-
 Fresh Windows got badly infected + various questions.
Fresh Windows got badly infected + various questions.
The questions are more important to me than problem itself, so please help me with them first.
I have a linksys router with firewall enabled and all ports closed. I have desktop and laptop PCs. My laptop is a HP Compaq-615 with 2 logic recovery drives. My laptop PC is severly infected, my desktop has Comodo firewall and Nod32 antivirus.
1.) If I will run a full format on laptop, will files in recovery drives still be infected?
2.) If I copy some of my data from laptop to desktop, is there a chance that I'll get a virus with it?
3.) If I format desktop PC (I was planning to anyway) and then copy some of the files, including anti-malware stuff from laptop, will I get infected?
4.) If I copy files from laptop to flash drive, will it get infected?
5.) If I copy some of the files from infected drive to HP recovery one, will they be infected?
The problem:
I recently bought a new laptop and installed Windows XP on it. I admit, that was very stupid of me, but I was lazy and didn't install any firewall/antivirus/spyware on it. I used this laptop for a week at University, which had a unsecured wireless network (from which I think I've got all the problems). 2 days ago it hit me to get some protection.
I installed Eset Nod32 4.0, it found a Win32/Olmarik Trojan and said that it can't delete it because it's in memory + some other viruses (don't remember names, sadly) + Kryptic.ZS trojan, which it stated to have deleted.
I then installed MalwareBytes and Spybot S&D. Ran both, they've found some minor spybots, removed. Booted in safe mode, scanned with Nod32, nothing.
Today when I turned on laptop, Nod32 found both Olmarik and Kryptic.ZS trojans again. I tried looking for .dlls, nothing. I installed Spyware Doctor, it didn't find anything. I then tried going to safe mode, but it did not boot at all (loads up all required dlls and then restarts and shows me that windows didn't turn off properly and blah blah). I then booted to Windows and it went all to hell. I've got some weird X in the tray stating that I have spyware and I should go to some bogus site and install their stuff), S&D refused to work, Nod32 flashed with virus notifications. Malwarebytes detected some, but I still have the Olmarik and Kryptic.ZS. It's a fresh windows install, so I don't mind reformatting if doing a full clean saves the hassle. My main concern are files, mentioned in questions.
Here's the Malwarebytes log
Malwarebytes' Anti-Malware 1.41
Database version: 2792
Windows 5.1.2600 Service Pack 3, v.5755
14.09.2009 22:31:42
mbam-log-2009-09-14 (22-31-42).txt
Scan type: Full Scan (C:\|E:\|F:\|)
Objects scanned: 134438
Time elapsed: 14 minute(s), 7 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 1
Registry Keys Infected: 0
Registry Values Infected: 2
Registry Data Items Infected: 3
Folders Infected: 0
Files Infected: 23
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
C:\WINDOWS\system32\autochk.dll (Trojan.Agent) -> Delete on reboot.
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\autochk (Trojan.Agent) -> Delete on reboot.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\autochk (Trojan.Agent) -> Delete on reboot.
Registry Data Items Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Not selected for removal.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Not selected for removal.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Not selected for removal.
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\autochk.dll (Trojan.Agent) -> Delete on reboot.
C:\Documents and Settings\Inori\protect.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Local Settings\Temporary Internet Files\Content.IE5\2EI4LF1D\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Local Settings\Temporary Internet Files\Content.IE5\GLQQC2C7\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Local Settings\Temporary Internet Files\Content.IE5\X2B5416M\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Local Settings\Temporary Internet Files\Content.IE5\XSMBXUX6\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Start Menu\Programs\Startup\ChkDisk.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\LocalService\protect.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\cru629.dat (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\cru629.dat (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\config\systemprofile\protect.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\config\systemprofile\Local Settings\Temporary Internet Files\Content.IE5\PNSXCUYE\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\config\systemprofile\Local Settings\Temporary Internet Files\Content.IE5\W9K1E0R2\Install[1].exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\config\systemprofile\Start Menu\Programs\Startup\ChkDisk.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\dllcache\beep.sys (Trojan.KillAV) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\beep.sys (Trojan.KillAV) -> Quarantined and deleted successfully.
C:\WINDOWS\Temp\rundll32.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Start Menu\Programs\Startup\ChkDisk.lnk (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\str.sys (Rootkit.Agent) -> Delete on reboot.
C:\WINDOWS\Temp\nsrbgxod.bak (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\Inori\Local Settings\Temp\nsrbgxod.bak (Trojan.Agent) -> Delete on reboot.
C:\Documents and Settings\NetworkService\protect.dll (Trojan.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\braviax.exe (Trojan.Downloader) -> Delete on reboot.
-

Hello Inori
Welcome to Safer Networking.
Please read Before You Post
That said, All advice given by anyone volunteering here, is taken at your own risk.
While best efforts are made to assist in removing infections safely, unexpected stuff can happen.
First off let me say that I do not know what your infected with, with the threats going around now its very possible that after a clean install that one of your backed up files was infected and reinfected the clean computer. The way this works is we only do one computer at a time, I assume this is your laptop? When were done cleaning this one you can post for the other , working two computers at the same time gets very confusing. What I would do also is to keep the other computers offline until we get this one cleaned up.
Please download RootRepeal one of these locations and save it to your desktop
Here
Here
Here
- Open
 on your desktop.
on your desktop. - Click the
 tab.
tab. - Click the
 button.
button. - Check just these boxes:
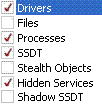
- Push Ok
- Check the box for your main system drive (Usually C:, and press Ok.
- Allow RootRepeal to run a scan of your system. This may take some time.
- Once the scan completes, push the
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
- Download random's system information tool (RSIT) by random/random from here and save it to your desktop.
- Double click on RSIT.exe to run RSIT.
- Click Continue at the disclaimer screen.
- Once it has finished, two logs will open. Please post the contents of both log.txt (<<will be maximized) and info.txt (<<will be minimized)
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules



 tab.
tab. button.
button.
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.