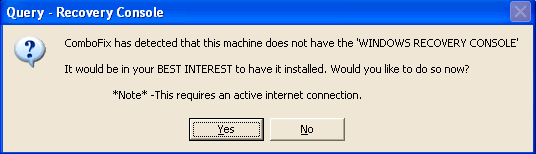
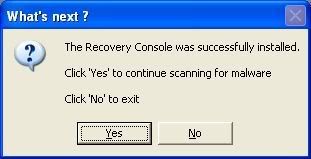
my computer has been infected with malware. below is a HJT log:
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 22:22, on 4/13/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
D:\aawservice.exe
C:\WINDOWS\system32\LEXBCES.EXE
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\system32\LEXPPS.EXE
C:\Program Files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
C:\Program Files\Bonjour\mDNSResponder.exe
C:\Program Files\ewido anti-malware\ewidoctrl.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\Program Files\Common Files\Microsoft Shared\VS7Debug\mdm.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\wscntfy.exe
C:\WINDOWS\system32\ezSP_Px.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Yahoo!\Messenger\ymsgr_tray.exe
C:\WINDOWS\system32\wuauclt.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\WINDOWS\system32\dwwin.exe
C:\Program Files\Trend Micro\HijackThis\Gamer.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://google.atcomet.com/m/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Bar = http://us.rd.yahoo.com/customize/ie/...ch/search.html
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKCU\Software\Microsoft\Internet Explorer\SearchURL,(Default) = http://us.rd.yahoo.com/customize/ie/.../www.yahoo.com
R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://www.ddcd.jp/dd3e/sony/cd/faq.html
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyServer = gate.temple.edu:8080
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = 127.0.0.1;*.local
R3 - URLSearchHook: Yahoo! Toolbar - {EF99BD32-C1FB-11D2-892F-0090271D4F88} - C:\Program Files\Yahoo!\Companion\Installs\cpn1\yt.dll
O2 - BHO: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre6\bin\ssv.dll
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O4 - HKLM\..\Run: [MSConfig] C:\WINDOWS\pchealth\helpctr\Binaries\MSCONFIG.EXE /auto
O4 - HKLM\..\Run: [ezShieldProtector for Px] C:\WINDOWS\system32\ezSP_Px.exe
O4 - HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [Yahoo! Pager] "C:\Program Files\Yahoo!\Messenger\YahooMessenger.exe" -quiet
O8 - Extra context menu item: &D&ownload &with BitComet - res://D:\Program Files\BitComet\BitComet.exe/AddLink.htm
O8 - Extra context menu item: &D&ownload all video with BitComet - res://D:\Program Files\BitComet\BitComet.exe/AddVideo.htm
O8 - Extra context menu item: &D&ownload all with BitComet - res://D:\Program Files\BitComet\BitComet.exe/AddAllLink.htm
O8 - Extra context menu item: &Google Search - res://c:\program files\google\GoogleToolbar2.dll/cmsearch.html
O8 - Extra context menu item: &Yahoo! Search - file:///C:\Program Files\Yahoo!\Common/ycsrch.htm
O8 - Extra context menu item: Backward Links - res://c:\program files\google\GoogleToolbar2.dll/cmbacklinks.html
O8 - Extra context menu item: Cached Snapshot of Page - res://c:\program files\google\GoogleToolbar2.dll/cmcache.html
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~3\Office10\EXCEL.EXE/3000
O8 - Extra context menu item: Similar Pages - res://c:\program files\google\GoogleToolbar2.dll/cmsimilar.html
O8 - Extra context menu item: Translate into English - res://c:\program files\google\GoogleToolbar2.dll/cmtrans.html
O8 - Extra context menu item: Yahoo! &Dictionary - file:///C:\Program Files\Yahoo!\Common/ycdict.htm
O8 - Extra context menu item: Yahoo! &Maps - file:///C:\Program Files\Yahoo!\Common/ycmap.htm
O8 - Extra context menu item: Yahoo! &SMS - file:///C:\Program Files\Yahoo!\Common/ycsms.htm
O9 - Extra button: BitComet - {d18a0b52-d63c-4ed0-afc6-c1e3dc1af43a} - res://D:\Program Files\BitComet\tools\BitCometBHO_1.2.8.7.dll/206 (file missing)
O14 - IERESET.INF: START_PAGE_URL=http://www.sony.com/vaiopeople
O23 - Service: Lavasoft Ad-Aware Service (aawservice) - Lavasoft - D:\aawservice.exe
O23 - Service: Apple Mobile Device - Apple Inc. - C:\Program Files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - C:\WINDOWS\system32\Ati2evxx.exe
O23 - Service: ATI Smart - Unknown owner - C:\WINDOWS\system32\ati2sgag.exe
O23 - Service: Bonjour Service - Apple Inc. - C:\Program Files\Bonjour\mDNSResponder.exe
O23 - Service: ewido security suite control - ewido networks - C:\Program Files\ewido anti-malware\ewidoctrl.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: iPod Service - Apple Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: Java Quick Starter (JavaQuickStarterService) - Sun Microsystems, Inc. - C:\Program Files\Java\jre6\bin\jqs.exe
O23 - Service: LexBce Server (LexBceS) - Lexmark International, Inc. - C:\WINDOWS\system32\LEXBCES.EXE
O23 - Service: NVIDIA Driver Helper Service (NVSvc) - NVIDIA Corporation - C:\WINDOWS\System32\nvsvc32.exe
O23 - Service: VAIO Media Music Server (VAIOMediaPlatform-MusicServer-AppServer) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Music\SSSvr.exe
O23 - Service: VAIO Media Music Server (HTTP) (VAIOMediaPlatform-MusicServer-HTTP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\SV_Httpd.exe
O23 - Service: VAIO Media Music Server (UPnP) (VAIOMediaPlatform-MusicServer-UPnP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\UPnPFramework.exe
O23 - Service: VAIO Media Photo Server (VAIOMediaPlatform-PhotoServer-AppServer) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Photo\appsrv\PhotoAppSrv.exe
O23 - Service: VAIO Media Photo Server (HTTP) (VAIOMediaPlatform-PhotoServer-HTTP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\SV_Httpd.exe
O23 - Service: VAIO Media Photo Server (UPnP) (VAIOMediaPlatform-PhotoServer-UPnP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\UPnPFramework.exe
O23 - Service: VAIO Media Video Server (VAIOMediaPlatform-VideoServer-AppServer) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Video\GPVSvr.exe
O23 - Service: VAIO Media Video Server (HTTP) (VAIOMediaPlatform-VideoServer-HTTP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\SV_Httpd.exe
O23 - Service: VAIO Media Video Server (UPnP) (VAIOMediaPlatform-VideoServer-UPnP) - Sony Corporation - C:\Program Files\Sony\VAIO Media Integrated Server\Platform\UPnPFramework.exe
--
End of file - 7487 bytes