-
 Hijacked
Hijacked
Hi, I am running a Windows Vista laptop that has been hijacked by malware. Spybot S&D was disabled. I tried to repair this programme, no luck. Tried to reinstall, no luck becasue malware won't allow me to link to Safer-Networking webistes: 'Page Load Error - website not found'. Malware has also disabled TrendMicro 2008 by same process. Have downloaded 'HijackThis', but cant get it to run. Have downloaded and installed 'mbam' but can't get it to run. Have downloaded 'gmer' and run it with the following result:
GMER 1.0.15.14972 - http://www.gmer.net
Rootkit scan 2009-07-29 21:22:02
Windows 6.0.6001 Service Pack 1
---- System - GMER 1.0.15 ----
SSDT 99455FC0 ZwCreateKey
SSDT 99455200 ZwCreateProcess
SSDT 994554C0 ZwCreateProcessEx
SSDT 99456E20 ZwCreateThread
SSDT 99456540 ZwDeleteKey
SSDT 99456800 ZwDeleteValueKey
SSDT 99457160 ZwLoadDriver
SSDT 99455A40 ZwOpenProcess
SSDT 99456280 ZwSetValueKey
SSDT 99455D00 ZwTerminateProcess
SSDT 99456C80 ZwWriteVirtualMemory
SSDT 99456FC0 ZwCreateThreadEx
SSDT 99455780 ZwCreateUserProcess
Code 8B087340 ZwEnumerateKey
Code 8B0DD2D8 ZwFlushInstructionCache
Code 8B0BF30D IofCallDriver
Code 8B0999CE IofCompleteRequest
Code 8B090305 ZwSaveKey
Code 8B08630D ZwSaveKeyEx
---- Kernel code sections - GMER 1.0.15 ----
.text ntkrnlpa.exe!IofCompleteRequest 81A55FE2 5 Bytes JMP 8B0999D3
.text ntkrnlpa.exe!ZwSaveKey 81A72664 5 Bytes JMP 8B09030A
.text ntkrnlpa.exe!ZwSaveKeyEx 81A72678 5 Bytes JMP 8B086312
.text ntkrnlpa.exe!KeSetTimerEx + 41C 81AD49E0 4 Bytes [C0, 5F, 45, 99] {RCR BYTE [EDI+0x45], 0x99}
.text ntkrnlpa.exe!KeSetTimerEx + 43C 81AD4A00 8 Bytes [00, 52, 45, 99, C0, 54, 45, ...]
.text ntkrnlpa.exe!KeSetTimerEx + 454 81AD4A18 4 Bytes [20, 6E, 45, 99] {AND [ESI+0x45], CH; CDQ }
.text ntkrnlpa.exe!KeSetTimerEx + 508 81AD4ACC 4 Bytes [40, 65, 45, 99]
.text ntkrnlpa.exe!KeSetTimerEx + 514 81AD4AD8 4 Bytes [00, 68, 45, 99] {ADD [EAX+0x45], CH; CDQ }
.text ...
.text ntkrnlpa.exe!IofCallDriver 81AD7F6F 5 Bytes JMP 8B0BF312
PAGE ntkrnlpa.exe!ZwFlushInstructionCache 81BCE30B 5 Bytes JMP 8B0DD2DC
PAGE ntkrnlpa.exe!ZwEnumerateKey 81C23BA2 5 Bytes JMP 8B087344
---- Devices - GMER 1.0.15 ----
AttachedDevice \Driver\kbdclass \Device\KeyboardClass0 Wdf01000.sys (WDF Dynamic/Microsoft Corporation)
AttachedDevice \Driver\tdx \Device\Tcp tmtdi.sys (Trend Micro TDI Driver (i386-fre)/Trend Micro Inc.)
AttachedDevice \Driver\tdx \Device\Udp tmtdi.sys (Trend Micro TDI Driver (i386-fre)/Trend Micro Inc.)
AttachedDevice \FileSystem\fastfat \Fat fltmgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
---- Disk sectors - GMER 1.0.15 ----
Disk \Device\Harddisk0\DR0 sector 01: rootkit-like behavior; copy of MBR
Disk \Device\Harddisk0\DR0 sector 02: rootkit-like behavior; copy of MBR
Disk \Device\Harddisk0\DR0 sector 03: copy of MBR
Disk \Device\Harddisk0\DR0 sector 04: rootkit-like behavior; copy of MBR
Disk \Device\Harddisk0\DR0 sector 05: copy of MBR
Disk \Device\Harddisk0\DR0 sector 06: copy of MBR
Disk \Device\Harddisk0\DR0 sector 07: rootkit-like behavior; copy of MBR
Disk \Device\Harddisk0\DR0 sector 08: copy of MBR
Disk \Device\Harddisk0\DR0 sector 09: copy of MBR
Disk \Device\Harddisk0\DR0 sector 10: copy of MBR
Disk \Device\Harddisk0\DR0 sector 11: copy of MBR
Disk \Device\Harddisk0\DR0 sector 12: copy of MBR
Disk \Device\Harddisk0\DR0 sector 13: copy of MBR
Disk \Device\Harddisk0\DR0 sector 14: copy of MBR
Disk \Device\Harddisk0\DR0 sector 15: copy of MBR
Disk \Device\Harddisk0\DR0 sector 16: copy of MBR
Disk \Device\Harddisk0\DR0 sector 17: copy of MBR
Disk \Device\Harddisk0\DR0 sector 18: copy of MBR
Disk \Device\Harddisk0\DR0 sector 19: copy of MBR
Disk \Device\Harddisk0\DR0 sector 20: copy of MBR
Disk \Device\Harddisk0\DR0 sector 21: copy of MBR
Disk \Device\Harddisk0\DR0 sector 22: copy of MBR
Disk \Device\Harddisk0\DR0 sector 23: copy of MBR
Disk \Device\Harddisk0\DR0 sector 24: copy of MBR
Disk \Device\Harddisk0\DR0 sector 25: copy of MBR
Disk \Device\Harddisk0\DR0 sector 26: copy of MBR
Disk \Device\Harddisk0\DR0 sector 27: copy of MBR
Disk \Device\Harddisk0\DR0 sector 28: copy of MBR
Disk \Device\Harddisk0\DR0 sector 29: copy of MBR
Disk \Device\Harddisk0\DR0 sector 30: copy of MBR
Disk \Device\Harddisk0\DR0 sector 31: copy of MBR
Disk \Device\Harddisk0\DR0 sector 32: copy of MBR
Disk \Device\Harddisk0\DR0 sector 33: copy of MBR
Disk \Device\Harddisk0\DR0 sector 34: copy of MBR
Disk \Device\Harddisk0\DR0 sector 35: copy of MBR
Disk \Device\Harddisk0\DR0 sector 36: copy of MBR
Disk \Device\Harddisk0\DR0 sector 37: copy of MBR
Disk \Device\Harddisk0\DR0 sector 38: copy of MBR
Disk \Device\Harddisk0\DR0 sector 39: copy of MBR
Disk \Device\Harddisk0\DR0 sector 40: copy of MBR
Disk \Device\Harddisk0\DR0 sector 41: copy of MBR
Disk \Device\Harddisk0\DR0 sector 42: copy of MBR
Disk \Device\Harddisk0\DR0 sector 43: copy of MBR
Disk \Device\Harddisk0\DR0 sector 44: copy of MBR
Disk \Device\Harddisk0\DR0 sector 45: copy of MBR
Disk \Device\Harddisk0\DR0 sector 46: copy of MBR
Disk \Device\Harddisk0\DR0 sector 47: copy of MBR
Disk \Device\Harddisk0\DR0 sector 48: copy of MBR
Disk \Device\Harddisk0\DR0 sector 49: copy of MBR
Disk \Device\Harddisk0\DR0 sector 50: copy of MBR
Disk \Device\Harddisk0\DR0 sector 51: copy of MBR
Disk \Device\Harddisk0\DR0 sector 52: copy of MBR
Disk \Device\Harddisk0\DR0 sector 53: copy of MBR
Disk \Device\Harddisk0\DR0 sector 54: copy of MBR
Disk \Device\Harddisk0\DR0 sector 55: copy of MBR
Disk \Device\Harddisk0\DR0 sector 56: copy of MBR
Disk \Device\Harddisk0\DR0 sector 57: copy of MBR
Disk \Device\Harddisk0\DR0 sector 58: copy of MBR
Disk \Device\Harddisk0\DR0 sector 59: copy of MBR
Disk \Device\Harddisk0\DR0 sector 60: copy of MBR
Disk \Device\Harddisk0\DR0 sector 61: copy of MBR
Disk \Device\Harddisk0\DR0 sector 62: copy of MBR
Disk \Device\Harddisk0\DR0 sector 63: rootkit-like behavior; copy of MBR
---- EOF - GMER 1.0.15 ----
Grateful for any advice. Scotty D
-

Hello Scotty
Welcome to Safer Networking.
Please read Before You Post
That said, All advice given by anyone volunteering here, is taken at your own risk.
While best efforts are made to assist in removing infections safely, unexpected stuff can happen.
Download Combofix from any of the links below. You must rename it before saving it. Save it to your desktop.
Link 1
Link 2
Link 3


* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
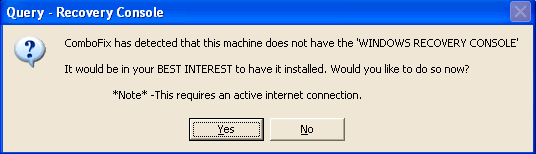
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
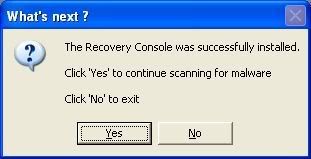
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:
Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply along with a New Hijackthis log.
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
-
 Hijacked
Hijacked
Hi, I have run Combo-fix and the following log is included:
ComboFix 09-07-29.04 - user 31/07/2009 14:09.1.2 - NTFSx86
Microsoft® Windows Vista™ Home Premium 6.0.6001.1.1252.61.1033.18.1021.415 [GMT 10:00]
Running from: c:\users\user\Desktop\Combo-Fix.exe
AV: Trend Micro Internet Security *On-access scanning disabled* (Outdated) {7D2296BC-32CC-4519-917E-52E652474AF5}
SP: Windows Defender *enabled* (Updated) {D68DDC3A-831F-4FAE-9E44-DA132C1ACF46}
* Created a new restore point
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\$recycle.bin\S-1-5-21-1723735219-730846136-2680881529-500
c:\users\user\License.v.3.346.exe
c:\windows\system32\drivers\ESQULiqtpfpsxwxjpngmqqeacsqwqmhvenbmi.sys
c:\windows\system32\drivers\ESQULwnhxcwrxmixrqpdbcteqqxerdcvptiov.sys
c:\windows\System32\ESQULjotjnnokniircexbttbyouodlcufmeft.dll
c:\windows\System32\ESQULmruhupwhymeeelcsovmxttbspfptprou.dll
c:\windows\system32\ESQULzcounter
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
-------\Service_ESQULserv.sys
-------\Service_ESQULserv.sys
((((((((((((((((((((((((( Files Created from 2009-06-28 to 2009-07-31 )))))))))))))))))))))))))))))))
.
2009-07-29 10:35 . 2009-07-13 03:36 38160 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-07-29 10:35 . 2009-07-29 10:35 -------- d-----w- c:\progra~2\Malwarebytes
2009-07-29 10:35 . 2009-07-13 03:36 19096 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-07-29 10:35 . 2009-07-29 10:43 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-07-27 08:46 . 2009-07-27 08:46 -------- d-----w- c:\windows\system32\Adobe
2009-07-22 15:17 . 2009-07-22 15:17 -------- d-----w- c:\program files\Mozilla ActiveX Control v1.7.12
2009-07-20 14:56 . 2009-07-20 14:56 -------- d-----w- c:\program files\iPod
2009-07-20 14:56 . 2009-07-20 14:57 -------- d-----w- c:\program files\iTunes
2009-07-14 14:29 . 2009-07-14 14:29 -------- d-----w- C:\Graboid
2009-07-14 13:47 . 2009-07-14 13:48 86494 ----a-w- c:\users\user\VideoLicense.v.4.312.exe
2009-07-14 13:18 . 2009-07-14 13:18 -------- d-----w- c:\users\user\AppData\Roaming\Graboid Inc
2009-07-13 15:35 . 2009-07-22 15:23 -------- d-----w- c:\users\user\AppData\Local\Graboid_Inc
2009-07-13 15:35 . 2009-07-13 15:44 -------- d-----w- c:\users\user\AppData\Local\Graboid
2009-07-13 15:35 . 2009-07-13 15:36 -------- d-----w- c:\users\user\AppData\Roaming\MozillaControl
2009-07-13 15:33 . 2009-07-29 09:01 -------- d-----w- c:\program files\VideoLAN
2009-07-13 15:32 . 2009-07-29 09:03 -------- d-----w- c:\program files\Graboid
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-07-31 04:40 . 2007-01-12 02:03 12 ----a-w- c:\windows\bthservsdp.dat
2009-07-31 03:33 . 2009-02-05 07:37 58346 ----a-w- c:\users\user\AppData\Roaming\nvModes.dat
2009-07-31 00:02 . 2009-04-27 11:14 -------- d-----w- c:\program files\Trend Micro
2009-07-29 09:34 . 2009-03-02 01:58 -------- d-----w- c:\program files\Spybot - Search & Destroy
2009-07-29 09:32 . 2009-03-02 01:58 -------- d-----w- c:\progra~2\Spybot - Search & Destroy
2009-07-20 14:56 . 2009-04-28 09:18 -------- d-----w- c:\program files\Common Files\Apple
2009-06-14 09:17 . 2009-06-14 09:16 -------- d-----w- c:\program files\QuickTime
2009-06-12 17:09 . 2007-01-12 02:49 -------- d-----w- c:\program files\Microsoft Works
2009-06-08 06:40 . 2009-06-08 06:40 0 ---ha-w- c:\windows\system32\drivers\Msft_User_WpdMtpDr_01_00_00.Wdf
2009-07-27 08:29 . 2009-04-13 13:16 134648 ----a-w- c:\program files\mozilla firefox\components\brwsrcmp.dll
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"Sidebar"="c:\program files\Windows Sidebar\sidebar.exe" [2008-01-19 1233920]
"ehTray.exe"="c:\windows\ehome\ehTray.exe" [2008-01-19 125952]
"OE"="c:\program files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe" [2009-04-27 492808]
"WMPNSCFG"="c:\program files\Windows Media Player\WMPNSCFG.exe" [2008-01-19 202240]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"Windows Defender"="c:\program files\Windows Defender\MSASCui.exe" [2008-01-19 1008184]
"SynTPEnh"="c:\program files\Synaptics\SynTP\SynTPEnh.exe" [2007-09-14 1021224]
"QPService"="c:\program files\HP\QuickPlay\QPService.exe" [2006-12-03 167936]
"QlbCtrl"="c:\program files\Hewlett-Packard\HP Quick Launch Buttons\QlbCtrl.exe" [2006-11-06 159744]
"HP Health Check Scheduler"="c:\program files\Hewlett-Packard\HP Health Check\HPHC_Scheduler.exe" [2006-12-04 46704]
"WAWifiMessage"="c:\program files\Hewlett-Packard\HP Wireless Assistant\WiFiMsg.exe" [2006-10-18 317152]
"hpWirelessAssistant"="c:\program files\Hewlett-Packard\HP Wireless Assistant\HPWAMain.exe" [2006-10-18 472800]
"SunJavaUpdateSched"="c:\program files\Java\jre1.6.0\bin\jusched.exe" [2007-01-12 77824]
"HP Software Update"="c:\program files\Hp\HP Software Update\HPWuSchd2.exe" [2007-05-08 54840]
"SynTPStart"="c:\program files\Synaptics\SynTP\SynTPStart.exe" [2007-09-14 102400]
"NvSvc"="c:\windows\system32\nvsvc.dll" [2007-02-27 90191]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2007-02-27 7770112]
"NvMediaCenter"="c:\windows\system32\NvMcTray.dll" [2007-02-27 81920]
"UfSeAgnt.exe"="c:\program files\Trend Micro\Internet Security\UfSeAgnt.exe" [2009-04-01 995528]
"QuickTime Task"="c:\program files\QuickTime\QTTask.exe" [2009-05-26 413696]
"iTunesHelper"="c:\program files\iTunes\iTunesHelper.exe" [2009-07-13 292128]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
"Launcher"="c:\windows\SMINST\launcher.exe" [2006-11-08 44128]
[HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run]
"OE"="c:\program files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe" [2009-04-27 492808]
c:\progra~2\MICROS~1\Windows\STARTM~1\Programs\Startup\
Adobe Reader Speed Launch.lnk - c:\program files\Adobe\Reader 8.0\Reader\reader_sl.exe [2006-10-23 40048]
Adobe Reader Synchronizer.lnk - c:\program files\Adobe\Reader 8.0\Reader\AdobeCollabSync.exe [2006-10-23 734872]
Microsoft Office.lnk - c:\program files\Microsoft Office\Office10\OSA.EXE [2001-2-13 83360]
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\policies\system]
"EnableUIADesktopToggle"= 0 (0x0)
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\WinDefend]
@="Service"
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"UacDisableNotify"=dword:00000001
"InternetSettingsDisableNotify"=dword:00000001
"AutoUpdateDisableNotify"=dword:00000001
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring]
"DisableMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\SymantecAntiVirus]
"DisableMonitoring"=dword:00000001
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\SymantecFirewall]
"DisableMonitoring"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\DomainProfile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\FirewallRules]
"{30A953C3-59FE-4C8D-A6A0-9E6567F3AA45}"= UDP:c:\program files\HP\QuickPlay\QP.exe:QP
"{42F778AE-2810-4BA4-BD34-7EECE5073AD2}"= TCP:c:\program files\HP\QuickPlay\QP.exe:QP
"{755DB9DE-E26E-4634-B7FB-83909D4797E9}"= UDP:c:\program files\Bonjour\mDNSResponder.exe:Bonjour
"{AF89F773-60BF-476A-B0CC-BE13C1589B1C}"= TCP:c:\program files\Bonjour\mDNSResponder.exe:Bonjour
"{42DCACAA-E192-4174-8CC2-B6325E944191}"= UDP:c:\program files\DNA\btdna.exe:DNA (TCP-In)
"{2877EA1E-21CB-4B86-AEE6-0A62EFC5A95C}"= TCP:c:\program files\DNA\btdna.exe:DNA (UDP-In)
"{1FDECB65-81CD-4FAE-8128-304D0F09390E}"= UDP:c:\program files\iTunes\iTunes.exe:iTunes
"{993F6183-FE47-4934-8EFA-D1909698024D}"= TCP:c:\program files\iTunes\iTunes.exe:iTunes
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\PublicProfile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\StandardProfile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\StandardProfile\AuthorizedApplications\List]
"c:\\Program Files\\BitTorrent\\bittorrent.exe"= c:\program files\BitTorrent\bittorrent.exe:*:Enabled:BitTorrent
R1 tmlwf;Trend Micro NDIS 6.0 Filter Driver;c:\windows\System32\drivers\tmlwf.sys [27/04/2009 9:12 PM 145424]
R2 tmevtmgr;tmevtmgr;c:\windows\System32\drivers\tmevtmgr.sys [27/04/2009 9:12 PM 50192]
R2 tmpreflt;tmpreflt;c:\windows\System32\drivers\tmpreflt.sys [27/04/2009 9:12 PM 36368]
R2 tmwfp;Trend Micro WFP Callout Driver;c:\windows\System32\drivers\tmwfp.sys [27/04/2009 9:12 PM 256528]
R3 NETw5v32;Intel(R) Wireless WiFi Link 5000 Series Adapter Driver for Windows Vista 32 Bit;c:\windows\System32\drivers\NETw5v32.sys [17/11/2008 2:40 PM 3668480]
R3 ST50220;Sonix ST50220 USB Video Camera Driver;c:\windows\System32\drivers\ST50220.sys [2/12/2008 11:26 AM 34224]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\svchost]
bthsvcs REG_MULTI_SZ BthServ
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://ie.redirect.hp.com/svs/rdr?TYPE=3&tp=iehome&locale=EN_AU&c=71&bd=Pavilion&pf=laptop
mStart Page = hxxp://ie.redirect.hp.com/svs/rdr?TYPE=3&tp=iehome&locale=EN_AU&c=71&bd=Pavilion&pf=laptop
uInternet Settings,ProxyOverride = *.local
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~3\Office10\EXCEL.EXE/3000
Handler: hiro - {50BA1131-168F-4c08-A69B-4012273F222E} - c:\program files\Hiro-Media\HiroClient\OldHiroProtocolHandler.dll
Handler: hirodownload - {77F2FF4C-CEDD-4c71-8ABF-DF7CC05EFC63} - c:\program files\Hiro-Media\HiroClient\HiroProtocolHandler.dll
FF - ProfilePath - c:\users\user\AppData\Roaming\Mozilla\Firefox\Profiles\j3s9ko54.default\
FF - prefs.js: browser.startup.homepage - hxxp://www.myspace.com/
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjava11.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjava12.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjava13.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjava14.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjava32.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npjpi160.dll
FF - plugin: c:\program files\Java\jre1.6.0\bin\npoji610.dll
FF - plugin: c:\program files\Mozilla Firefox\plugins\npbittorrent.dll
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-07-31 14:47
Windows 6.0.6001 Service Pack 1 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E96D-E325-11CE-BFC1-08002BE10318}\0000\AllUserSettings]
@Denied: (A) (Users)
@Denied: (A) (Everyone)
@Allowed: (B 1 2 3 4 5) (S-1-5-20)
"BlindDial"=dword:00000000
.
------------------------ Other Running Processes ------------------------
.
c:\windows\System32\audiodg.exe
c:\program files\Trend Micro\BM\TMBMSRV.exe
c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
c:\program files\Bonjour\mDNSResponder.exe
c:\program files\HP\QuickPlay\Kernel\TV\CLCapSvc.exe
c:\program files\Common Files\LightScribe\LSSrvc.exe
c:\program files\Trend Micro\Internet Security\SfCtlCom.exe
c:\program files\Trend Micro\Internet Security\TmProxy.exe
c:\windows\System32\drivers\XAudio.exe
c:\program files\HP\QuickPlay\Kernel\TV\CLSched.exe
c:\program files\Hewlett-Packard\Shared\hpqwmiex.exe
c:\program files\Trend Micro\Internet Security\TmPfw.exe
c:\program files\Windows Media Player\wmpnetwk.exe
c:\windows\ehome\ehmsas.exe
c:\windows\System32\rundll32.exe
c:\program files\iPod\bin\iPodService.exe
c:\program files\Hewlett-Packard\HP Health Check\HPHC_Service.exe
c:\progra~1\HEWLET~1\Shared\HPQTOA~1.EXE
.
**************************************************************************
.
Completion time: 2009-07-31 14:53 - machine was rebooted
ComboFix-quarantined-files.txt 2009-07-31 04:53
Pre-Run: 21,923,848,192 bytes free
Post-Run: 21,834,649,600 bytes free
193 --- E O F --- 2009-06-14 17:01
I AM UNABLE TO PRODUCE A HIJACKTHIS LOG AT THIS STAGE
-

Hello Scotty,
You where infected by a Rootkit that prevents most security scans from running, it sometimes blocks access to secuity sites as well. Looks like Combofix removed it.
You should be able to run these programs now , and after you run the scans than post a Hijackthis log.
Download TFC to your desktop
- Close any open windows.
- Double click the TFC icon to run the program
- TFC will close all open programs itself in order to run,
- Click the Start button to begin the process.
- Allow TFC to run uninterrupted.
- The program should not take long to finish it's job
- Once its finished it should automatically reboot your machine,
- if it doesn't, manually reboot to ensure a complete clean
Please download Malwarebytes' Anti-Malware to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.

- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected .
- When completed, a log will open in Notepad. Please save it to a convenient location and post the results.
- Note: If you receive a notice that some of the items couldn't be removed, that they have been added to the delete on reboot list, please reboot.
Post the report and also a new HJT log please
Download Trendmicros Hijackthis to your desktop.
- Double click it to install
- Follow the prompts and by default it will install in C:\Program Files\Trendmicro\Hijackthis\Highjackthis.exe
- Open HJT Scan and Save a Log File, it will open in Notepad
- Go to Format and make sure Wordwrap is Unchecked
- Go to Edit> Select All.....Edit > Copy and Paste the new log into this thread by using the Submit Reply and not start a New Thread.
DO NOT have HijackThis fix anything yet. Most of what it finds will be harmless or even required.
Run the programs, post the log from Malwarebytes and then a Hijackthis log please
-
 Hijacked
Hijacked
Hi, you were correct in that the programmes now run after Combo-fix. The 'mbam' log is as follows:
Malwarebytes' Anti-Malware 1.39
Database version: 2539
Windows 6.0.6001 Service Pack 1
1/08/2009 4:14:24 PM
mbam-log-2009-08-01 (16-14-24).txt
Scan type: Quick Scan
Objects scanned: 82666
Time elapsed: 11 minute(s), 13 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 2
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\user\VideoLicense.v.4.312.exe (Trojan.Dropper) -> Quarantined and deleted successfully.
c:\WINDOWS\Tasks\{5B57CF47-0BFA-43c6-ACF9-3B3653DCADBA}.job (Trojan.FakeAlert) -> Quarantined and deleted successfully.
THE 'HIJACKTHIS' LOG IS AS FOLLOWS:
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 4:24:13 PM, on 1/08/2009
Platform: Windows Vista SP1 (WinNT 6.00.1905)
MSIE: Internet Explorer v7.00 (7.00.6001.18294)
Boot mode: Normal
Running processes:
C:\Windows\system32\Dwm.exe
C:\Windows\Explorer.EXE
C:\Windows\system32\taskeng.exe
C:\Program Files\Trend Micro\Internet Security\UfSeAgnt.exe
C:\Program Files\Windows Defender\MSASCui.exe
C:\Program Files\Synaptics\SynTP\SynTPEnh.exe
C:\Program Files\HP\QuickPlay\QPService.exe
C:\Program Files\Hewlett-Packard\HP Quick Launch Buttons\QLBCTRL.exe
C:\Program Files\Hewlett-Packard\HP Wireless Assistant\WiFiMsg.exe
C:\Program Files\Hewlett-Packard\HP Wireless Assistant\HPWAMain.exe
C:\Program Files\Java\jre6\bin\jusched.exe
C:\Program Files\HP\HP Software Update\hpwuSchd2.exe
C:\Program Files\iTunes\iTunesHelper.exe
C:\Program Files\Windows Media Player\wmpnscfg.exe
C:\Program Files\Windows Sidebar\sidebar.exe
C:\WINDOWS\ehome\ehtray.exe
C:\Program Files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe
C:\Program Files\Adobe\Reader 8.0\Reader\reader_sl.exe
C:\PROGRA~1\HEWLET~1\Shared\HPQTOA~1.EXE
C:\WINDOWS\System32\rundll32.exe
C:\Windows\ehome\ehmsas.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\Windows\system32\wuauclt.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://ie.redirect.hp.com/svs/rdr?TY...lion&pf=laptop
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://ie.redirect.hp.com/svs/rdr?TY...lion&pf=laptop
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = *.local
R0 - HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName =
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 - BHO: (no name) - {5C255C8A-E604-49b4-9D64-90988571CECB} - (no file)
O2 - BHO: Windows Live Sign-in Helper - {9030D464-4C02-4ABF-8ECC-5164760863C6} - C:\Program Files\Common Files\Microsoft Shared\Windows Live\WindowsLiveLogin.dll
O2 - BHO: Google Toolbar Helper - {AA58ED58-01DD-4d91-8333-CF10577473F7} - c:\program files\google\googletoolbar1.dll
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O3 - Toolbar: &Google - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - c:\program files\google\googletoolbar1.dll
O4 - HKLM\..\Run: [Windows Defender] %ProgramFiles%\Windows Defender\MSASCui.exe -hide
O4 - HKLM\..\Run: [SynTPEnh] C:\Program Files\Synaptics\SynTP\SynTPEnh.exe
O4 - HKLM\..\Run: [QPService] "C:\Program Files\HP\QuickPlay\QPService.exe"
O4 - HKLM\..\Run: [QlbCtrl] %ProgramFiles%\Hewlett-Packard\HP Quick Launch Buttons\QlbCtrl.exe /Start
O4 - HKLM\..\Run: [HP Health Check Scheduler] C:\Program Files\Hewlett-Packard\HP Health Check\HPHC_Scheduler.exe
O4 - HKLM\..\Run: [WAWifiMessage] %ProgramFiles%\Hewlett-Packard\HP Wireless Assistant\WiFiMsg.exe
O4 - HKLM\..\Run: [hpWirelessAssistant] %ProgramFiles%\Hewlett-Packard\HP Wireless Assistant\HPWAMain.exe
O4 - HKLM\..\Run: [SunJavaUpdateSched] "C:\Program Files\Java\jre6\bin\jusched.exe"
O4 - HKLM\..\Run: [HP Software Update] C:\Program Files\Hp\HP Software Update\HPWuSchd2.exe
O4 - HKLM\..\Run: [SynTPStart] C:\Program Files\Synaptics\SynTP\SynTPStart.exe
O4 - HKLM\..\Run: [NvSvc] RUNDLL32.EXE C:\Windows\system32\nvsvc.dll,nvsvcStart
O4 - HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\Windows\system32\NvCpl.dll,NvStartup
O4 - HKLM\..\Run: [NvMediaCenter] RUNDLL32.EXE C:\Windows\system32\NvMcTray.dll,NvTaskbarInit
O4 - HKLM\..\Run: [UfSeAgnt.exe] "C:\Program Files\Trend Micro\Internet Security\UfSeAgnt.exe"
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\QTTask.exe" -atboottime
O4 - HKLM\..\Run: [iTunesHelper] "C:\Program Files\iTunes\iTunesHelper.exe"
O4 - HKLM\..\RunOnce: [Launcher] %WINDIR%\SMINST\launcher.exe
O4 - HKCU\..\Run: [Sidebar] C:\Program Files\Windows Sidebar\sidebar.exe /autoRun
O4 - HKCU\..\Run: [ehTray.exe] C:\Windows\ehome\ehTray.exe
O4 - HKCU\..\Run: [OE] C:\Program Files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe
O4 - HKCU\..\Run: [WMPNSCFG] C:\Program Files\Windows Media Player\WMPNSCFG.exe
O4 - HKUS\S-1-5-18\..\Run: [OE] C:\Program Files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\Run: [OE] C:\Program Files\Trend Micro\Internet Security\TMAS_OE\TMAS_OEMon.exe (User 'Default user')
O4 - Global Startup: Adobe Reader Speed Launch.lnk = C:\Program Files\Adobe\Reader 8.0\Reader\reader_sl.exe
O4 - Global Startup: Adobe Reader Synchronizer.lnk = C:\Program Files\Adobe\Reader 8.0\Reader\AdobeCollabSync.exe
O4 - Global Startup: Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office10\OSA.EXE
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~3\Office10\EXCEL.EXE/3000
O13 - Gopher Prefix:
O16 - DPF: {20A60F0D-9AFA-4515-A0FD-83BD84642501} (Checkers Class) - http://messenger.zone.msn.com/binary...r.cab56986.cab
O16 - DPF: {C3F79A2B-B9B4-4A66-B012-3EE46475B072} (MessengerStatsClient Class) - http://messenger.zone.msn.com/binary...t.cab56907.cab
O18 - Protocol: hiro - {50BA1131-168F-4C08-A69B-4012273F222E} - C:\Program Files\Hiro-Media\HiroClient\OldHiroProtocolHandler.dll
O18 - Protocol: hirodownload - {77F2FF4C-CEDD-4C71-8ABF-DF7CC05EFC63} - C:\Program Files\Hiro-Media\HiroClient\HiroProtocolHandler.dll
O23 - Service: AddFiltr - Hewlett-Packard Development Company, L.P. - C:\Program Files\Hewlett-Packard\HP Quick Launch Buttons\AddFiltr.exe
O23 - Service: Apple Mobile Device - Apple Inc. - C:\Program Files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
O23 - Service: Bonjour Service - Apple Inc. - C:\Program Files\Bonjour\mDNSResponder.exe
O23 - Service: CyberLink Background Capture Service (CBCS) (CLCapSvc) - Unknown owner - C:\Program Files\HP\QuickPlay\Kernel\TV\CLCapSvc.exe
O23 - Service: CyberLink Task Scheduler (CTS) (CLSched) - Unknown owner - C:\Program Files\HP\QuickPlay\Kernel\TV\CLSched.exe
O23 - Service: Symantec Lic NetConnect service (CLTNetCnService) - Unknown owner - c:\Program Files\Common Files\Symantec Shared\ccSvcHst.exe (file missing)
O23 - Service: HP Health Check Service - Hewlett-Packard - C:\Program Files\Hewlett-Packard\HP Health Check\hphc_service.exe
O23 - Service: hpqwmiex - Hewlett-Packard Development Company, L.P. - C:\Program Files\Hewlett-Packard\Shared\hpqwmiex.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Roxio\Roxio MyDVD Basic v9\InstallShield\Driver\1050\Intel 32\IDriverT.exe
O23 - Service: iPod Service - Apple Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: LightScribeService Direct Disc Labeling Service (LightScribeService) - Hewlett-Packard Company - C:\Program Files\Common Files\LightScribe\LSSrvc.exe
O23 - Service: RoxMediaDB9 - Sonic Solutions - C:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe
O23 - Service: Trend Micro Central Control Component (SfCtlCom) - Trend Micro Inc. - C:\Program Files\Trend Micro\Internet Security\SfCtlCom.exe
O23 - Service: stllssvr - MicroVision Development, Inc. - C:\Program Files\Common Files\SureThing Shared\stllssvr.exe
O23 - Service: Trend Micro Unauthorized Change Prevention Service (TMBMServer) - Trend Micro Inc. - C:\Program Files\Trend Micro\BM\TMBMSRV.exe
O23 - Service: Trend Micro Personal Firewall (TmPfw) - Trend Micro Inc. - C:\Program Files\Trend Micro\Internet Security\TmPfw.exe
O23 - Service: Trend Micro Proxy Service (TmProxy) - Trend Micro Inc. - C:\Program Files\Trend Micro\Internet Security\TmProxy.exe
O23 - Service: XAudioService - Conexant Systems, Inc. - C:\Windows\system32\DRIVERS\xaudio.exe
--
End of file - 8400 bytes
THANKS YOU GUYS ARE DOING A GREAT JOB
-

Hi,
Are you aware of this?
C:\Program Files\Hiro-Media <--Add supported
http://www.hiro-media.com/
Things are looking good, lets run this free online virus scanner as a doublecheck.
Please run this free online virus scanner from ESET
- Note: You will need to use Internet explorer for this scan
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Click Start
- Make sure that the option Remove found threats is ticked, and the option Scan unwanted applications is checked
- Click Scan
- Wait for the scan to finish
- Use notepad to open the logfile located at C:\Program Files\EsetOnlineScanner\log.txt
- Copy and paste that log as a reply to this topic
How is your computer behaving now?
-
 Hijacked
Hijacked
Giday,
ESET appeared to run OK and picked up another five malicious programmes. The log is as follows:
C:\Qoobox\Quarantine\C\Users\user\License.v.3.346.exe.vir a variant of Win32/Kryptik.AAL trojan deleted - quarantined
C:\Qoobox\Quarantine\C\WINDOWS\System32\ESQULjotjnnokniircexbttbyouodlcufmeft.dll.vir Win32/Olmarik.JL trojan cleaned by deleting - quarantined
C:\Qoobox\Quarantine\C\WINDOWS\System32\ESQULmruhupwhymeeelcsovmxttbspfptprou.dll.vir Win32/Olmarik.JI trojan cleaned by deleting - quarantined
C:\Users\user\Downloads\DivX.FLCodec.exe Win32/AutoRun.ABH worm deleted - quarantined
C:\Users\user\Downloads\onlinemovies.40018.exe Win32/TrojanDownloader.Agent.PGM trojan cleaned by deleting - quarantined
Thanks for the heads up about the Hiro-Media file. Do you suggest the best way to get rid of this programmes is by selecting it for deletion in HIJACKTHIS?
The computer appears to be running OK now. Thanks very much for your help in what I suspect is a relatively simple problem given the size of some of the threads.
Last edited by tashi; 2009-08-11 at 18:45.
Reason: Timestamp archive
-

Hi,
ESET Found a few things but most being in Qoobox which are backups of what Combofix removed, we will get to that in a bit.
C:\Program Files\Hiro-Media <--You should be able to uninstall this via the Add Remove Programs in the Control Panel, if you cant , let me know.
-

Hi,
- Click START then RUN
- Now type Combofix /u in the runbox and click OK. Note the space between the X and the U, it needs to be there.
- When shown the disclaimer, Select "2"
The above procedure will:- Delete the following:
- ComboFix and its associated files and folders.
- VundoFix backups, if present
- The C:\Deckard folder, if present
- The C:_OtMoveIt folder, if present
- Reset the clock settings.
- Hide file extensions, if required.
- Hide System/Hidden files, if required.
- Reset System Restore.
How are things running now??
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules