-
 Virtumonde
Virtumonde
Hi,
I have 4 viruses which I am unable to remove using spybot.
Basically the sybot fixes these errors after scanning. But when I scan them again, these viruses are still to be seen.
The log file is a bit long, so I have just pasted a part of it.
The log file shows that the registry key is fixed but still it will repeat when i do the rescanning
PLZ HELP
TinyBar.C: [SBI $1BB1339D] Browser helper object (Registry key, fixed)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{6D794CB4-C7CD-4c6f-BFDC-9B77AFBDC02C}
TinyBar.C: [SBI $32F9D995] Settings (Registry value, fixed)
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks\{6D794CB4-C7CD-4c6f-BFDC-9B77AFBDC02C}
TinyBar.C: [SBI $D87CA6BD] Class ID (Registry value, fixed)
HKEY_CLASSES_ROOT\CLSID\{6D794CB4-C7CD-4c6f-BFDC-9B77AFBDC02C}\InprocServer32\=...C:\WINDOWS\SYSTEM32\yayvVLCS.dll...
TinyBar.C: [SBI $8F2A4A7E] Class ID (Registry key, fixed)
HKEY_CLASSES_ROOT\CLSID\{6D794CB4-C7CD-4c6f-BFDC-9B77AFBDC02C}
Virtumonde: [SBI $4D2BC948] Settings (Registry key, fixed)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\contim
Virtumonde: [SBI $779C9C0D] Settings (Registry key, fixed)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemoveRP
Virtumonde: [SBI $FD08B4B7] Configuration file (File, fixed)
C:\WINDOWS\system32\gQXyaGgh.ini2
Properties.size=34176
Properties.md5=FCCDBDD5F6790579FAD3A579C6C86AF3
Properties.filedate=1238860028
Properties.filedatetext=2009-04-04 19:47:08
Virtumonde: [SBI $2A2DCEAC] Configuration file (File, fixed)
C:\WINDOWS\system32\gQXyaGgh.ini
Properties.size=34786
Properties.md5=089F6F688D4F7DA2E78799800C09D786
Properties.filedate=1238860103
Properties.filedatetext=2009-04-04 19:48:22
Virtumonde.prx: [SBI $3F9F40D4] Autorun settings (48582fb9) (Registry value, fixed)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\48582fb9
Virtumonde.sci: [SBI $C49500CA] Settings (Registry key, fixed)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\yayvVLCS
--- Spybot - Search & Destroy version: 1.6.2 (build: 20090126) ---
2009-01-26 blindman.exe (1.0.0.8)
2009-01-26 SDFiles.exe (1.6.1.7)
2009-01-26 SDMain.exe (1.0.0.6)
2009-01-26 SDShred.exe (1.0.2.5)
2009-01-26 SDUpdate.exe (1.6.0.12)
2009-01-26 SpybotSD.exe (1.6.2.46)
2009-01-26 TeaTimer.exe (1.6.4.26)
2009-04-04 unins000.exe (51.49.0.0)
2009-01-26 Update.exe (1.6.0.7)
2009-01-26 advcheck.dll (1.6.2.15)
2007-04-02 aports.dll (2.1.0.0)
2008-06-14 DelZip179.dll (1.79.11.1)
2009-01-26 SDHelper.dll (1.6.2.14)
2008-06-19 sqlite3.dll
2009-01-26 Tools.dll (2.1.6.10)
2009-01-16 UninsSrv.dll (1.0.0.0)
2009-01-22 Includes\Adware.sbi (*)
2009-03-25 Includes\AdwareC.sbi (*)
2009-01-22 Includes\Cookies.sbi (*)
2009-03-31 Includes\Dialer.sbi (*)
2009-03-25 Includes\DialerC.sbi (*)
2009-01-22 Includes\HeavyDuty.sbi (*)
2009-02-10 Includes\Hijackers.sbi (*)
2009-03-03 Includes\HijackersC.sbi (*)
2009-03-17 Includes\Keyloggers.sbi (*)
2009-03-17 Includes\KeyloggersC.sbi (*)
2004-11-29 Includes\LSP.sbi (*)
2009-03-25 Includes\Malware.sbi (*)
2009-03-31 Includes\MalwareC.sbi (*)
2009-03-25 Includes\PUPS.sbi (*)
2009-03-31 Includes\PUPSC.sbi (*)
2009-01-22 Includes\Revision.sbi (*)
2009-01-13 Includes\Security.sbi (*)
2009-03-23 Includes\SecurityC.sbi (*)
2008-06-03 Includes\Spybots.sbi (*)
2008-06-03 Includes\SpybotsC.sbi (*)
2009-01-28 Includes\Spyware.sbi (*)
2009-01-28 Includes\SpywareC.sbi (*)
2009-03-25 Includes\Tracks.uti
2009-03-30 Includes\Trojans.sbi (*)
2009-03-31 Includes\TrojansC.sbi (*)
2008-03-04 Plugins\Chai.dll
2008-03-05 Plugins\Fennel.dll
2008-02-26 Plugins\Mate.dll
2007-12-24 Plugins\TCPIPAddress.dll
--- System information ---
Windows XP (Build: 2600) Service Pack 2 (5.1.2600)
/ .NETFramework / 1.1: Microsoft .NET Framework 1.1 Service Pack 1 (KB867460)
/ Windows / SP1: Microsoft Internationalized Domain Names Mitigation APIs
/ Windows / SP1: Microsoft National Language Support Downlevel APIs
/ Windows XP / SP3: Windows Installer 3.1 (KB893803)
/ Windows XP / SP3: Windows Installer 3.1 (KB893803)
/ Windows XP / SP3: Update for Windows XP (KB898461)
/ Windows XP / SP3: Hotfix for Windows XP (KB915865)
/ XML Paper Specification Shared Components Pack 1.0: XML Paper Specification Shared Components Pack 1.0
--- Startup entries list ---
Located: HK_LM:Run, Google Desktop Search
command: "C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe" /startup
file: C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
size: 29744
MD5: 6542DC2E93BCE4D4289FA70A4D367DC2
Located: HK_LM:Run, MSConfig
command: C:\WINDOWS\PCHealth\HelpCtr\Binaries\MSConfig.exe /auto
file: C:\WINDOWS\PCHealth\HelpCtr\Binaries\MSConfig.exe
size: 158208
MD5: 4FD22142F54692463A7B98B7DE175573
Located: HK_LM:Run, Network Associates Error Reporting Service
command: "C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe"
file: C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe
size: 147514
MD5: 78915C3AD0024BACD46F41BF02EE4415
Located: HK_LM:Run, ShStatEXE
command: "C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE" /STANDALONE
file: C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE
size: 90112
MD5: 29B6DCE167D45EE7C246D3552191D651
Located: HK_CU:Run, ctfmon.exe
where: S-1-5-21-484763869-776561741-725345543-1003...
command: C:\WINDOWS\system32\ctfmon.exe
file: C:\WINDOWS\system32\ctfmon.exe
size: 15360
MD5: 24232996A38C0B0CF151C2140AE29FC8
Located: HK_CU:Run, DAEMON Tools Lite
where: S-1-5-21-484763869-776561741-725345543-1003...
command: "C:\Program Files\DAEMON Tools Lite\daemon.exe" -autorun
file: C:\Program Files\DAEMON Tools Lite\daemon.exe
size: 687560
MD5: 2AC015CD0D8AA59E4AAD8EFFE29798EF
Located: HK_CU:Run, RocketDock
where: S-1-5-21-484763869-776561741-725345543-1003...
command: "C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe"
file: C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe
size: 630784
MD5: 4AC28B51530D3A93B3F27EB7A72F575F
Located: HK_CU:Run, SpybotSD TeaTimer
where: S-1-5-21-484763869-776561741-725345543-1003...
command: C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
file: C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
size: 2144088
MD5: 896A1DB9A972AD2339C2E8569EC926D1
Located: Startup (disabled), Adobe Gamma Loader (DISABLED)
command: C:\PROGRA~1\COMMON~1\Adobe\CALIBR~1\ADOBEG~1.EXE
file: C:\PROGRA~1\COMMON~1\Adobe\CALIBR~1\ADOBEG~1.EXE
size: 113664
MD5: C2FF17734176CD15221C10044EF0BA1A
Located: Startup (disabled), Adobe Reader Speed Launch (DISABLED)
command: C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
file: C:\PROGRA~1\Adobe\ACROBA~1.0\Reader\READER~1.EXE
size: 29696
MD5: DFCB9ADE94A4F8A7C42EEF41101A30AD
Located: Startup (disabled), AutoCAD Startup Accelerator (DISABLED)
command: C:\PROGRA~1\COMMON~1\AUTODE~1\ACSTAR~2.EXE
file: C:\PROGRA~1\COMMON~1\AUTODE~1\ACSTAR~2.EXE
size: 11000
MD5: AD61C37E1D1E56FAFC5FF7E3CB2D3EFA
Located: Startup (disabled), WinZip Quick Pick (DISABLED)
command: C:\PROGRA~1\WinZip\WZQKPICK.EXE
file: C:\PROGRA~1\WinZip\WZQKPICK.EXE
size: 118784
MD5: BB272E4A58C563EBF40F8CB1173DA1DA
Located: Startup (disabled), OneNote 2007 Screen Clipper and Launcher (DISABLED)
command: C:\PROGRA~1\MICROS~2\Office12\ONENOTEM.EXE /tsr
file: C:\PROGRA~1\MICROS~2\Office12\ONENOTEM.EXE
size: 98632
MD5: D91AFB6D2A0DA7539B74FB5838775D94
Located: WinLogon, crypt32chain
command: crypt32.dll
file: crypt32.dll
size: 0
MD5: D41D8CD98F00B204E9800998ECF8427E
Warning: if the file is actually larger than 0 bytes,
the checksum could not be properly calculated!
-

Hello suraj
Welcome to Safer Networking.
Please read Before You Post
That said, All advice given by anyone volunteering here, is taken at your own risk.
While best efforts are made to assist in removing infections safely, unexpected stuff can happen.
Download Trendmicros Hijackthis to your desktop.
- Double click it to install
- Follow the prompts and by default it will install in C:\Program Files\Trendmicro\Hijackthis\Highjackthis.exe
- Open HJT Scan and Save a Log File, it will open in Notepad
- Go to Format and make sure Wordwrap is Unchecked
- Go to Edit> Select All.....Edit > Copy and Paste the new log into this thread by using the Submit Reply and not start a New Thread.
DO NOT have HijackThis fix anything yet. Most of what it finds will be harmless or even required.
-

Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 8:36:43 AM, on 4/5/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.5730.0013)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\csrss.exe
C:\WINDOWS\SYSTEM32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\Program Files\Network Associates\VirusScan\Mcshield.exe
C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
C:\Program Files\Common Files\Microsoft Shared\VS7Debug\mdm.exe
C:\PROGRA~1\NETWOR~1\COMMON~1\naPrdMgr.exe
C:\Program Files\CyberLink\Shared files\RichVideo.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\wdfmgr.exe
C:\WINDOWS\system32\WebUpdateSvc.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\locator.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe
C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE
C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe
C:\Program Files\DAEMON Tools Lite\daemon.exe
C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
C:\PROGRA~1\MICROS~2\Office12\OUTLOOK.EXE
C:\WINDOWS\System32\svchost.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\Program Files\AutoCAD 2007\acad.exe
C:\Program Files\Common Files\Autodesk Shared\WSCommCntr1.exe
C:\Program Files\Microsoft Office\Office12\EXCEL.EXE
C:\Program Files\Spybot - Search & Destroy\SpybotSD.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
C:\WINDOWS\system32\wbem\wmiprvse.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = about:blank
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
F2 - REG:system.ini: UserInit=userinit.exe
O1 - Hosts: 82.98.235.133 browser-security.microsoft.com
O1 - Hosts: 82.98.235.133 url.adtrgt.com
O1 - Hosts: 82.98.235.133 best-click-scanner.info
O1 - Hosts: 82.98.235.133 antivirus-xp-pro-2009.com
O1 - Hosts: 82.98.235.133 microsoft.infosecuritycenter.com
O1 - Hosts: 82.98.235.133 microsoft.softwaresecurityhelp.com
O1 - Hosts: 82.98.235.133 onlinenotifyq.net
O1 - Hosts: 82.98.235.133 antivirusxp-pro-2009.com
O1 - Hosts: 82.98.235.133 microsoft.browser-security-center.com
O3 - Toolbar: StylerToolBar - {D2F8F919-690B-4EA2-9FA7-A203D1E04F75} - C:\Program Files\Styler\TB\StylerTB.dll
O3 - Toolbar: DAEMON Tools Toolbar - {32099AAC-C132-4136-9E9A-4E364A424E17} - C:\Program Files\DAEMON Tools Toolbar\DTToolbar.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O4 - HKLM\..\Run: [Network Associates Error Reporting Service] "C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe"
O4 - HKLM\..\Run: [ShStatEXE] "C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE" /STANDALONE
O4 - HKLM\..\Run: [Google Desktop Search] "C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe" /startup
O4 - HKLM\..\Run: [MSConfig] C:\WINDOWS\PCHealth\HelpCtr\Binaries\MSConfig.exe /auto
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [RocketDock] "C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe"
O4 - HKCU\..\Run: [DAEMON Tools Lite] "C:\Program Files\DAEMON Tools Lite\daemon.exe" -autorun
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O8 - Extra context menu item: Add to Google Photos Screensa&ver - res://C:\WINDOWS\system32\GPhotos.scr/200
O8 - Extra context menu item: Download all with Free Download Manager - file://C:\Program Files\Free Download Manager\dlall.htm
O8 - Extra context menu item: Download selected with Free Download Manager - file://C:\Program Files\Free Download Manager\dlselected.htm
O8 - Extra context menu item: Download with Free Download Manager - file://C:\Program Files\Free Download Manager\dllink.htm
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~2\Office12\EXCEL.EXE/3000
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: S&end to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~2\Office12\REFIEBAR.DLL
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra button: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O9 - Extra 'Tools' menuitem: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} (Windows Genuine Advantage Validation Tool) - http://go.microsoft.com/fwlink/?linkid=39204
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (YInstStarter Class) - C:\Program Files\Yahoo!\Common\yinsthelper.dll
O16 - DPF: {474F00F5-3853-492C-AC3A-476512BBC336} (UploadListView Class) - http://img4.orkut.com/activex/10036/photouploader.cab
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/micr...?1196686120740
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://www.update.microsoft.com/micr...?1196686106662
O16 - DPF: {745395C8-D0E1-4227-8586-624CA9A10A8D} (AxisMediaControl Class) - http://72.235.75.93:8082/activex/AMC.cab
O16 - DPF: {DE625294-70E6-45ED-B895-CFFA13AEB044} (AxisMediaControlEmb Class) - http://206.230.61.85/activex/AMC.cab
O17 - HKLM\System\CCS\Services\Tcpip\..\{5F9E34EA-EE80-4A48-93FF-790DF80D8426}: NameServer = 212.72.1.168,212.72.23.4
O18 - Protocol: grooveLocalGWS - {88FED34C-F0CA-4636-A375-3CB6248B04CD} - C:\PROGRA~1\MICROS~2\Office12\GR99D3~1.DLL
O20 - AppInit_DLLs: C:\PROGRA~1\Google\GOOGLE~4\GOEC62~1.DLL
O23 - Service: Autodesk Licensing Service - Autodesk - C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
O23 - Service: Google Desktop Manager 5.7.806.10245 (GoogleDesktopManager-061008-081103) - Google - C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
O23 - Service: Google Update Service (gupdate1c9a2501a054d4a) (gupdate1c9a2501a054d4a) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Software Updater (gusvc) - Google - C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: McAfee Framework Service (McAfeeFramework) - Network Associates, Inc. - C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
O23 - Service: Network Associates McShield (McShield) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\Mcshield.exe
O23 - Service: Network Associates Task Manager (McTaskManager) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
O23 - Service: Cyberlink RichVideo Service(CRVS) (RichVideo) - Unknown owner - C:\Program Files\CyberLink\Shared files\RichVideo.exe
O23 - Service: Web Update Service by PowerProgrammer (WebUpdate) - Data Perceptions / PowerProgrammer - C:\WINDOWS\system32\WebUpdateSvc.exe
--
End of file - 9170 bytes
-

Hi suraj,
General Telecommunications Organization Oman <--Is this your ISP?
Do this first...Important
Disable the TeaTimer, leave it disabled, do not turn it back on until we're done or it will prevent fixes from taking
- Run Spybot-S&D in Advanced Mode.
- If it is not already set to do this Go to the Mode menu select "Advanced Mode"
- On the left hand side, Click on Tools
- Then click on the Resident Icon in the List
- Uncheck "Resident TeaTimer" and OK any prompts.
- Restart your computer.<--You need to do this for it to take effect
Please do not proceed until the TeaTimer is disabled
Download the HostsXpert 4.2.0.0. - Hosts File Manager.
- Unzip HostsXpert 4.2.0.0 - Hosts File Manager to a convenient folder such as C:\HostsXpert
- Click HostsXpert.exe to Run HostsXpert - Hosts File Manager from its new home
- Click "Make Hosts Writable?" in the upper right corner (If available).
- Click Restore Microsoft's Hosts file and then click OK.
- Click the X to exit the program.
- Note: If you were using a custom Hosts file you will need to replace any of those entries yourself.
Open HijackThis > Do a System Scan Only, close your browser and all open windows including this one, the only program or window you should have open is HijackThis, check the following entries and click on Fix Checked.
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = about:blank
O3 - Toolbar: DAEMON Tools Toolbar - {32099AAC-C132-4136-9E9A-4E364A424E17} - C:\Program Files\DAEMON Tools Toolbar\DTToolbar.dll
Please download ATF Cleaner by Atribune to your desktop.
- Double-click ATF-Cleaner.exe to run the program.
- Under Main choose: Select All
- Click the Empty Selected button.
Your system may start up slower after running ATF Cleaner, this is expected but will be back to normal after the first or second boot up
Please note: If you use online banking or are registered online with any other organizations, ensure you have memorized password and other personal information as removing cookies will temporarily disable the auto-login facility.
Please download Malwarebytes' Anti-Malware from Here or Here
Double Click mbam-setup.exe to install the application.
- Make sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select "Perform Quick Scan", then click Scan.
- The scan may take some time to finish,so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected.<-- Don't forget this
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy and Paste the entire report in your next reply along with a New Hijackthis log.
Last edited by ken545; 2009-04-05 at 14:09.
-

REALLY...THANKS A LOT
But still some errors are coming during startup. Those errors dont seem to be viruses. After two reboots I have not yet been able to retrive my active desktop
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 4:54:23 PM, on 4/5/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.5730.0013)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\SYSTEM32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
C:\Program Files\Network Associates\VirusScan\Mcshield.exe
C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
C:\Program Files\Common Files\Microsoft Shared\VS7Debug\mdm.exe
C:\Program Files\CyberLink\Shared files\RichVideo.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\WebUpdateSvc.exe
C:\WINDOWS\system32\wscntfy.exe
C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe
C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE
C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe
C:\Program Files\DAEMON Tools Lite\daemon.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\explorer.exe
C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O2 - BHO: &Yahoo! Toolbar Helper - {02478D38-C3F9-4efb-9B51-7695ECA05670} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
O2 - BHO: (no name) - {2C514090-3D76-4DEC-AC2C-ADEF178D9D94} - (no file)
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\PROGRA~1\MICROS~2\Office12\GRA8E1~1.DLL
O2 - BHO: (no name) - {82C1F710-E6F3-47AB-91CE-CBAB4B33ADE9} - (no file)
O2 - BHO: Google Toolbar Notifier BHO - {AF69DE43-7D58-4638-B6FA-CE66B5AD205D} - C:\Program Files\Google\GoogleToolbarNotifier\5.1.1309.3572\swg.dll
O2 - BHO: FDMIECookiesBHO Class - {CC59E0F9-7E43-44FA-9FAA-8377850BF205} - C:\Program Files\Free Download Manager\iefdmcks.dll
O2 - BHO: SingleInstance Class - {FDAD4DA1-61A2-4FD8-9C17-86F7AC245081} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\YTSingleInstance.dll
O3 - Toolbar: StylerToolBar - {D2F8F919-690B-4EA2-9FA7-A203D1E04F75} - C:\Program Files\Styler\TB\StylerTB.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O4 - HKLM\..\Run: [Network Associates Error Reporting Service] "C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe"
O4 - HKLM\..\Run: [ShStatEXE] "C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE" /STANDALONE
O4 - HKLM\..\Run: [Google Desktop Search] "C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe" /startup
O4 - HKLM\..\Run: [MSConfig] C:\WINDOWS\PCHealth\HelpCtr\Binaries\MSConfig.exe /auto
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [RocketDock] "C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe"
O4 - HKCU\..\Run: [DAEMON Tools Lite] "C:\Program Files\DAEMON Tools Lite\daemon.exe" -autorun
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O8 - Extra context menu item: Add to Google Photos Screensa&ver - res://C:\WINDOWS\system32\GPhotos.scr/200
O8 - Extra context menu item: Download all with Free Download Manager - file://C:\Program Files\Free Download Manager\dlall.htm
O8 - Extra context menu item: Download selected with Free Download Manager - file://C:\Program Files\Free Download Manager\dlselected.htm
O8 - Extra context menu item: Download with Free Download Manager - file://C:\Program Files\Free Download Manager\dllink.htm
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~2\Office12\EXCEL.EXE/3000
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: S&end to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~2\Office12\REFIEBAR.DLL
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra button: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O9 - Extra 'Tools' menuitem: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} (Windows Genuine Advantage Validation Tool) - http://go.microsoft.com/fwlink/?linkid=39204
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (YInstStarter Class) - C:\Program Files\Yahoo!\Common\yinsthelper.dll
O16 - DPF: {474F00F5-3853-492C-AC3A-476512BBC336} (UploadListView Class) - http://img4.orkut.com/activex/10036/photouploader.cab
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/micr...?1196686120740
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://www.update.microsoft.com/micr...?1196686106662
O16 - DPF: {745395C8-D0E1-4227-8586-624CA9A10A8D} (AxisMediaControl Class) - http://72.235.75.93:8082/activex/AMC.cab
O16 - DPF: {DE625294-70E6-45ED-B895-CFFA13AEB044} (AxisMediaControlEmb Class) - http://206.230.61.85/activex/AMC.cab
O17 - HKLM\System\CCS\Services\Tcpip\..\{5F9E34EA-EE80-4A48-93FF-790DF80D8426}: NameServer = 212.72.1.168,212.72.23.4
O18 - Protocol: grooveLocalGWS - {88FED34C-F0CA-4636-A375-3CB6248B04CD} - C:\PROGRA~1\MICROS~2\Office12\GR99D3~1.DLL
O20 - AppInit_DLLs: C:\PROGRA~1\Google\GOOGLE~4\GOEC62~1.DLL
O23 - Service: Autodesk Licensing Service - Autodesk - C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
O23 - Service: Google Desktop Manager 5.7.806.10245 (GoogleDesktopManager-061008-081103) - Google - C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
O23 - Service: Google Update Service (gupdate1c9a2501a054d4a) (gupdate1c9a2501a054d4a) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Software Updater (gusvc) - Google - C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: McAfee Framework Service (McAfeeFramework) - Network Associates, Inc. - C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
O23 - Service: Network Associates McShield (McShield) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\Mcshield.exe
O23 - Service: Network Associates Task Manager (McTaskManager) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
O23 - Service: Cyberlink RichVideo Service(CRVS) (RichVideo) - Unknown owner - C:\Program Files\CyberLink\Shared files\RichVideo.exe
O23 - Service: Web Update Service by PowerProgrammer (WebUpdate) - Data Perceptions / PowerProgrammer - C:\WINDOWS\system32\WebUpdateSvc.exe
--
End of file - 8856 bytes
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
MDAM LOG FILE
Malwarebytes' Anti-Malware 1.35
Database version: 1904
Windows 5.1.2600 Service Pack 2
4/5/2009 4:32:15 PM
mbam-log-2009-04-05 (16-32-15).txt
Scan type: Quick Scan
Objects scanned: 72153
Time elapsed: 3 minute(s), 59 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 1
Registry Keys Infected: 18
Registry Values Infected: 0
Registry Data Items Infected: 5
Folders Infected: 0
Files Infected: 6
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
C:\WINDOWS\system32\hgGayXQg.dll (Trojan.Vundo.H) -> Delete on reboot.
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{82c1f710-e6f3-47ab-91ce-cbab4b33ade9} (Trojan.Vundo.H) -> Delete on reboot.
HKEY_CLASSES_ROOT\CLSID\{82c1f710-e6f3-47ab-91ce-cbab4b33ade9} (Trojan.Vundo.H) -> Delete on reboot.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{82c1f710-e6f3-47ab-91ce-cbab4b33ade9} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{3aa42713-5c1e-48e2-b432-d8bf420dd31d} (Rogue.Antivirus2008) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{2b96d5cc-c5b5-49a5-a69d-cc0a30f9028c} (Adware.Minibug) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{6d794cb4-c7cd-4c6f-bfdc-9b77afbdc02c} (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{1d4db7d2-6ec9-47a3-bd87-1e41684e07bb} (Adware.MyWebSearch) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\TypeLib\{ad8ec855-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\Interface\{ad8ec84d-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\Interface\{ad8ec850-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\Interface\{ad8ec851-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ad8ec84e-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ad8ec852-600f-11d6-aec4-0000c0a675b5} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{2137dab8-b070-11d2-ba72-0020afdd8935} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{2137dabb-b070-11d2-ba72-0020afdd8935} (Trojan.Downloader) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\rdfa (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\FCOVM (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\cs41275 (Malware.Trace) -> Quarantined and deleted successfully.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA\Notification Packages (Trojan.Vundo.H) -> Data: c:\windows\system32\hggayxqg -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA\Authentication Packages (Trojan.Vundo.H) -> Data: c:\windows\system32\hggayxqg -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\hgGayXQg.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\gQXyaGgh.ini (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\gQXyaGgh.ini2 (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\basex232.dll (Trojan.Downloader) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\basex32.dll (Trojan.Downloader) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\qoMghheE.dll (Trojan.Vundo) -> Quarantined and deleted successfully.
-

Hi,
The TeaTimer is still enabled, try disabling it again , reboot and leave it disabled.
Open HijackThis > Do a System Scan Only, close your browser and all open windows including this one, the only program or window you should have open is HijackThis, check the following entries and click on Fix Checked.
O2 - BHO: (no name) - {2C514090-3D76-4DEC-AC2C-ADEF178D9D94} - (no file)
O2 - BHO: (no name) - {82C1F710-E6F3-47AB-91CE-CBAB4B33ADE9} - (no file)
With Vundo, there could be more.
Download ComboFix from one of these locations:
Link 1
Link 2
Link 3
* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
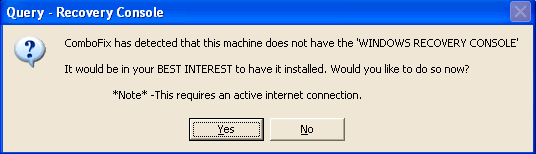
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
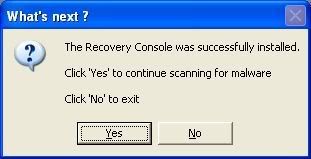
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:
Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply along with a New Hijackthis log.
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
-

Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 9:08:20 AM, on 4/9/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.6000.16791)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
C:\Program Files\Network Associates\VirusScan\Mcshield.exe
C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
C:\Program Files\Common Files\Microsoft Shared\VS7Debug\mdm.exe
C:\Program Files\CyberLink\Shared files\RichVideo.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\WebUpdateSvc.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\WINDOWS\system32\wscntfy.exe
C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe
C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE
C:\Program Files\Microsoft Office\Office12\GrooveMonitor.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe
C:\WINDOWS\system32\WgaTray.exe
C:\WINDOWS\system32\wuauclt.exe
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\WINDOWS\explorer.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
C:\Program Files\Mozilla Firefox\firefox.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page =
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O2 - BHO: &Yahoo! Toolbar Helper - {02478D38-C3F9-4efb-9B51-7695ECA05670} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\Program Files\Microsoft Office\Office12\GrooveShellExtensions.dll
O2 - BHO: Google Toolbar Notifier BHO - {AF69DE43-7D58-4638-B6FA-CE66B5AD205D} - C:\Program Files\Google\GoogleToolbarNotifier\5.1.1309.3572\swg.dll
O2 - BHO: FDMIECookiesBHO Class - {CC59E0F9-7E43-44FA-9FAA-8377850BF205} - C:\Program Files\Free Download Manager\iefdmcks.dll
O2 - BHO: SingleInstance Class - {FDAD4DA1-61A2-4FD8-9C17-86F7AC245081} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\YTSingleInstance.dll
O3 - Toolbar: StylerToolBar - {D2F8F919-690B-4EA2-9FA7-A203D1E04F75} - C:\Program Files\Styler\TB\StylerTB.dll
O3 - Toolbar: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\PROGRA~1\Yahoo!\Companion\Installs\cpn\yt.dll
O4 - HKLM\..\Run: [Network Associates Error Reporting Service] "C:\Program Files\Common Files\Network Associates\TalkBack\TBMon.exe"
O4 - HKLM\..\Run: [ShStatEXE] "C:\Program Files\Network Associates\VirusScan\SHSTAT.EXE" /STANDALONE
O4 - HKLM\..\Run: [Google Desktop Search] "C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe" /startup
O4 - HKLM\..\Run: [MSConfig] C:\WINDOWS\pchealth\helpctr\Binaries\MSCONFIG.EXE /auto
O4 - HKLM\..\Run: [GrooveMonitor] "C:\Program Files\Microsoft Office\Office12\GrooveMonitor.exe"
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [RocketDock] "C:\WINDOWS\Resources\Themes\RocketDock\RocketDock.exe"
O8 - Extra context menu item: Add to Google Photos Screensa&ver - res://C:\WINDOWS\system32\GPhotos.scr/200
O8 - Extra context menu item: Download all with Free Download Manager - file://C:\Program Files\Free Download Manager\dlall.htm
O8 - Extra context menu item: Download selected with Free Download Manager - file://C:\Program Files\Free Download Manager\dlselected.htm
O8 - Extra context menu item: Download with Free Download Manager - file://C:\Program Files\Free Download Manager\dllink.htm
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~2\Office12\EXCEL.EXE/3000
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: S&end to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~2\Office12\REFIEBAR.DLL
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra button: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O9 - Extra 'Tools' menuitem: Absolute Poker - {13C1DBF6-7535-495c-91F6-8C13714ED485} - C:\Documents and Settings\Suraj\Start Menu\Programs\Absolute Poker\Absolute Poker.lnk (file missing) (HKCU)
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} (Windows Genuine Advantage Validation Tool) - http://go.microsoft.com/fwlink/?linkid=39204
O16 - DPF: {30528230-99f7-4bb4-88d8-fa1d4f56a2ab} (YInstStarter Class) - C:\Program Files\Yahoo!\Common\yinsthelper.dll
O16 - DPF: {474F00F5-3853-492C-AC3A-476512BBC336} (UploadListView Class) - http://img4.orkut.com/activex/10036/photouploader.cab
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/micr...?1196686120740
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} (MUWebControl Class) - http://www.update.microsoft.com/micr...?1196686106662
O16 - DPF: {745395C8-D0E1-4227-8586-624CA9A10A8D} (AxisMediaControl Class) - http://72.235.75.93:8082/activex/AMC.cab
O16 - DPF: {DE625294-70E6-45ED-B895-CFFA13AEB044} (AxisMediaControlEmb Class) - http://206.230.61.85/activex/AMC.cab
O17 - HKLM\System\CCS\Services\Tcpip\..\{5F9E34EA-EE80-4A48-93FF-790DF80D8426}: NameServer = 212.72.1.168,212.72.23.4
O18 - Protocol: grooveLocalGWS - {88FED34C-F0CA-4636-A375-3CB6248B04CD} - C:\Program Files\Microsoft Office\Office12\GrooveSystemServices.dll
O23 - Service: Autodesk Licensing Service - Autodesk - C:\Program Files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
O23 - Service: Google Desktop Manager 5.7.806.10245 (GoogleDesktopManager-061008-081103) - Google - C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
O23 - Service: Google Update Service (gupdate1c9a2501a054d4a) (gupdate1c9a2501a054d4a) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Software Updater (gusvc) - Google - C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: McAfee Framework Service (McAfeeFramework) - Network Associates, Inc. - C:\Program Files\Network Associates\Common Framework\FrameworkService.exe
O23 - Service: Network Associates McShield (McShield) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\Mcshield.exe
O23 - Service: Network Associates Task Manager (McTaskManager) - Network Associates, Inc. - C:\Program Files\Network Associates\VirusScan\VsTskMgr.exe
O23 - Service: Cyberlink RichVideo Service(CRVS) (RichVideo) - Unknown owner - C:\Program Files\CyberLink\Shared files\RichVideo.exe
O23 - Service: Web Update Service by PowerProgrammer (WebUpdate) - Data Perceptions / PowerProgrammer - C:\WINDOWS\system32\WebUpdateSvc.exe
--
End of file - 8636 bytes
-

Hi,
I need to see the Combofix log.
C:\ComboFix.txt <--You can find it here
-

This thread is being closed due to lack of response,
Note: If it has been five days or more since your last post, and the helper assisting you posted a response to that post to which you did not reply, your topic will not be reopened. At that point, if you still require help, please start a new topic and include a fresh HijackThis log and a link to your previous thread.
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules