
74.125.45.100 www.getantivirusplusnow.com
74.125.45.100 www.secure-plus-payments.com
74.125.45.100 www.securesoftwarebill.com
206.53.61.77 google.ae
206.53.61.77 google.as
206.53.61.77 google.at
206.53.61.77 google.az
206.53.61.77 google.ba
206.53.61.77 google.be
206.53.61.77 google.bg
206.53.61.77 google.bs
206.53.61.77 google.ca
206.53.61.77 google.cd
206.53.61.77 google.com.gh
206.53.61.77 google.com.hk
206.53.61.77 google.com.jm
206.53.61.77 google.com.mx
206.53.61.77 google.com.my
206.53.61.77 google.com.na
206.53.61.77 google.com.nf
206.53.61.77 google.com.ng
206.53.61.77 google.ch
206.53.61.77 google.com.np
206.53.61.77 google.com.pr
206.53.61.77 google.com.qa
206.53.61.77 google.com.sg
206.53.61.77 google.com.tj
206.53.61.77 google.com.tw
206.53.61.77 google.dj
206.53.61.77 google.de
206.53.61.77 google.dk
206.53.61.77 google.dm
206.53.61.77 google.ee
206.53.61.77 google.fi
206.53.61.77 google.fm
206.53.61.77 google.fr
206.53.61.77 google.ge
206.53.61.77 google.gg
206.53.61.77 google.gm
206.53.61.77 google.gr
206.53.61.77 google.ht
206.53.61.77 google.ie
206.53.61.77 google.im
206.53.61.77 google.in
206.53.61.77 google.it
206.53.61.77 google.ki
206.53.61.77 google.la
206.53.61.77 google.li
206.53.61.77 google.lv
206.53.61.77 google.ma
206.53.61.77 google.ms
206.53.61.77 google.mu
206.53.61.77 google.mw
206.53.61.77 google.nl
206.53.61.77 google.no
206.53.61.77 google.nr
206.53.61.77 google.nu
206.53.61.77 google.pl
206.53.61.77 google.pn
206.53.61.77 google.pt
206.53.61.77 google.ro
206.53.61.77 google.ru
206.53.61.77 google.rw
206.53.61.77 google.sc
206.53.61.77 google.se
206.53.61.77 google.sh
206.53.61.77 google.si
206.53.61.77 google.sm
206.53.61.77 google.sn
206.53.61.77 google.st
206.53.61.77 google.tl
206.53.61.77 google.tm
206.53.61.77 google.tt
206.53.61.77 google.us
206.53.61.77 google.vu
206.53.61.77 google.ws
206.53.61.77 google.co.ck
206.53.61.77 google.co.id
206.53.61.77 google.co.il
206.53.61.77 google.co.in
206.53.61.77 google.co.jp
206.53.61.77 google.co.kr
206.53.61.77 google.co.ls
206.53.61.77 google.co.ma
206.53.61.77 google.co.nz
206.53.61.77 google.co.tz
206.53.61.77 google.co.ug
206.53.61.77 google.co.uk
206.53.61.77 google.co.za
206.53.61.77 google.co.zm
206.53.61.77 google.com
206.53.61.77 google.com.af
206.53.61.77 google.com.ag
206.53.61.77 google.com.ar
206.53.61.77 google.com.au
206.53.61.77 google.com.bn
206.53.61.77 google.com.br
206.53.61.77 google.com.by
206.53.61.77 google.com.bz
206.53.61.77 google.com.cu
206.53.61.77 google.com.ec
206.53.61.77 google.com.fj
206.53.61.77 www.google.ae
206.53.61.77 www.google.as
206.53.61.77 www.google.at
206.53.61.77 www.google.az
206.53.61.77 www.google.ba
206.53.61.77 www.google.be
206.53.61.77 www.google.bg
206.53.61.77 www.google.bs
206.53.61.77 www.google.ca
206.53.61.77 www.google.cd
206.53.61.77 www.google.com.gh
206.53.61.77 www.google.com.hk
206.53.61.77 www.google.com.jm
206.53.61.77 www.google.com.mx
206.53.61.77 www.google.com.my
206.53.61.77 www.google.com.na
206.53.61.77 www.google.com.nf
206.53.61.77 www.google.com.ng
206.53.61.77 www.google.ch
206.53.61.77 www.google.com.np
206.53.61.77 www.google.com.pr
206.53.61.77 www.google.com.qa
206.53.61.77 www.google.com.sg
206.53.61.77 www.google.com.tj
206.53.61.77 www.google.com.tw
206.53.61.77 www.google.dj
206.53.61.77 www.google.de
206.53.61.77 www.google.dk
206.53.61.77 www.google.dm
206.53.61.77 www.google.ee
206.53.61.77 www.google.fi
206.53.61.77 www.google.fm
206.53.61.77 www.google.fr
206.53.61.77 www.google.ge
206.53.61.77 www.google.gg
206.53.61.77 www.google.gm
206.53.61.77 www.google.gr
206.53.61.77 www.google.ht
206.53.61.77 www.google.ie
206.53.61.77 www.google.im
206.53.61.77 www.google.in
206.53.61.77 www.google.it
206.53.61.77 www.google.ki
206.53.61.77 www.google.la
206.53.61.77 www.google.li
206.53.61.77 www.google.lv
206.53.61.77 www.google.ma
206.53.61.77 www.google.ms
206.53.61.77 www.google.mu
206.53.61.77 www.google.mw
206.53.61.77 www.google.nl
206.53.61.77 www.google.no
206.53.61.77 www.google.nr
206.53.61.77 www.google.nu
206.53.61.77 www.google.pl
206.53.61.77 www.google.pn
206.53.61.77 www.google.pt
206.53.61.77 www.google.ro
206.53.61.77 www.google.ru
206.53.61.77 www.google.rw
206.53.61.77 www.google.sc
206.53.61.77 www.google.se
206.53.61.77 www.google.sh
206.53.61.77 www.google.si
206.53.61.77 www.google.sm
206.53.61.77 www.google.sn
206.53.61.77 www.google.st
206.53.61.77 www.google.tl
206.53.61.77 www.google.tm
206.53.61.77 www.google.tt
206.53.61.77 www.google.us
206.53.61.77 www.google.vu
206.53.61.77 www.google.ws
206.53.61.77 www.google.co.ck
206.53.61.77 www.google.co.id
206.53.61.77 www.google.co.il
206.53.61.77 www.google.co.in
206.53.61.77 www.google.co.jp
206.53.61.77 www.google.co.kr
206.53.61.77 www.google.co.ls
206.53.61.77 www.google.co.ma
206.53.61.77 www.google.co.nz
206.53.61.77 www.google.co.tz
206.53.61.77 www.google.co.ug
206.53.61.77 www.google.co.uk
206.53.61.77 www.google.co.za
206.53.61.77 www.google.co.zm
206.53.61.77 www.google.com
206.53.61.77 www.google.com.af
206.53.61.77 www.google.com.ag
206.53.61.77 www.google.com.ar
206.53.61.77 www.google.com.au
206.53.61.77 www.google.com.bn
206.53.61.77 www.google.com.br
206.53.61.77 www.google.com.by
206.53.61.77 www.google.com.bz
206.53.61.77 www.google.com.cu
206.53.61.77 www.google.com.ec
206.53.61.77 www.google.com.fj
206.53.61.77 google.com
206.53.61.77 www.google.com
206.53.61.77 bing.com
206.53.61.77 www.bing.com
206.53.61.77 search.yahoo.com
206.53.61.77 www.search.yahoo.com
206.53.61.77 search.live.com
206.53.61.77 search.msn.com
206.53.61.77 googleads.g.doubleclick.net
206.53.61.77 www.googleads.g.doubleclick.net
206.53.61.77 pubads.g.doubleclick.net
206.53.61.77 www.pubads.g.doubleclick.net
206.53.61.77 partner.googleadservices.com
206.53.61.77 www.partner.googleadservices.com
206.53.61.77 www.partner.googleadservices.com
-

Hello bhellmol
Welcome to Safer Networking.
Please read Before You Post
That said, All advice given by anyone volunteering here, is taken at your own risk.
While best efforts are made to assist in removing infections safely, unexpected stuff can happen.
Download the HostsXpert 4.2.0.0. - Hosts File Manager.
- Unzip HostsXpert 4.2.0.0 - Hosts File Manager to a convenient folder such as C:\HostsXpert
- Click HostsXpert.exe to Run HostsXpert - Hosts File Manager from its new home
- Click "Make Hosts Writable?" in the upper right corner (If available).
- Click Restore Microsoft's Hosts file and then click OK.
- Click the X to exit the program.
- Note: If you were using a custom Hosts file you will need to replace any of those entries yourself.
Please download ATF Cleaner by Atribune to your desktop.
- Double-click ATF-Cleaner.exe to run the program.
- Under Main choose: Select All
- Click the Empty Selected button.
Your system may start up slower after running ATF Cleaner, this is expected but will be back to normal after the first or second boot up
Please note: If you use online banking or are registered online with any other organizations, ensure you have memorized password and other personal information as removing cookies will temporarily disable the auto-login facility.
Please download Malwarebytes' Anti-Malware from Here or Here
Double Click mbam-setup.exe to install the application.
- Make sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select "Perform Quick Scan", then click Scan.
- The scan may take some time to finish,so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected.<-- Don't forget this
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy and Paste the entire report in your next reply along with a New Hijackthis log.
-
 Unable to restore Hosts file
Unable to restore Hosts file
Hi Ken,
Thanks so much for your help on this. I tried to restore the hosts file using HostsExpert you mentioned.
When I open the program, it defalts to the "File Handling" sceen and shows the following 'buttons':
"Make Read Only?"
"Backup/Restore"
"Import Options"
I do not see a button that reads "Make Hosts Writable" anywhere on the screen.
When I click on "Restore MS Hosts File" it first says, "Press OK to Restore Microsofts original Hosts File." When I click OK, I get a stop error message saying, "ERROR: Cannot Create file C:\Windows\System32\DRIVERS\ETC\hosts"
-
 Other information concerning problems
Other information concerning problems
Hi Ken,
I did not mention it in the original post, but whne I instal any of the virus programs such as Norton or AVS, the program appears to be complately installed, but when I click on any of the user interface options (try to open the program) the waiting hourglass comes up for a split second... but nothing opens...
Ben
-
 Malwarebytes' Anti-Malware (Part One)
Malwarebytes' Anti-Malware (Part One)
Here are the Malwarebytes' Anti-Malware and HJT files as requested... bear in mind I was not able to restore the Hosts file.
Malwarebytes' Anti-Malware 1.38
Database version: 2338
Windows 5.1.2600 Service Pack 3
6/26/2009 9:10:23 AM
mbam-log-2009-06-26 (09-10-23).txt
Scan type: Quick Scan
Objects scanned: 117018
Time elapsed: 2 minute(s), 49 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 571
Registry Values Infected: 0
Registry Data Items Infected: 12
Folders Infected: 1
Files Infected: 6
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\APVXDWIN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LUALL.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Nmain.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ACKWIN32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ANTI-Trojan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AUTODOWN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCONSOL.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVE32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVGCTRL.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVKSERV.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVNT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPCC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPDOS32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPTC32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPUPD.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVSCHED32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVWIN95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVWUPD32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BLACKD.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BLACKICE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CFIADMIN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CFIAUDIT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CFINET.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CFINET32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CLAW95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CLAW95CF.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CLEANER.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CLEANER3.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\DVP95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\DVP95_0.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ECENGINE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ESAFE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\F-AGNT95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\F-PROT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\F-PROT95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\F-STOPW.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FINDVIRU.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FP-WIN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FPROT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FRW.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IAMAPP.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IAMSERV.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IBMASN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IBMAVSP.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ICLOAD95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ICLOADNT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ICMON.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ICSUPP95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ICSUPPNT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IFACE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IOMON98.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\JEDI.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LOCKDOWN2000.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LOOKOUT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MOOLIVE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MPFTRAY.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\N32SCANW.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapw32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NAVLU32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NAVNT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NISUM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NORMIST.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NUPGRADE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NVC95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PAVCL.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PAVSCHED.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PAVW.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PCCWIN98.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PCFWALLICON.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PERSFW.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAV7.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAV7WIN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SAFEWEB.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCAN32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCAN95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCANPM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCRSCAN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SERV95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SMC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SPHINX.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SWEEP95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TBSCAN.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TCA.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TDS2-98.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TDS2-NT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VET95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VETTRAY.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VSCAN40.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VSECOMR.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VSHWIN32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VSSTAT.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WEBSCANX.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WFINDV32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ZONEALARM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_AVP32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_AVPCC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_AVPM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avsynmgr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CCAPP.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\espwatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lucomserver.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Monitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nisserv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\notstart.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nsched32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\padmin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rapapp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedt32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rescue.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VET32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AgentSvr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\symlcsvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rtvscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPTray.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FCH32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSGK32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSM32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSMB32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GUARD.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCAgent.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCMSCSVC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCNASVC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCPROXY.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCSHIELD.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCSYSMON.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MPFSRV.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Nvsvc32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PAVFNSVR.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PAVSRV51.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PSCTRLS.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PSIMSVC.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCHED.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TCM.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TPSRV.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WEBPROXY.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\defwatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rescue32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scam32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\symproxysvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPC32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\webtrap.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avltmain.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ccevtmgr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcvsshld.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mghtml.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcshell.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pop3trap.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Agentw.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alogserv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AluSchedulerSvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\amon9x.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antiVirus.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ants.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\apimonitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aplica32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\arr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atcon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atguard.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atupdater.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atwatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\au.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aupdate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\auto-protect.nav80try.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autoTrace.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autoupdate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avciman.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgcc32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgemc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgrsx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgserv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgserv9.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgtray.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avkpop.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avkservice.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avkwctl9.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avwin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avwinnt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avwupd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avwupsrv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avxmonitor9x.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avxmonitornt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avxquar.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\backweb.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bargains.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bd_professional.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bdmcon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\beagle.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bidef.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bidserver.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bipcp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bipcpevalsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\blink.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\blss.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bootconf.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bootwarn.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\borg2.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bpc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brasil.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bs120.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bundle.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bvt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ccpxysvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cdp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cfd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cfgwiz.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\clean.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cleanpc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\click.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmesys.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmgrdian.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmon016.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\connectionmonitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\control (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cpd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cpf9x206.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cpfnt206.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ctrl.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cwnb181.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cwntdwmo.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\datemanager.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dcomx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\defalert.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\defscangui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\deputy.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dllcache.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dllreg.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\doors.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dpf.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dpfsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dpps2.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\drwatson.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dssAgent.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\efpeadm.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\emsw.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ent.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\escanhnt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\escanv95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ethereal.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\etrustcipe.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\evpn.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\exantiVirus-cnet.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\exe.avxw.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\expert.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explore.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fast.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fih32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\firewall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fnrb32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fp-win_trial.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsaa.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsav.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsav530stbyb.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsav530wtbyb.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsav95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gator.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbmenu.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbpoll.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\generics.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gmt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\guarddog.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hackTracersetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hbinst.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hbsrv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hotactio.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hotpatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\htlog.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\htpatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hwpe.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hxdl.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hxiul.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iamstats.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\idle.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iedll.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iedriver.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ifw2000.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\inetlnfo.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\infus.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\infwin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\init.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\intdel.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\intren.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\istsvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\jammer.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\jdbgmrg.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavlite40eng.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavpers40eng.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kazza.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\keenvalue.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kerio-pf-213-en-win.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kerio-wrl-421-en-win.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kerio-wrp-421-en-win.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\killprocesssetup161.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\launcher.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ldnetmon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ldpro.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ldpromenu.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ldscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lnetinfo.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\loader.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\localnet.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lockdown.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lordpe.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\lsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\luau.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\luinit.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\luspt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mapisvc32.exe (Security.Hijack) -> Quarantined and deleted successfully.
-
 Malwarebytes' Anti-Malware (Part Two)
Malwarebytes' Anti-Malware (Part Two)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcmnhdlr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\McSACore.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mctool.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcupdate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcvsrte.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\md.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mfin32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mfw2en.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mfweng3.02d30.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mgavrtcl.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mgavrte.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mgui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\minilog.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmod.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mpfAgent.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mpfservice.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mrflux.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msapp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msbb.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msblast.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mscache.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msccn32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mscman.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msdm.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msdos.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msiexec16.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mslaugh.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmgt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmsgri32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssys.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msvxd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mu0311ad.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mwatch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nav.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\navap.navapsvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\navdx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nc2000.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ncinst4.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ndd32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\neomonitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\neowatchlog.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netarmor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netd32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netinfo.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netmon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netscanpro.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netspyhunter-1.2.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netutils.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\norton_Internet_secu_3.0_407.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npf40_tw_98_nt_me_2k.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nprotect.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npscheck.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npssvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nssys32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nstask32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nsupdate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ntrtscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ntvdm.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ntxconfig.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nui.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nvarch16.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nwinst4.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nwservice.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nwtool16.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\onsrvr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\optimize.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ostronet.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\otfix.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\outpostinstall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\outpostproinstall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\panixk.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\patch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pavproxy.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pavprsrv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pdsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\periscope.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\perswf.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pf2.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pfwadmin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pgmonitr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pingscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\poproxy.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\popscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\portdetective.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\portmonitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\powerscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ppinupdt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pptbc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ppvstop.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\prizesurfer.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\prmt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\prmvr.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procdump.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\processmonitor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procExplorerv1.0.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\programauditor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\proport.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protectx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PskSvc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pspf.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\purge.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qconsole.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qserver.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rav8win32eng.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ray.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rb32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rcsync.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\realmon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\reged.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rrguard.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rshell.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rtvscn95.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rulaunch.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sahAgent.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\save.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\savenow.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sbserv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\setup_flowprotector_us.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\setupvameeval.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sgssfw32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sh.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\shellspyinstall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\shn.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\showbehind.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sms.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smss32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\soap.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sofi.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sperm.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spf.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spoler.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spoolcv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spoolsv32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spyxx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srexe.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ss3edit.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ssg_4104.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ssgrate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\st2.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\start.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\stcloader.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\supftrl.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\support.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\supporter5.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchostc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchosts.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svshost.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sweepnet.sweepsrv.sys.swnetsup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\symtray.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\System.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\System32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sysupd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taumon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tc.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tds-3.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\teekids.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tfak.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tfak5.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tgbob.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\titanin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\titaninxp.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\trickler.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\trjscan.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\trjsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Trojantrap3.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tvmd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tvtmd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\undoboot.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\updat.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\upgrad.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utpost.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbcmserv.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbcons.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbust.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbwin9x.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbwinntw.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vcsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vfsetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vir-help.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Virusmdpersonalfirewall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vnlan300.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vnpc3000.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vpc42.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vpfw30s.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vscenu6.02d30.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsched.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsisetup.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsmain.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsmon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vswin9xe.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vswinntse.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vswinperse.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\w32dsm89.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\w9x.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\watchdog.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\webdav.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\whoswatchingme.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wimmun32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\win32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\win32us.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winactive.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\win-bugsfix.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\window.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Windows.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wininetd.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wininit.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wininitx.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winlogin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winmain.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winnet.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winppr32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winrecon.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winservn.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winssk32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winstart.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winstart001.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wintsk32.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winupdate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wkufind.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wnad.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wnt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wradmin.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wrctrl.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsbgate.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wupdater.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wupdt.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wyvernworksfirewall.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xpf202en.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zatutor.exe (Security.Hijack) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zonalm2601.exe (Security.Hijack) -> Quarantined and deleted successfully.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
HKEY_USERS\S-1-5-20\SOFTWARE\Classes\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
HKEY_USERS\S-1-5-19\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
HKEY_USERS\S-1-5-19\SOFTWARE\Classes\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
HKEY_USERS\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
HKEY_USERS\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\URL (Search.Hijack) -> Bad: (http://plexfind.com/?aid=10010&n=10&subid=227e_102&q={searchTerms}) Good: (http://www.Google.com/) -> Quarantined and deleted successfully.
Folders Infected:
c:\documents and settings\ellen hellmoldt\application data\Fast Antivirus 2009 (Rogue.FastAntiVirus) -> Quarantined and deleted successfully.
Files Infected:
c:\RECYCLER\NPROTECT\00001449.EXE (Rogue.Installer) -> Quarantined and deleted successfully.
c:\documents and settings\ellen hellmoldt\start menu\Programs\Fast Antivirus 2009.lnk (Rogue.FastAntiVirus) -> Quarantined and deleted successfully.
c:\documents and settings\ellen hellmoldt\start menu\Fast Antivirus 2009.lnk (Rogue.FastAntiVirus) -> Quarantined and deleted successfully.
c:\documents and settings\ellen hellmoldt\application data\microsoft\internet explorer\quick launch\Fast Antivirus 2009.lnk (Rogue.FastAntiVirus) -> Quarantined and deleted successfully.
c:\documents and settings\ellen hellmoldt\Desktop\Fast Antivirus 2009.lnk (Rogue.FastAntiVirus) -> Quarantined and deleted successfully.
c:\WINDOWS\system32\wini101981.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
-
 HJT Log after Malawerbytes
HJT Log after Malawerbytes
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 9:15:45 AM, on 6/26/2009
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Creative\Shared Files\CTAudSvc.exe
C:\Program Files\Common Files\Creative Labs Shared\Service\CreativeLicensing.exe
C:\WINDOWS\system32\CTsvcCDA.exe
C:\WINDOWS\System32\GEARSec.exe
C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
C:\Program Files\Common Files\Motive\McciCMService.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\Program Files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE
C:\Program Files\Microsoft SQL Server\MSSQL$MICROSOFTSMLBIZ\Binn\sqlservr.exe
C:\WINDOWS\system32\nvsvc32.exe
C:\WINDOWS\system32\HPZipm12.exe
C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxWatch9.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\wuauclt.exe
C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe
C:\Program Files\ATT-SST\McciTrayApp.exe
C:\Program Files\BellSouthWCC\McciTrayApp.exe
C:\Program Files\HP\HP Software Update\HPWuSchd2.exe
C:\WINDOWS\system32\CTXFIHLP.EXE
C:\Program Files\Creative\MediaSource\Detector\CTDetect.exe
C:\WINDOWS\SYSTEM32\CTXFISPI.EXE
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
C:\Documents and Settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe
C:\Program Files\Auslogics\Auslogics BoostSpeed\boostspeed.exe
C:\Program Files\Microsoft SQL Server\80\Tools\Binn\sqlmangr.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Search Bar = http://us.rd.yahoo.com/customize/ie/...ch/search.html
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Search Page = http://us.rd.yahoo.com/customize/ie/.../www.yahoo.com
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.yahoo.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Bar = http://us.rd.yahoo.com/customize/ie/...ch/search.html
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKCU\Software\Microsoft\Internet Explorer\SearchURL,(Default) = http://us.rd.yahoo.com/customize/ie/.../www.yahoo.com
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = 127.0.0.1
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn\yt.dll
O1 - Hosts: 74.125.45.100 test1111.com
O1 - Hosts: 74.125.45.100 test1112.com
O1 - Hosts: 74.125.45.100 4-open-davinci.com
O1 - Hosts: 74.125.45.100 securitysoftwarepayments.com
O1 - Hosts: 74.125.45.100 privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 secure.privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 www.secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.securesoftwarebill.com
O1 - Hosts: 206.53.61.77 google.ae
O1 - Hosts: 206.53.61.77 google.as
O1 - Hosts: 206.53.61.77 google.at
O1 - Hosts: 206.53.61.77 google.az
O1 - Hosts: 206.53.61.77 google.ba
O1 - Hosts: 206.53.61.77 google.be
O1 - Hosts: 206.53.61.77 google.bg
O1 - Hosts: 206.53.61.77 google.bs
O1 - Hosts: 206.53.61.77 google.ca
O1 - Hosts: 206.53.61.77 google.cd
O1 - Hosts: 206.53.61.77 google.com.gh
O1 - Hosts: 206.53.61.77 google.com.hk
O1 - Hosts: 206.53.61.77 google.com.jm
O1 - Hosts: 206.53.61.77 google.com.mx
O1 - Hosts: 206.53.61.77 google.com.my
O1 - Hosts: 206.53.61.77 google.com.na
O1 - Hosts: 206.53.61.77 google.com.nf
O1 - Hosts: 206.53.61.77 google.com.ng
O1 - Hosts: 206.53.61.77 google.ch
O1 - Hosts: 206.53.61.77 google.com.np
O1 - Hosts: 206.53.61.77 google.com.pr
O1 - Hosts: 206.53.61.77 google.com.qa
O1 - Hosts: 206.53.61.77 google.com.sg
O1 - Hosts: 206.53.61.77 google.com.tj
O1 - Hosts: 206.53.61.77 google.com.tw
O1 - Hosts: 206.53.61.77 google.dj
O1 - Hosts: 206.53.61.77 google.de
O1 - Hosts: 206.53.61.77 google.dk
O1 - Hosts: 206.53.61.77 google.dm
O1 - Hosts: 206.53.61.77 google.ee
O1 - Hosts: 206.53.61.77 google.fi
O1 - Hosts: 206.53.61.77 google.fm
O1 - Hosts: 206.53.61.77 google.fr
O1 - Hosts: 206.53.61.77 google.ge
O1 - Hosts: 206.53.61.77 google.gg
O1 - Hosts: 206.53.61.77 google.gm
O1 - Hosts: 206.53.61.77 google.gr
O1 - Hosts: 206.53.61.77 google.ht
O1 - Hosts: 206.53.61.77 google.ie
O1 - Hosts: 206.53.61.77 google.im
O1 - Hosts: 206.53.61.77 google.in
O1 - Hosts: 206.53.61.77 google.it
O1 - Hosts: 206.53.61.77 google.ki
O1 - Hosts: 206.53.61.77 google.la
O1 - Hosts: 206.53.61.77 google.li
O1 - Hosts: 206.53.61.77 google.lv
O1 - Hosts: 206.53.61.77 google.ma
O1 - Hosts: 206.53.61.77 google.ms
O1 - Hosts: 206.53.61.77 google.mu
O1 - Hosts: 206.53.61.77 google.mw
O1 - Hosts: 206.53.61.77 google.nl
O1 - Hosts: 206.53.61.77 google.no
O1 - Hosts: 206.53.61.77 google.nr
O1 - Hosts: 206.53.61.77 google.nu
O1 - Hosts: 206.53.61.77 google.pl
O1 - Hosts: 206.53.61.77 google.pn
O1 - Hosts: 206.53.61.77 google.pt
O1 - Hosts: 206.53.61.77 google.ro
O1 - Hosts: 206.53.61.77 google.ru
O1 - Hosts: 206.53.61.77 google.rw
O1 - Hosts: 206.53.61.77 google.sc
O1 - Hosts: 206.53.61.77 google.se
O1 - Hosts: 206.53.61.77 google.sh
O1 - Hosts: 206.53.61.77 google.si
O1 - Hosts: 206.53.61.77 google.sm
O1 - Hosts: 206.53.61.77 google.sn
O1 - Hosts: 206.53.61.77 google.st
O1 - Hosts: 206.53.61.77 google.tl
O1 - Hosts: 206.53.61.77 google.tm
O1 - Hosts: 206.53.61.77 google.tt
O1 - Hosts: 206.53.61.77 google.us
O1 - Hosts: 206.53.61.77 google.vu
O1 - Hosts: 206.53.61.77 google.ws
O1 - Hosts: 206.53.61.77 google.co.ck
O1 - Hosts: 206.53.61.77 google.co.id
O1 - Hosts: 206.53.61.77 google.co.il
O1 - Hosts: 206.53.61.77 google.co.in
O1 - Hosts: 206.53.61.77 google.co.jp
O1 - Hosts: 206.53.61.77 google.co.kr
O1 - Hosts: 206.53.61.77 google.co.ls
O1 - Hosts: 206.53.61.77 google.co.ma
O1 - Hosts: 206.53.61.77 google.co.nz
O1 - Hosts: 206.53.61.77 google.co.tz
O1 - Hosts: 206.53.61.77 google.co.ug
O1 - Hosts: 206.53.61.77 google.co.uk
O1 - Hosts: 206.53.61.77 google.co.za
O1 - Hosts: 206.53.61.77 google.co.zm
O1 - Hosts: 206.53.61.77 google.com
O1 - Hosts: 206.53.61.77 google.com.af
O1 - Hosts: 206.53.61.77 google.com.ag
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn\yt.dll
O3 - Toolbar: (no name) - {CCC7A320-B3CA-4199-B1A6-9F516DD69829} - (no file)
O4 - HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [ATT-SST_McciTrayApp] "C:\Program Files\ATT-SST\McciTrayApp.exe"
O4 - HKLM\..\Run: [BellSouthWCC_McciTrayApp] C:\Program Files\BellSouthWCC\McciTrayApp.exe
O4 - HKLM\..\Run: [HP Software Update] C:\Program Files\HP\HP Software Update\HPWuSchd2.exe
O4 - HKLM\..\Run: [CTxfiHlp] CTXFIHLP.EXE
O4 - HKCU\..\Run: [Creative Detector] "C:\Program Files\Creative\MediaSource\Detector\CTDetect.exe" /R
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [Search Protection] C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
O4 - HKCU\..\Run: [YSearchProtection] C:\Program Files\Yahoo!\Search Protection\SearchProtection.exe
O4 - HKCU\..\Run: [Google Update] "C:\Documents and Settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe" /c
O4 - HKCU\..\Run: [Auslogics BoostSpeed 4] C:\Program Files\Auslogics\Auslogics BoostSpeed\boostspeed.exe
O4 - HKCU\..\RunOnce: [] C:\Program Files\Internet Explorer\iexplore.exe http://www.symantec.com/techsupp/ser...000d2.0000025e
O4 - Global Startup: Service Manager.lnk = C:\Program Files\Microsoft SQL Server\80\Tools\Binn\sqlmangr.exe
O6 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MI1933~1\OFFICE11\EXCEL.EXE/3000
O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_06\bin\npjpi150_06.dll
O9 - Extra 'Tools' menuitem: Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_06\bin\npjpi150_06.dll
O9 - Extra button: Yahoo! Services - {5BAB4B5B-68BC-4B02-94D6-2FC0DE4A7897} - C:\WINDOWS\system32\shdocvw.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MI1933~1\OFFICE11\REFIEBAR.DLL
O9 - Extra button: Real.com - {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - C:\WINDOWS\system32\Shdocvw.dll
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O16 - DPF: vzTCPConfig - http://www.verizon.net/checkmypc/fio...zTCPConfig.CAB
O16 - DPF: {1663ed61-23eb-11d2-b92f-008048fdd814} (MeadCo ScriptX Advanced) - https://www3.eleadcrm.com/evo2/fresh...ation/smsx.cab
O16 - DPF: {200B3EE9-7242-4EFD-B1E4-D97EE825BA53} (VerifyGMN Class) - http://h20270.www2.hp.com/ediags/gmn...taller_gmn.cab
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (Installation Support) - C:\Program Files\Yahoo!\Common\Yinsthelper.dll
O16 - DPF: {49232000-16E4-426C-A231-62846947304B} (SysData Class) - https://wimpro.cce.hp.com/ChatEntry/...ds/sysinfo.cab
O16 - DPF: {4C39376E-FA9D-4349-BACC-D305C1750EF3} (EPUImageControl Class) - http://tools.ebayimg.com/eps/wl/acti..._v1-0-3-48.cab
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5} (Symantec RuFSI Utility Class) - http://security.symantec.com/sscv6/S.../bin/cabsa.cab
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://update.microsoft.com/microsof...?1164731403000
O16 - DPF: {97BB6657-DC7F-4489-9067-51FAB9D8857E} (CWebLaunchCtl Object) - https://control.everdream.com/cf1liv...weblaunch2.cab
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/ge...sh/swflash.cab
O16 - DPF: {E06E2E99-0AA1-11D4-ABA6-0060082AA75C} (GpcContainer Class) - https://themeetingson.webex.com/clie...ex/ieatgpc.cab
O23 - Service: Creative Audio Engine Licensing Service - Creative Labs - C:\Program Files\Common Files\Creative Labs Shared\Service\CTAELicensing.exe
O23 - Service: Creative Labs Licensing Service - Creative Labs - C:\Program Files\Common Files\Creative Labs Shared\Service\CreativeLicensing.exe
O23 - Service: Creative Service for CDROM Access - Creative Technology Ltd - C:\WINDOWS\system32\CTsvcCDA.exe
O23 - Service: Creative Audio Service (CTAudSvcService) - Creative Technology Ltd - C:\Program Files\Creative\Shared Files\CTAudSvc.exe
O23 - Service: GEARSecurity - GEAR Software - C:\WINDOWS\System32\GEARSec.exe
O23 - Service: Google Update Service (gupdate1c9a7fe50862e34) (gupdate1c9a7fe50862e34) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Intel(R) Matrix Storage Event Monitor (IAANTMON) - Intel Corporation - C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\1150\Intel 32\IDriverT.exe
O23 - Service: McciCMService - Motive Communications, Inc. - C:\Program Files\Common Files\Motive\McciCMService.exe
O23 - Service: NVIDIA Display Driver Service (NVSvc) - NVIDIA Corporation - C:\WINDOWS\system32\nvsvc32.exe
O23 - Service: Pml Driver HPZ12 - HP - C:\WINDOWS\system32\HPZipm12.exe
O23 - Service: Roxio UPnP Renderer 9 - Sonic Solutions - C:\Program Files\Common Files\Sonic Shared\RoxioUPnPRenderer9.exe
O23 - Service: Roxio Upnp Server 9 - Sonic Solutions - C:\Program Files\Common Files\Sonic Shared\RoxioUpnpService9.exe
O23 - Service: LiveShare P2P Server 9 (RoxLiveShare9) - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxLiveShare9.exe
O23 - Service: RoxMediaDB9 - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe
O23 - Service: Roxio Hard Drive Watcher 9 (RoxWatch9) - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxWatch9.exe
O23 - Service: stllssvr - MicroVision Development, Inc. - C:\Program Files\Common Files\SureThing Shared\stllssvr.exe
O23 - Service: Yahoo! Updater (YahooAUService) - Yahoo! Inc. - C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
--
End of file - 14899 bytes
-
-

There are some nasty infections going around that will prevent security programs from working, after your clean things should work normally.
Open HijackThis > Do a System Scan Only, close your browser and all open windows including this one, the only program or window you should have open is HijackThis, check the following entries and click on Fix Checked.
O1 - Hosts: 74.125.45.100 test1111.com
O1 - Hosts: 74.125.45.100 test1112.com
O1 - Hosts: 74.125.45.100 4-open-davinci.com
O1 - Hosts: 74.125.45.100 securitysoftwarepayments.com
O1 - Hosts: 74.125.45.100 privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 secure.privatesecuredpayments.com
O1 - Hosts: 74.125.45.100 getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.getantivirusplusnow.com
O1 - Hosts: 74.125.45.100 www.secure-plus-payments.com
O1 - Hosts: 74.125.45.100 www.securesoftwarebill.com
O1 - Hosts: 206.53.61.77 google.ae
O1 - Hosts: 206.53.61.77 google.as
O1 - Hosts: 206.53.61.77 google.at
O1 - Hosts: 206.53.61.77 google.az
O1 - Hosts: 206.53.61.77 google.ba
O1 - Hosts: 206.53.61.77 google.be
O1 - Hosts: 206.53.61.77 google.bg
O1 - Hosts: 206.53.61.77 google.bs
O1 - Hosts: 206.53.61.77 google.ca
O1 - Hosts: 206.53.61.77 google.cd
O1 - Hosts: 206.53.61.77 google.com.gh
O1 - Hosts: 206.53.61.77 google.com.hk
O1 - Hosts: 206.53.61.77 google.com.jm
O1 - Hosts: 206.53.61.77 google.com.mx
O1 - Hosts: 206.53.61.77 google.com.my
O1 - Hosts: 206.53.61.77 google.com.na
O1 - Hosts: 206.53.61.77 google.com.nf
O1 - Hosts: 206.53.61.77 google.com.ng
O1 - Hosts: 206.53.61.77 google.ch
O1 - Hosts: 206.53.61.77 google.com.np
O1 - Hosts: 206.53.61.77 google.com.pr
O1 - Hosts: 206.53.61.77 google.com.qa
O1 - Hosts: 206.53.61.77 google.com.sg
O1 - Hosts: 206.53.61.77 google.com.tj
O1 - Hosts: 206.53.61.77 google.com.tw
O1 - Hosts: 206.53.61.77 google.dj
O1 - Hosts: 206.53.61.77 google.de
O1 - Hosts: 206.53.61.77 google.dk
O1 - Hosts: 206.53.61.77 google.dm
O1 - Hosts: 206.53.61.77 google.ee
O1 - Hosts: 206.53.61.77 google.fi
O1 - Hosts: 206.53.61.77 google.fm
O1 - Hosts: 206.53.61.77 google.fr
O1 - Hosts: 206.53.61.77 google.ge
O1 - Hosts: 206.53.61.77 google.gg
O1 - Hosts: 206.53.61.77 google.gm
O1 - Hosts: 206.53.61.77 google.gr
O1 - Hosts: 206.53.61.77 google.ht
O1 - Hosts: 206.53.61.77 google.ie
O1 - Hosts: 206.53.61.77 google.im
O1 - Hosts: 206.53.61.77 google.in
O1 - Hosts: 206.53.61.77 google.it
O1 - Hosts: 206.53.61.77 google.ki
O1 - Hosts: 206.53.61.77 google.la
O1 - Hosts: 206.53.61.77 google.li
O1 - Hosts: 206.53.61.77 google.lv
O1 - Hosts: 206.53.61.77 google.ma
O1 - Hosts: 206.53.61.77 google.ms
O1 - Hosts: 206.53.61.77 google.mu
O1 - Hosts: 206.53.61.77 google.mw
O1 - Hosts: 206.53.61.77 google.nl
O1 - Hosts: 206.53.61.77 google.no
O1 - Hosts: 206.53.61.77 google.nr
O1 - Hosts: 206.53.61.77 google.nu
O1 - Hosts: 206.53.61.77 google.pl
O1 - Hosts: 206.53.61.77 google.pn
O1 - Hosts: 206.53.61.77 google.pt
O1 - Hosts: 206.53.61.77 google.ro
O1 - Hosts: 206.53.61.77 google.ru
O1 - Hosts: 206.53.61.77 google.rw
O1 - Hosts: 206.53.61.77 google.sc
O1 - Hosts: 206.53.61.77 google.se
O1 - Hosts: 206.53.61.77 google.sh
O1 - Hosts: 206.53.61.77 google.si
O1 - Hosts: 206.53.61.77 google.sm
O1 - Hosts: 206.53.61.77 google.sn
O1 - Hosts: 206.53.61.77 google.st
O1 - Hosts: 206.53.61.77 google.tl
O1 - Hosts: 206.53.61.77 google.tm
O1 - Hosts: 206.53.61.77 google.tt
O1 - Hosts: 206.53.61.77 google.us
O1 - Hosts: 206.53.61.77 google.vu
O1 - Hosts: 206.53.61.77 google.ws
O1 - Hosts: 206.53.61.77 google.co.ck
O1 - Hosts: 206.53.61.77 google.co.id
O1 - Hosts: 206.53.61.77 google.co.il
O1 - Hosts: 206.53.61.77 google.co.in
O1 - Hosts: 206.53.61.77 google.co.jp
O1 - Hosts: 206.53.61.77 google.co.kr
O1 - Hosts: 206.53.61.77 google.co.ls
O1 - Hosts: 206.53.61.77 google.co.ma
O1 - Hosts: 206.53.61.77 google.co.nz
O1 - Hosts: 206.53.61.77 google.co.tz
O1 - Hosts: 206.53.61.77 google.co.ug
O1 - Hosts: 206.53.61.77 google.co.uk
O1 - Hosts: 206.53.61.77 google.co.za
O1 - Hosts: 206.53.61.77 google.co.zm
O1 - Hosts: 206.53.61.77 google.com
O1 - Hosts: 206.53.61.77 google.com.af
O1 - Hosts: 206.53.61.77 google.com.ag
O6 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
Open up HostXpert and up at the very top left you will see an option to Make Writable, if it says Read Only then click it and it will change to Make Writable. Then see if you can run it.
Run ATF Cleaner if you have not done so already, then run this next program
Installing the Recovery Console will come in handy if your system ever becomes corrupted so this is your call to install it
Download ComboFix from one of these locations:
Link 1
Link 2
Link 3
* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:
Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply along with a New Hijackthis log.
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
-
 ComboFix Log
ComboFix Log
Hi Ken,
looks like the Host File Restore worked this time...
Here is the ComboFix file paste:
ComboFix 09-06-25.07 - Benjamin Hellmoldt 06/26/2009 10:21.1 - NTFSx86
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.3070.2629 [GMT -7:00]
Running from: c:\documents and settings\Benjamin Hellmoldt\Desktop\ComboFix.exe
AV: Fast Antivirus 2009 *On-access scanning enabled* (Updated) {E93D42AE-0531-44A3-B895-384BC873656F}
FW: Fast Antivirus 2009 *enabled* {B92B3569-4759-4CBE-BEAF-27EF8D1D6363}
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\program files\INSTALL.LOG
c:\windows\system32\_000006_.tmp.dll
c:\windows\system32\_000007_.tmp.dll
c:\windows\system32\_000008_.tmp.dll
c:\windows\system32\_000011_.tmp.dll
c:\windows\system32\_000012_.tmp.dll
.
((((((((((((((((((((((((( Files Created from 2009-05-26 to 2009-06-26 )))))))))))))))))))))))))))))))
.
2009-06-26 16:04 . 2009-06-26 16:04 -------- d-----w- c:\docume~1\BENJAM~1\APPLIC~1\Malwarebytes
2009-06-26 16:04 . 2009-06-17 18:27 38160 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-06-26 16:04 . 2009-06-26 16:09 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-06-26 16:04 . 2009-06-26 16:04 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2009-06-26 16:04 . 2009-06-17 18:27 19096 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-06-26 05:16 . 2009-06-26 05:16 -------- d-----w- c:\documents and settings\All Users\Application Data\Downloaded Installations
2009-06-25 17:33 . 2009-06-25 17:33 -------- d-----w- c:\program files\ERUNT
2009-06-25 16:48 . 2009-06-25 16:48 -------- d-----w- c:\program files\Trend Micro
2009-06-25 14:55 . 2009-06-25 15:35 -------- d-----w- c:\docume~1\BENJAM~1\APPLIC~1\Auslogics
2009-06-25 14:54 . 2009-06-25 14:54 -------- d-----w- c:\program files\Auslogics
2009-06-25 13:43 . 2009-06-25 13:44 -------- d-----w- c:\program files\Spybot - Search & Destroy
2009-06-25 13:43 . 2009-06-25 13:44 -------- d-----w- c:\documents and settings\All Users\Application Data\Spybot - Search & Destroy
2009-06-25 13:09 . 2009-06-25 13:09 -------- d-----w- c:\documents and settings\Pat Fife\Application Data\Motive
2009-06-25 13:09 . 2009-06-25 13:09 -------- d-sh--w- c:\documents and settings\Pat Fife\IETldCache
2009-06-22 19:21 . 2009-06-24 15:46 -------- d-----w- c:\documents and settings\All Users\Application Data\Norton
2009-06-22 19:06 . 2009-06-22 19:21 -------- d-----w- c:\documents and settings\All Users\Application Data\NortonInstaller
2009-06-22 19:03 . 2009-06-22 19:10 -------- d-----w- c:\docume~1\BENJAM~1\APPLIC~1\GetRightToGo
2009-06-19 23:44 . 2009-06-19 23:44 -------- d-sh--w- c:\documents and settings\All Users\Application Data\SysFld
2009-06-19 23:44 . 2009-06-25 18:31 2105344 ----a-w- c:\documents and settings\All Users\Application Data\6af99e6\EX6af9.exe
2009-06-19 23:44 . 2009-06-21 17:42 -------- d-sh--w- c:\documents and settings\All Users\Application Data\6af99e6
2009-06-19 14:22 . 2009-06-19 14:22 -------- d-----w- c:\documents and settings\Benjamin Hellmoldt\Local Settings\Application Data\assembly
2009-06-19 14:21 . 2009-06-19 14:22 -------- d-----w- c:\program files\Virtual Earth 3D
2009-06-10 12:52 . 2009-04-30 21:22 12800 ----a-w- c:\windows\system32\dllcache\xpshims.dll
2009-06-10 12:52 . 2009-04-30 21:22 246272 ----a-w- c:\windows\system32\dllcache\ieproxy.dll
2009-06-02 12:37 . 2008-02-04 17:27 102400 ----a-w- c:\windows\system32\cttele32.dll
2009-06-02 12:37 . 2009-06-02 12:37 -------- d-----w- c:\program files\OpenAL
2009-06-02 12:37 . 2008-10-08 08:21 72728 ----a-w- c:\windows\system32\{EF7AEA4C-EC87-45fd-A909-47D0136316DE}##CTHWIUT.SYS
2009-06-02 12:37 . 2008-10-08 08:21 171032 ----a-w- c:\windows\system32\{EF7AEA4C-EC87-45fd-A909-47D0136316DE}##CT20XUT.SYS
2009-06-02 12:33 . 2008-09-25 22:40 20888640 ----a-w- c:\windows\system32\AppSetup.exe
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-06-25 18:53 . 2006-11-16 07:18 1052672 ----a-w- c:\windows\system32\stlang.dll
2009-06-25 18:51 . 2006-11-16 06:58 20480 ----a-w- c:\windows\MBDEF.EXE
2009-06-25 18:50 . 2004-08-11 23:24 49152 ----a-w- c:\windows\Help\SBSI\Training\usersid.exe
2009-06-25 18:50 . 2004-08-11 23:24 233472 ----a-w- c:\windows\Help\SBSI\Training\ounins32_s.exe
2009-06-25 18:50 . 2005-05-12 07:36 12288 ----a-w- c:\windows\Fonts\RandFont.dll
2009-06-25 18:49 . 2005-08-07 22:10 16384 ----a-w- c:\windows\CTHELPER.EXE
2009-06-25 18:37 . 2008-11-18 13:38 262144 ----a-w- C:\ntuser.dat
2009-06-25 18:34 . 2008-04-03 02:36 110592 ----a-w- c:\documents and settings\Ellen Hellmoldt\Application Data\U3\temp\cleanup.exe
2009-06-25 18:34 . 2008-04-03 02:22 3096576 ---ha-w- c:\documents and settings\Ellen Hellmoldt\Application Data\U3\temp\Launchpad Removal.exe
2009-06-25 18:31 . 2005-09-20 18:04 6709248 ----a-w- c:\documents and settings\All Users\Application Data\WildTangent\Dell Game Console\Downloads\Installers\{3C48F877-A164-45E9-B9DA-26A049FFC207}.exe
2009-06-24 19:31 . 2009-03-18 19:18 -------- d-----w- c:\program files\Google
2009-06-24 15:46 . 2006-11-16 07:25 -------- d-----w- c:\program files\Common Files\Symantec Shared
2009-06-22 19:13 . 2007-12-09 21:39 -------- d-----w- c:\documents and settings\All Users\Application Data\Symantec
2009-06-14 17:25 . 2006-12-13 15:19 -------- d-----w- c:\docume~1\BENJAM~1\APPLIC~1\Roxio
2009-06-10 13:59 . 2006-11-16 07:34 -------- d-----w- c:\program files\Microsoft Works
2009-06-02 12:37 . 2006-11-16 07:21 -------- d--h--w- c:\program files\InstallShield Installation Information
2009-06-02 12:37 . 2006-11-28 17:23 -------- d-----w- c:\documents and settings\All Users\Application Data\Creative
2009-06-02 12:37 . 2006-11-28 17:27 444952 ----a-w- c:\windows\system32\wrap_oal.dll
2009-06-02 12:37 . 2006-11-16 06:58 109080 ----a-w- c:\windows\system32\OpenAL32.dll
2009-05-23 13:16 . 2009-05-23 13:16 -------- d-----w- c:\documents and settings\All Users\Application Data\PassMark
2009-05-13 05:15 . 2004-08-11 23:00 915456 ----a-w- c:\windows\system32\wininet.dll
2009-05-07 15:32 . 2004-08-11 23:00 345600 ----a-w- c:\windows\system32\localspl.dll
2009-04-17 12:26 . 2004-08-11 23:00 1847168 ----a-w- c:\windows\system32\win32k.sys
2009-04-15 14:51 . 2004-08-11 23:00 585216 ----a-w- c:\windows\system32\rpcrt4.dll
2007-05-21 02:53 . 2006-12-24 15:35 88 --sh--r- c:\windows\system32\D0CB389E8B.sys
2007-05-21 02:53 . 2006-12-24 15:35 3350 --sha-w- c:\windows\system32\KGyGaAvL.sys
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"Creative Detector"="c:\program files\Creative\MediaSource\Detector\CTDetect.exe" [2004-12-03 102400]
"ctfmon.exe"="c:\windows\system32\ctfmon.exe" [2008-04-14 15360]
"Search Protection"="c:\program files\Yahoo!\Search Protection\SearchProtection.exe" [2008-10-07 111856]
"YSearchProtection"="c:\program files\Yahoo!\Search Protection\SearchProtection.exe" [2008-10-07 111856]
"Google Update"="c:\documents and settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe" [2009-03-23 133104]
"Auslogics BoostSpeed 4"="c:\program files\Auslogics\Auslogics BoostSpeed\boostspeed.exe" [2009-03-16 362096]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
"<NO NAME>"="c:\program files\Internet Explorer\iexplore.exe" [2009-03-08 638816]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2009-06-25 7323648]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 8.0\Reader\Reader_sl.exe" [2008-10-15 39792]
"ATT-SST_McciTrayApp"="c:\program files\ATT-SST\McciTrayApp.exe" [2008-09-19 1529856]
"BellSouthWCC_McciTrayApp"="c:\program files\BellSouthWCC\McciTrayApp.exe" [2006-03-10 543232]
"HP Software Update"="c:\program files\HP\HP Software Update\HPWuSchd2.exe" [2007-05-08 54840]
"CTxfiHlp"="CTXFIHLP.EXE" - c:\windows\system32\Ctxfihlp.exe [2008-10-08 23552]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
Service Manager.lnk - c:\program files\Microsoft SQL Server\80\Tools\Binn\sqlmangr.exe [2005-5-3 81920]
[HKEY_CURRENT_USER\software\microsoft\windows\currentversion\policies\explorer]
"NoViewOnDrive"= 0 (0x0)
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Digital Imaging Monitor.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Digital Imaging Monitor.lnk
backup=c:\windows\pss\HP Digital Imaging Monitor.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Image Zone Fast Start.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Image Zone Fast Start.lnk
backup=c:\windows\pss\HP Image Zone Fast Start.lnkCommon Startup
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring]
"DisableMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\SymantecAntiVirus]
"DisableMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\SymantecFirewall]
"DisableMonitoring"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqtra08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqste08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpofxm08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposfx08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposid01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqscnvw.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqkygrp.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqCopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpfccopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpzwiz01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqPhUnl.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqDIA.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpoews01.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Common Files\\Sonic Shared\\RoxioUPnPRenderer9.exe"=
"c:\\Program Files\\Roxio\\Audio Master 9\\MusicDiscCreator9.exe"=
"c:\\Program Files\\Yahoo!\\Messenger\\YahooMessenger.exe"=
"c:\\Program Files\\Yahoo!\\Messenger\\YServer.exe"=
"c:\\Program Files\\Messenger\\msmsgs.exe"=
"c:\\Program Files\\Autech\\Kelly-Moore Click & Paint v3\\Paint.exe"=
R3 CT20XUT.SYS;CT20XUT.SYS;c:\windows\system32\drivers\CT20XUT.sys [10/8/2008 1:21 AM 171032]
R3 CTEXFIFX.SYS;CTEXFIFX.SYS;c:\windows\system32\drivers\CTEXFIFX.sys [10/8/2008 1:21 AM 1324056]
R3 CTHWIUT.SYS;CTHWIUT.SYS;c:\windows\system32\drivers\CTHWIUT.sys [10/8/2008 1:21 AM 72728]
S2 gupdate1c9a7fe50862e34;Google Update Service (gupdate1c9a7fe50862e34);c:\program files\Google\Update\GoogleUpdate.exe [3/18/2009 12:18 PM 133104]
S3 Creative Audio Engine Licensing Service;Creative Audio Engine Licensing Service;c:\program files\Common Files\Creative Labs Shared\Service\CTAELicensing.exe [6/2/2009 5:36 AM 79360]
S3 CT20XUT;CT20XUT;c:\windows\system32\drivers\CT20XUT.sys [10/8/2008 1:21 AM 171032]
S3 CTEXFIFX;CTEXFIFX;c:\windows\system32\drivers\CTEXFIFX.sys [10/8/2008 1:21 AM 1324056]
S3 CTHWIUT;CTHWIUT;c:\windows\system32\drivers\CTHWIUT.sys [10/8/2008 1:21 AM 72728]
S3 OlCamudp;OLYMPUS Digital Camera;c:\windows\system32\drivers\olcamudp.sys [2/24/2007 7:10 AM 10379]
S3 PLCMPR5;PLCMPR5 NDIS Protocol Driver;\??\c:\windows\system32\PLCMPR5.SYS --> c:\windows\system32\PLCMPR5.SYS [?]
S3 PLCNDIS5;PLCNDIS5 NDIS Protocol Driver;c:\windows\system32\PLCNDIS5.SYS [1/25/2007 6:41 PM 17280]
S3 SBRE;SBRE;\??\c:\windows\system32\drivers\SBREdrv.sys --> c:\windows\system32\drivers\SBREdrv.sys [?]
[HKEY_LOCAL_MACHINE\software\microsoft\active setup\installed components\>{60B49E34-C7CC-11D0-8953-00A0C90347FF}]
"c:\windows\system32\rundll32.exe" "c:\windows\system32\iedkcs32.dll",BrandIEActiveSetup SIGNUP
.
Contents of the 'Scheduled Tasks' folder
2009-06-26 c:\windows\Tasks\GoogleUpdateTaskMachine.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-03-18 19:18]
2009-06-26 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-4253714937-3508310156-4223063404-1006.job
- c:\documents and settings\Benjamin Hellmoldt\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2009-03-23 14:14]
2009-06-26 c:\windows\Tasks\User_Feed_Synchronization-{DF6DC8AC-E099-451A-87ED-3C500D5CB567}.job
- c:\windows\system32\msfeedssync.exe [2006-10-17 11:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.yahoo.com/
mSearch Bar = hxxp://us.rd.yahoo.com/customize/ie/defaults/sb/msgr8/*http://www.yahoo.com/ext/search/search.html
uInternet Settings,ProxyOverride = 127.0.0.1
uSearchURL,(Default) = hxxp://us.rd.yahoo.com/customize/ie/defaults/su/msgr8/*http://www.yahoo.com
IE: E&xport to Microsoft Excel - c:\progra~1\MI1933~1\OFFICE11\EXCEL.EXE/3000
Trusted Zone: eleadcrm.com\www
Trusted Zone: eleadcrm.com\www3
Trusted Zone: motive.com\patttbc.att
Trusted Zone: musicmatch.com\online
DPF: Microsoft XML Parser for Java - file:///C:/WINDOWS/Java/classes/xmldso.cab
DPF: vzTCPConfig - hxxp://www.verizon.net/checkmypc/fios/includes/vzTCPConfig.CAB
DPF: {97BB6657-DC7F-4489-9067-51FAB9D8857E} - hxxps://control.everdream.com/cf1live/static/weblaunch/weblaunch2.cab
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-06-26 10:22
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
CTxfiHlp = CTXFIHLP.EXE?
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-4253714937-3508310156-4223063404-1006\Software\Microsoft\SystemCertificates\AddressBook*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
.
Completion time: 2009-06-26 10:24
ComboFix-quarantined-files.txt 2009-06-26 17:23
Pre-Run: 155,000,836,096 bytes free
Post-Run: 155,073,318,912 bytes free
WindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(2)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
multi(0)disk(0)rdisk(0)partition(2)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect
203 --- E O F --- 2009-06-10 14:01
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules