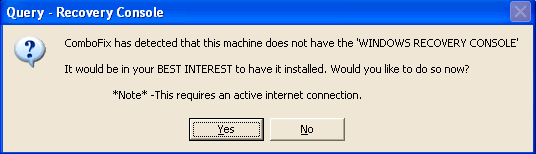
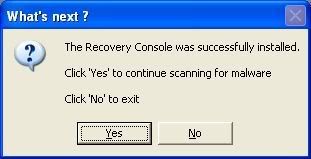
Hello and happy new year.
I've been infected with Virtumonde, Virtumonde.generic, and SmitFraud. They are pernicious buggers: I have used both spybot and symantec to clean up my machine, but the infections have always come back.
I have identified a dll file in my system32 folder, which is associated with the infection, but I can't remove it manually because it is associated with the explorer.exe and winlogon.exe processes.
The hijackthis log is below.
Thank you so much for your help and patience.
******************
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 11:10:57 AM, on 1/1/2009
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP3 (6.00.2900.5512)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\Program Files\Common Files\Symantec Shared\ccSetMgr.exe
C:\Program Files\Common Files\Symantec Shared\ccEvtMgr.exe
C:\WINDOWS\System32\WLTRYSVC.EXE
C:\WINDOWS\System32\bcmwltry.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Symantec AntiVirus\DefWatch.exe
C:\Program Files\Dell\QuickSet\NICCONFIGSVC.exe
C:\Program Files\Symantec AntiVirus\SavRoam.exe
C:\Program Files\Symantec AntiVirus\Rtvscan.exe
C:\WINDOWS\system32\wscntfy.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Apoint\Apoint.exe
C:\WINDOWS\system32\DSentry.exe
C:\WINDOWS\system32\WLTRAY.exe
C:\Program Files\Common Files\Symantec Shared\ccApp.exe
C:\PROGRA~1\SYMANT~1\VPTray.exe
C:\Program Files\Apoint\HidFind.exe
C:\Program Files\Apoint\Apntex.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\WINDOWS\system32\rundll32.exe
C:\WINDOWS\system32\rundll32.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.princeton.edu/
O4 - HKLM\..\Run: [Apoint] C:\Program Files\Apoint\Apoint.exe
O4 - HKLM\..\Run: [DVDSentry] C:\WINDOWS\system32\DSentry.exe
O4 - HKLM\..\Run: [Broadcom Wireless Manager UI] C:\WINDOWS\system32\WLTRAY.exe
O4 - HKLM\..\Run: [ccApp] "C:\Program Files\Common Files\Symantec Shared\ccApp.exe"
O4 - HKLM\..\Run: [vptray] C:\PROGRA~1\SYMANT~1\VPTray.exe
O4 - HKLM\..\Run: [SpybotSnD] "C:\Program Files\Spybot - Search & Destroy\SpybotSD.exe"
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~2\Office10\EXCEL.EXE/3000
O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_08\bin\ssv.dll
O9 - Extra 'Tools' menuitem: Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.5.0_08\bin\ssv.dll
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O16 - DPF: {01113300-3E00-11D2-8470-0060089874ED} (Support.com Configuration Class) - https://activatemydsl.verizon.net/sd...0Installer.cab
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://update.microsoft.com/windowsu...?1126734610611
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://www.update.microsoft.com/micr...?1217348810272
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: Domain = princeton.edu
O17 - HKLM\Software\..\Telephony: DomainName = princeton.edu
O17 - HKLM\System\CS1\Services\Tcpip\Parameters: Domain = princeton.edu
O18 - Filter hijack: text/html - {b71badaa-f02c-4705-b998-3ee462dbb2e6} - C:\WINDOWS\system32\mst120.dll
O23 - Service: Symantec Event Manager (ccEvtMgr) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\ccEvtMgr.exe
O23 - Service: Symantec Settings Manager (ccSetMgr) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\ccSetMgr.exe
O23 - Service: Symantec AntiVirus Definition Watcher (DefWatch) - Symantec Corporation - C:\Program Files\Symantec AntiVirus\DefWatch.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: iPodService - Apple Computer, Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: LiveUpdate - Symantec Corporation - C:\PROGRA~1\Symantec\LIVEUP~1\LUCOMS~1.EXE
O23 - Service: NICCONFIGSVC - Dell Inc. - C:\Program Files\Dell\QuickSet\NICCONFIGSVC.exe
O23 - Service: SAVRoam (SavRoam) - symantec - C:\Program Files\Symantec AntiVirus\SavRoam.exe
O23 - Service: Symantec SPBBCSvc (SPBBCSvc) - Symantec Corporation - C:\Program Files\Common Files\Symantec Shared\SPBBC\SPBBCSvc.exe
O23 - Service: Symantec AntiVirus - Symantec Corporation - C:\Program Files\Symantec AntiVirus\Rtvscan.exe
O23 - Service: Dell Wireless WLAN Tray Service (wltrysvc) - Unknown owner - C:\WINDOWS\System32\WLTRYSVC.EXE
O24 - Desktop Component 1: (no name) - C:\WINDOWS\SCI\Documentation\desktop.htm
--
End of file - 5339 bytes