-
 Unable to run most Protection programs
Unable to run most Protection programs
I can't run spybot, Hijackthis, etc. even with renaming the file so I cannot procure a log to post in here. I'll click on the executables but they simply will not open, it triggers like it normally does but then nothing pops up. My Google site searches also redirect to other places but I've managed to deal with them for awhile using the "cache" function. I need HELP!!
-
-
 RootRepeal log
RootRepeal log
Still unable to run anything, also tried starting in safe mode, I can't even boot in safe mode, the computer will auto restart.
ROOTREPEAL (c) AD, 2007-2009
==================================================
Scan Start Time: 2009/09/08 04:54
Program Version: Version 1.3.5.0
Windows Version: Windows XP SP2
==================================================
Drivers
-------------------
Name: dump_atapi.sys
Image Path: C:\WINDOWS\System32\Drivers\dump_atapi.sys
Address: 0xF29F3000 Size: 98304 File Visible: No Signed: -
Status: -
Name: dump_WMILIB.SYS
Image Path: C:\WINDOWS\System32\Drivers\dump_WMILIB.SYS
Address: 0xF79A2000 Size: 8192 File Visible: No Signed: -
Status: -
Name: PCI_PNP3674
Image Path: \Driver\PCI_PNP3674
Address: 0x00000000 Size: 0 File Visible: No Signed: -
Status: -
Name: rootrepeal.sys
Image Path: C:\WINDOWS\system32\drivers\rootrepeal.sys
Address: 0xB9C54000 Size: 49152 File Visible: No Signed: -
Status: -
Name: spsl.sys
Image Path: spsl.sys
Address: 0xF728E000 Size: 1052672 File Visible: No Signed: -
Status: -
Name: sptd
Image Path: \Driver\sptd
Address: 0x00000000 Size: 0 File Visible: No Signed: -
Status: -
Name: win32k.sys:1
Image Path: C:\WINDOWS\win32k.sys:1
Address: 0xF77E8000 Size: 20480 File Visible: No Signed: -
Status: -
Name: win32k.sys:2
Image Path: C:\WINDOWS\win32k.sys:2
Address: 0xF7580000 Size: 61440 File Visible: No Signed: -
Status: -
SSDT
-------------------
#: 041 Function Name: NtCreateKey
Status: Hooked by "spsl.sys" at address 0xf728f0e0
#: 071 Function Name: NtEnumerateKey
Status: Hooked by "spsl.sys" at address 0xf72adca4
#: 073 Function Name: NtEnumerateValueKey
Status: Hooked by "spsl.sys" at address 0xf72ae032
#: 119 Function Name: NtOpenKey
Status: Hooked by "spsl.sys" at address 0xf728f0c0
#: 160 Function Name: NtQueryKey
Status: Hooked by "spsl.sys" at address 0xf72ae10a
#: 173 Function Name: NtQuerySystemInformation
Status: Hooked by "C:\WINDOWS\System32\Drivers\Beep.SYS" at address 0xf75a21a0
#: 177 Function Name: NtQueryValueKey
Status: Hooked by "spsl.sys" at address 0xf72adf8a
#: 247 Function Name: NtSetValueKey
Status: Hooked by "spsl.sys" at address 0xf72ae19c
==EOF==
-

Try this
Please download this tool by sUBs, and save it to your desktop.- Close any applications that you have open, as your computer will be rebooted
- Double click +++.exe to run the tool
- When it has run it will reboot your computer, you may then delete the tool
Its important that you follow these instructions and rename Combofix as this Rootkit infection will stop it from running if its not renamed.
Download Combofix from any of the links below. You must rename it before saving it. Save it to your desktop.
Link 1
Link 2
Link 3


* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
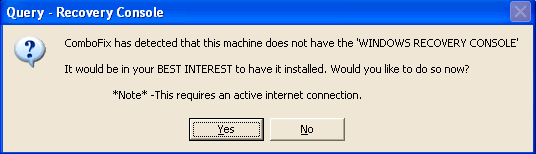
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
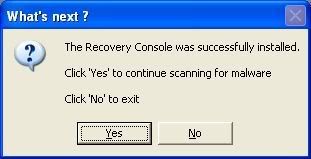
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:
Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply along with a New Hijackthis log.
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
Last edited by ken545; 2009-09-08 at 19:24.
Reason: Changed my fix
-

Unable to d/l the +++ program, the link is broken
-

Yep, it is. The problem were having is that this is a nasty rootkit , this garbage is getting more sophisticated all the time.
Follow the instructions and run Combofix renamed
-
 Combo Fix Log
Combo Fix Log
ComboFix 09-09-08.02 - HP_Owner 09/12/2009 5:41.1.1 - NTFSx86
Running from: c:\documents and settings\HP_Owner\Desktop\Combo--Fix.exe
* Created a new restore point
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\documents and settings\HP_Owner\Application Data\Microsoft\Windows\iexplorer.exe
c:\documents and settings\HP_Owner\Application Data\Microsoft\Windows\lsass.exe
c:\documents and settings\HP_Owner\Application Data\Microsoft\Windows\ms64.exe
c:\documents and settings\HP_Owner\Local Settings\Temporary Internet Files\21.tmp
C:\install.exe
c:\program files\Common Files\Real\WeatherBug\MiniBugTransporter.dll
c:\windows\braviax.exe
c:\windows\cru629.dat
c:\windows\system32\~.exe
c:\windows\system32\braviax.exe
c:\windows\system32\cru629.dat
c:\windows\system32\dllcache\beep.sys
c:\windows\system32\ps2.bat
c:\windows\system32\windows32.exe
c:\windows\system32\wisdstr.exe
Infected copy of c:\windows\system32\eventlog.dll was found and disinfected
Restored copy from - c:\windows\system32\dllcache\eventlog.dll
c:\windows\system32\drivers\beep.sys . . . is infected!!
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
-------\Legacy_IPRIP
-------\Legacy_{79007602-0CDB-4405-9DBF-1257BB3226ED}
-------\Service_Iprip
((((((((((((((((((((((((( Files Created from 2009-08-12 to 2009-09-12 )))))))))))))))))))))))))))))))
.
2009-09-12 03:27 . 2009-09-12 03:46 -------- d-----w- c:\documents and settings\All Users\Application Data\TrackMania
2009-09-12 02:51 . 2009-09-12 02:57 -------- d-----w- c:\program files\TmUnitedForever
2009-09-12 02:39 . 2009-09-12 02:41 -------- d-----w- c:\program files\TrackMania United
2009-09-07 19:34 . 2009-09-07 19:34 -------- d-----w- c:\windows\system32\wbem\Repository
2009-09-07 19:34 . 2009-09-07 19:34 -------- d-----w- c:\program files\Viewpoint
2009-09-05 21:35 . 2009-09-07 19:34 -------- d-----w- c:\documents and settings\HP_Owner\.housecall6.6
2009-09-05 05:47 . 2009-09-05 05:47 -------- d-----w- c:\program files\Lavalys
2009-09-01 21:54 . 2009-09-01 21:54 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\GraveyardShift
2009-09-01 21:53 . 2009-09-01 21:53 -------- d-----w- c:\documents and settings\All Users\Application Data\TEMP
2009-09-01 21:52 . 2009-09-01 21:52 -------- d-----w- c:\program files\GoGii Games
2009-08-31 18:27 . 2009-08-31 18:27 -------- d-----w- c:\program files\Steinberg
2009-08-31 18:27 . 2009-08-31 18:27 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\Antares
2009-08-31 18:27 . 2009-08-31 18:27 -------- d-----w- c:\program files\Antares Audio Technologies
2009-08-28 20:50 . 2009-08-29 20:57 -------- d-----w- c:\program files\osu!
2009-08-28 20:50 . 2009-08-28 20:50 -------- d-----w- c:\windows\osu!
2009-08-27 06:52 . 2009-08-27 16:31 -------- d-----w- c:\program files\De Blob
2009-08-25 14:23 . 2009-08-25 14:23 -------- d-----w- c:\windows\system32\Adobe
2009-08-24 16:39 . 2009-08-24 16:39 -------- d-----w- c:\program files\Tale of Tales
2009-08-24 16:39 . 2007-07-27 21:57 57449 ----a-w- c:\windows\system32\The Endless Forest 3.scr
2009-08-24 12:03 . 2009-08-24 12:03 -------- d-----w- c:\program files\The Marriage
2009-08-24 10:34 . 2009-08-24 10:34 -------- d-----w- c:\documents and settings\HP_Owner\bin
2009-08-24 10:32 . 2009-08-24 10:32 -------- d-----w- c:\program files\Colormental
2009-08-22 09:55 . 2009-08-22 09:55 -------- d-----w- c:\program files\Trend Micro
2009-08-21 10:58 . 2009-08-21 10:58 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\TeamViewer
2009-08-15 12:58 . 2009-08-15 12:58 56 ---ha-w- c:\windows\system32\ezsidmv.dat
2009-08-15 12:58 . 2009-09-07 21:43 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\skypePM
2009-08-15 12:58 . 2009-09-07 22:23 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\Skype
2009-08-15 12:58 . 2009-08-15 12:58 -------- d-----w- c:\program files\Common Files\Skype
2009-08-15 12:58 . 2009-08-15 12:58 -------- d-----r- c:\program files\Skype
2009-08-15 12:57 . 2009-08-15 12:58 -------- d-----w- c:\documents and settings\All Users\Application Data\Skype
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-09-12 09:38 . 2009-04-30 23:17 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\MxBoost
2009-09-12 06:40 . 2009-05-01 00:06 -------- d-----w- c:\program files\Warcraft III
2009-09-11 19:23 . 2009-04-30 23:20 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\Azureus
2009-09-11 18:45 . 2009-05-06 12:30 -------- d-----w- c:\program files\Steam
2009-09-08 02:24 . 2009-04-30 23:09 -------- d-----w- c:\program files\Maxthon2
2009-09-06 15:34 . 2009-05-08 23:00 -------- d-----w- c:\documents and settings\HP_Owner\Application Data\U3
2009-08-31 14:41 . 2006-02-16 11:03 -------- d-----w- c:\program files\Java
2009-08-26 13:05 . 2009-04-30 23:19 -------- d-----w- c:\program files\Vuze
2009-08-25 19:23 . 2009-05-01 00:10 78562 ----a-w- c:\windows\War3Unin.dat
2009-08-19 22:38 . 2009-05-20 00:12 -------- d-----w- c:\program files\Spybot - Search & Destroy
2009-08-01 00:07 . 2009-08-01 00:07 -------- d-----w- c:\program files\CEVO
2009-07-30 07:21 . 2009-07-30 07:21 -------- d-----w- c:\program files\uTorrent
2009-07-28 16:06 . 2009-07-28 16:06 0 ----a-w- c:\windows\system32\cid_store.dat
2009-07-25 09:23 . 2009-07-04 04:21 411368 ----a-w- c:\windows\system32\deploytk.dll
2009-07-22 14:56 . 2009-07-22 14:56 -------- d-----w- c:\program files\Microsoft
2009-07-15 17:02 . 2009-05-17 15:31 -------- d-----w- c:\program files\Free Music Zilla
2009-06-15 22:22 . 2009-05-30 03:34 35304 ----a-w- c:\windows\DIIUnin.dat
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\URLSearchHooks]
"{57BCA5FA-5DBB-45a2-B558-1755C3F6253B}"= "c:\program files\Winamp Toolbar\winamptb.dll" [2009-02-19 1262888]
[HKEY_CLASSES_ROOT\clsid\{57bca5fa-5dbb-45a2-b558-1755c3f6253b}]
[HKEY_CLASSES_ROOT\WINAMPTB.AOLTBSearch.1]
[HKEY_CLASSES_ROOT\TypeLib\{538CD77C-BFDD-49b0-9562-77419CAB89D1}]
[HKEY_CLASSES_ROOT\WINAMPTB.AOLTBSearch]
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-05 2260480]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"HPHUPD08"="c:\program files\HP\Digital Imaging\{33D6CC28-9F75-4d1b-A11D-98895B3A3729}\hphupd08.exe" [2005-06-02 49152]
"Recguard"="c:\windows\SMINST\RECGUARD.EXE" [2005-07-23 237568]
"HPBootOp"="c:\program files\Hewlett-Packard\HP Boot Optimizer\HPBootOp.exe" [2005-11-10 249856]
"Reminder"="c:\windows\Creator\Remind_XP.exe" [2004-12-14 663552]
"HP Software Update"="c:\program files\HP\HP Software Update\HPwuSchd2.exe" [2005-05-12 49152]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2009-03-27 13684736]
"NvMediaCenter"="c:\windows\system32\NvMcTray.dll" [2009-03-27 86016]
"CTSysVol"="c:\program files\Creative\SBAudigy2\Surround Mixer\CTSysVol.exe" [2003-09-17 57344]
"SBDrvDet"="c:\program files\Creative\SB Drive Det\SBDrvDet.exe" [2002-12-03 45056]
"UpdReg"="c:\windows\UpdReg.EXE" [2000-05-11 90112]
"GrooveMonitor"="c:\program files\Microsoft Office\Office12\GrooveMonitor.exe" [2006-10-27 31016]
"TkBellExe"="c:\program files\Common Files\Real\Update_OB\realsched.exe" [2006-02-16 180269]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-06-11 413696]
"SunJavaUpdateSched"="c:\program files\Java\jre6\bin\jusched.exe" [2009-07-25 149280]
"RTHDCPL"="RTHDCPL.EXE" - c:\windows\RTHDCPL.EXE [2006-01-12 15961088]
"nwiz"="nwiz.exe" - c:\windows\system32\nwiz.exe [2009-03-27 1657376]
"CTHelper"="CTHELPER.EXE" - c:\windows\system32\CtHelper.exe [2009-03-04 19456]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
HP Digital Imaging Monitor.lnk - c:\program files\HP\Digital Imaging\bin\hpqtra08.exe [2005-5-12 282624]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\WB]
2001-12-21 03:34 24576 ----a-w- c:\progra~1\Stardock\OBJECT~1\WINDOW~1\fastload.dll
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\drivers32]
"midi1"=myokent.dll
"MIDI3"=myokent.dll
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\services]
"Viewpoint Manager Service"=2 (0x2)
"Pml Driver HPZ12"=0 (0x0)
"ose"=3 (0x3)
"Microsoft Office Groove Audit Service"=3 (0x3)
"odserv"=3 (0x3)
"MDM"=2 (0x2)
"LightScribeService"=2 (0x2)
"JavaQuickStarterService"=2 (0x2)
"IDriverT"=3 (0x3)
"Creative Audio Engine Licensing Service"=3 (0x3)
"Ati HotKey Poller"=2 (0x2)
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"UpdatesDisableNotify"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"c:\\Program Files\\Free Music Zilla\\FMZilla.exe"=
"c:\\Program Files\\AIM6\\aim6.exe"=
"c:\\Program Files\\Steam\\steamapps\\lilxaznxboix\\team fortress 2\\hl2.exe"=
"c:\\Program Files\\Steam\\steamapps\\lilxaznxboix\\counter-strike\\hl.exe"=
"c:\\Documents and Settings\\HP_Owner\\temp\\TeamViewer\\Version4\\TeamViewer.exe"=
"c:\\Program Files\\Maxthon2\\Modules\\MxDownloader\\MxDownloadServer.exe"=
"c:\\WINDOWS\\system32\\The Endless Forest 3.scr"=
"c:\\Program Files\\Skype\\Phone\\Skype.exe"=
"c:\\Documents and Settings\\HP_Owner\\Desktop\\Dyadin 2\\Dyadin 2\\Dyadin 2\\bin\\dyadin.exe"=
"c:\\Program Files\\TmUnitedForever\\TmForever.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"6114:TCP"= 6114:TCP:6114t
"6114:UDP"= 6114:UDP:6114u
"6113:TCP"= 6113:TCP:6113t
"6113:UDP"= 6113:UDP:6113u
"3587:TCP"= 3587:TCP:Windows Peer-to-Peer Grouping
"3540:UDP"= 3540:UDP:Peer Name Resolution Protocol (PNRP)
"56324:TCP"= 56324:TCP:Pando Media Booster
"56324:UDP"= 56324:UDP:Pando Media Booster
"4000:TCP"= 4000:TCP:4000t
"4000:UDP"= 4000:UDP:4000u
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\IcmpSettings]
"AllowInboundEchoRequest"= 1 (0x1)
R3 COMMONFX;COMMONFX;c:\windows\system32\drivers\COMMONFX.SYS [2009-03-04 99352]
R3 CTAUDFX;CTAUDFX;c:\windows\system32\drivers\CTAUDFX.SYS [2009-03-04 555032]
R3 CTERFXFX.SYS;CTERFXFX.SYS;c:\windows\System32\drivers\CTERFXFX.SYS [2009-03-04 100888]
R3 CTERFXFX;CTERFXFX;c:\windows\system32\drivers\CTERFXFX.SYS [2009-03-04 100888]
R3 CTSBLFX;CTSBLFX;c:\windows\system32\drivers\CTSBLFX.SYS [2009-03-04 566296]
R3 NPF;NetGroup Packet Filter Driver;c:\windows\system32\drivers\npf.sys [2007-11-06 34064]
R3 XDva269;XDva269;c:\windows\system32\XDva269.sys [x]
R3 XDva277;XDva277;c:\windows\system32\XDva277.sys [x]
R4 Creative Audio Engine Licensing Service;Creative Audio Engine Licensing Service;c:\program files\Common Files\Creative Labs Shared\Service\CTAELicensing.exe [2009-05-11 79360]
R4 Viewpoint Manager Service;Viewpoint Manager Service;c:\program files\Viewpoint\Common\ViewpointService.exe [2007-01-04 24652]
S3 COMMONFX.SYS;COMMONFX.SYS;c:\windows\System32\drivers\COMMONFX.SYS [2009-03-04 99352]
S3 CTAUDFX.SYS;CTAUDFX.SYS;c:\windows\System32\drivers\CTAUDFX.SYS [2009-03-04 555032]
S3 CTSBLFX.SYS;CTSBLFX.SYS;c:\windows\System32\drivers\CTSBLFX.SYS [2009-03-04 566296]
S3 EuMusDesignVirtualAudioCableWdm;Virtual Audio Cable (WDM);c:\windows\system32\DRIVERS\vrtaucbl.sys [2006-12-31 31616]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\svchost]
p2psvc REG_MULTI_SZ p2psvc p2pimsvc p2pgasvc PNRPSvc
.
- - - - ORPHANS REMOVED - - - -
HKCU-Run-Aim6 - (no file)
HKLM-Run-PCDrProfiler - (no file)
HKLM-Run-CTXFIREG - CTxfiReg.exe
.
------- Supplementary Scan -------
.
uStart Page = hxxp://ie.redirect.hp.com/svs/rdr?TYPE=3&tp=iehome&locale=EN_US&c=Q106&bd=pavilion&pf=desktop
uDefault_Search_URL = hxxp://ie.redirect.hp.com/svs/rdr?TYPE=3&tp=iesearch&locale=EN_US&c=Q106&bd=pavilion&pf=desktop
mSearch Bar = hxxp://ie.redirect.hp.com/svs/rdr?TYPE=3&tp=iesearch&locale=EN_US&c=Q106&bd=pavilion&pf=desktop
uInternet Connection Wizard,ShellNext = iexplore
IE: &Winamp Search - c:\documents and settings\All Users\Application Data\Winamp Toolbar\ieToolbar\resources\en-US\local\search.html
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~4\Office12\EXCEL.EXE/3000
Trusted Zone: aol.com\free
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-09-12 05:50
Windows 5.1.2600 Service Pack 2 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
CTHelper = CTHELPER.EXE?
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-487398202-596544020-2533468191-1009\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID]
@Denied: (Full) (LocalSystem)
@SACL=
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'winlogon.exe'(812)
c:\windows\system32\myokent.dll
c:\windows\system32\Ati2evxx.dll
c:\progra~1\Stardock\OBJECT~1\WINDOW~1\fastload.dll
- - - - - - - > 'lsass.exe'(872)
c:\windows\system32\myokent.dll
- - - - - - - > 'explorer.exe'(3340)
c:\windows\system32\myokent.dll
c:\windows\system32\hnetcfg.dll
.
------------------------ Other Running Processes ------------------------
.
c:\program files\Creative\Shared Files\CTAudSvc.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\windows\system32\nvsvc32.exe
c:\windows\system32\tcpsvcs.exe
c:\windows\system32\wdfmgr.exe
c:\windows\system32\rundll32.exe
c:\windows\system32\wscntfy.exe
c:\windows\system32\rundll32.exe
c:\hp\KBD\kbd.exe
.
**************************************************************************
.
Completion time: 2009-09-12 5:54 - machine was rebooted
ComboFix-quarantined-files.txt 2009-09-12 09:54
Pre-Run: 105,822,593,024 bytes free
Post-Run: 107,604,398,080 bytes free
238 --- E O F --- 2009-05-11 20:24
-
 HiJackThis Log
HiJackThis Log
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 11:06:08 AM, on 9/12/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.6000.16827)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Creative\Shared Files\CTAudSvc.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINDOWS\system32\nvsvc32.exe
C:\WINDOWS\system32\tcpsvcs.exe
C:\Program Files\HP\HP Software Update\HPwuSchd2.exe
C:\WINDOWS\system32\RUNDLL32.EXE
C:\Program Files\Creative\SBAudigy2\Surround Mixer\CTSysVol.exe
C:\Program Files\Microsoft Office\Office12\GrooveMonitor.exe
C:\Program Files\Java\jre6\bin\jusched.exe
C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe
C:\WINDOWS\system32\wscntfy.exe
C:\WINDOWS\System32\svchost.exe
C:\HP\KBD\KBD.EXE
C:\WINDOWS\explorer.exe
c:\windows\system\hpsysdrv.exe
C:\Program Files\Maxthon2\Maxthon.exe
C:\Program Files\Trend Micro\HijackThis\HijackThis.exe
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://ie.redirect.hp.com/svs/rdr?TY...ion&pf=desktop
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://ie.redirect.hp.com/svs/rdr?TY...ion&pf=desktop
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Bar = http://ie.redirect.hp.com/svs/rdr?TY...ion&pf=desktop
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R3 - URLSearchHook: Winamp Search Class - {57BCA5FA-5DBB-45a2-B558-1755C3F6253B} - C:\Program Files\Winamp Toolbar\winamptb.dll
O2 - BHO: AcroIEHlprObj Class - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll
O2 - BHO: Winamp Toolbar Loader - {25CEE8EC-5730-41bc-8B58-22DDC8AB8C20} - C:\Program Files\Winamp Toolbar\winamptb.dll
O2 - BHO: Spybot-S&D IE Protection - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\PROGRA~1\MICROS~4\Office12\GRA8E1~1.DLL
O2 - BHO: HpWebHelper - {AAAE832A-5FFF-4661-9C8F-369692D1DCB9} - C:\WINDOWS\pchealth\helpctr\Vendors\CN=Hewlett-Packard,L=Cupertino,S=Ca,C=US\plugin\WebHelper.dll
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre6\bin\jp2ssv.dll
O2 - BHO: JQSIEStartDetectorImpl - {E7E6F031-17CE-4C07-BC86-EABFE594F69C} - C:\Program Files\Java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
O3 - Toolbar: Winamp Toolbar - {EBF2BA02-9094-4c5a-858B-BB198F3D8DE2} - C:\Program Files\Winamp Toolbar\winamptb.dll
O4 - HKLM\..\Run: [RTHDCPL] RTHDCPL.EXE
O4 - HKLM\..\Run: [HPHUPD08] c:\Program Files\HP\Digital Imaging\{33D6CC28-9F75-4d1b-A11D-98895B3A3729}\hphupd08.exe
O4 - HKLM\..\Run: [Recguard] C:\WINDOWS\SMINST\RECGUARD.EXE
O4 - HKLM\..\Run: [HPBootOp] "C:\Program Files\Hewlett-Packard\HP Boot Optimizer\HPBootOp.exe" /run
O4 - HKLM\..\Run: [Reminder] "C:\Windows\Creator\Remind_XP.exe"
O4 - HKLM\..\Run: [HP Software Update] C:\Program Files\HP\HP Software Update\HPwuSchd2.exe
O4 - HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup
O4 - HKLM\..\Run: [nwiz] nwiz.exe /install
O4 - HKLM\..\Run: [NvMediaCenter] RUNDLL32.EXE C:\WINDOWS\system32\NvMcTray.dll,NvTaskbarInit
O4 - HKLM\..\Run: [CTSysVol] C:\Program Files\Creative\SBAudigy2\Surround Mixer\CTSysVol.exe /r
O4 - HKLM\..\Run: [SBDrvDet] C:\Program Files\Creative\SB Drive Det\SBDrvDet.exe /r
O4 - HKLM\..\Run: [UpdReg] C:\WINDOWS\UpdReg.EXE
O4 - HKLM\..\Run: [GrooveMonitor] "C:\Program Files\Microsoft Office\Office12\GrooveMonitor.exe"
O4 - HKLM\..\Run: [CTHelper] CTHELPER.EXE
O4 - HKLM\..\Run: [TkBellExe] "C:\Program Files\Common Files\Real\Update_OB\realsched.exe" -osboot
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKLM\..\Run: [SunJavaUpdateSched] "C:\Program Files\Java\jre6\bin\jusched.exe"
O4 - HKCU\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
O4 - HKUS\S-1-5-21-487398202-596544020-2533468191-1009\..\Run: [SpybotSD TeaTimer] C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe (User '?')
O4 - .DEFAULT User Startup: Pin.lnk = C:\hp\bin\CLOAKER.EXE (User 'Default user')
O4 - Global Startup: HP Digital Imaging Monitor.lnk = C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe
O8 - Extra context menu item: &Winamp Search - C:\Documents and Settings\All Users\Application Data\Winamp Toolbar\ieToolbar\resources\en-US\local\search.html
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~1\MICROS~4\Office12\EXCEL.EXE/3000
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~4\Office12\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: S&end to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\PROGRA~1\MICROS~4\Office12\ONBttnIE.dll
O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~4\Office12\REFIEBAR.DLL
O9 - Extra button: (no name) - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra 'Tools' menuitem: Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O9 - Extra button: Internet Connection Help - {E2D4D26B-0180-43a4-B05F-462D6D54C789} - C:\WINDOWS\PCHEALTH\HELPCTR\Vendors\CN=Hewlett-Packard,L=Cupertino,S=Ca,C=US\IEButton\support.htm
O9 - Extra 'Tools' menuitem: Internet Connection Help - {E2D4D26B-0180-43a4-B05F-462D6D54C789} - C:\WINDOWS\PCHEALTH\HELPCTR\Vendors\CN=Hewlett-Packard,L=Cupertino,S=Ca,C=US\IEButton\support.htm
O16 - DPF: {02BF25D5-8C17-4B23-BC80-D3488ABDDC6B} (QuickTime Plugin Control) - http://appldnld.apple.com.edgesuite....x/qtplugin.cab
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} (Windows Genuine Advantage Validation Tool) - http://go.microsoft.com/fwlink/?linkid=39204
O18 - Protocol: grooveLocalGWS - {88FED34C-F0CA-4636-A375-3CB6248B04CD} - C:\PROGRA~1\MICROS~4\Office12\GR99D3~1.DLL
O18 - Protocol: skype4com - {FFC8B962-9B40-4DFF-9458-1830C7DD7F5D} - C:\PROGRA~1\COMMON~1\Skype\SKYPE4~1.DLL
O23 - Service: Creative Audio Service (CTAudSvcService) - Creative Technology Ltd - C:\Program Files\Creative\Shared Files\CTAudSvc.exe
O23 - Service: Java Quick Starter (JavaQuickStarterService) - Sun Microsystems, Inc. - C:\Program Files\Java\jre6\bin\jqs.exe
O23 - Service: NVIDIA Display Driver Service (NVSvc) - NVIDIA Corporation - C:\WINDOWS\system32\nvsvc32.exe
O23 - Service: Remote Packet Capture Protocol v.0 (experimental) (rpcapd) - CACE Technologies - C:\Program Files\WinPcap\rpcapd.exe
--
End of file - 7420 bytes
-

Hi,
You need to enable windows to show all files and folders, instructions Here
Go to VirusTotal and submit this file for analysis, just use the browse feature and then Send File, you will get a report back, post the report into this thread for me to see.
c:\windows\system32\drivers\beep.sys
Download TFC to your desktop
- Close any open windows.
- Double click the TFC icon to run the program
- TFC will close all open programs itself in order to run,
- Click the Start button to begin the process.
- Allow TFC to run uninterrupted.
- The program should not take long to finish it's job
- Once its finished it should automatically reboot your machine,
- if it doesn't, manually reboot to ensure a complete clean
Please download Malwarebytes' Anti-Malware from Here or Here
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.

- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected .
- When completed, a log will open in Notepad. Please save it to a convenient location and post the results.
- Note: If you receive a notice that some of the items couldn't be removed, that they have been added to the delete on reboot list, please reboot.
Post the report and also a new HJT log please
I need the Malwarebytes log, the report from VT and a new HJT log please
-

Due to inactivity, this thread will now be closed.
If it has been four days or more since your last post, and the helper assisting you posted a response to that post to which you did not reply, your topic will not be reopened. At that point, if you still require help, please start a new topic and include a new HijackThis log with a link to your previous thread. Please do not add any logs that might have been requested in the closed topic, you would be starting fresh.
Last edited by tashi; 2009-09-24 at 19:18.
Reason: Thank you Ken
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules



 tab.
tab. button.
button.
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.