Here are the logs you need. Thanks for the speedy replies to my questions, they were really helpful. 
Spybot S&D Log:
Code:
Click.GiftLoad: [SBI $89783858] User settings (Registry value, nothing done)
HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\Main\featurecontrol\FEATURE_BROWSER_EMULATION\svchost.exe
DoubleClick: Tracking cookie (Chrome: Chrome) (Cookie, nothing done)
Statcounter: Tracking cookie (Chrome: Chrome) (Cookie, nothing done)
--- Spybot - Search & Destroy version: 1.6.2 (build: 20090126) ---
2009-01-26 blindman.exe (1.0.0.8)
2009-01-26 SDFiles.exe (1.6.1.7)
2009-01-26 SDMain.exe (1.0.0.6)
2009-01-26 SDShred.exe (1.0.2.5)
2009-01-26 SDUpdate.exe (1.6.0.12)
2009-01-26 SpybotSD.exe (1.6.2.46)
2009-03-05 TeaTimer.exe (1.6.6.32)
2011-03-04 unins000.exe (51.49.0.0)
2009-01-26 Update.exe (1.6.0.7)
2009-07-28 advcheck.dll (1.6.3.17)
2007-04-02 aports.dll (2.1.0.0)
2008-06-14 DelZip179.dll (1.79.11.1)
2009-01-26 SDHelper.dll (1.6.2.14)
2008-06-19 sqlite3.dll
2009-01-26 Tools.dll (2.1.6.10)
2009-01-16 UninsSrv.dll (1.0.0.0)
2011-03-18 Includes\Adware.sbi (*)
2011-03-22 Includes\AdwareC.sbi (*)
2010-08-13 Includes\Cookies.sbi (*)
2010-12-14 Includes\Dialer.sbi (*)
2011-03-08 Includes\DialerC.sbi (*)
2011-02-24 Includes\HeavyDuty.sbi (*)
2010-11-30 Includes\Hijackers.sbi (*)
2011-03-08 Includes\HijackersC.sbi (*)
2010-09-15 Includes\iPhone.sbi (*)
2010-12-14 Includes\Keyloggers.sbi (*)
2011-03-08 Includes\KeyloggersC.sbi (*)
2004-11-29 Includes\LSP.sbi (*)
2011-02-24 Includes\Malware.sbi (*)
2011-03-22 Includes\MalwareC.sbi (*)
2011-02-24 Includes\PUPS.sbi (*)
2011-03-15 Includes\PUPSC.sbi (*)
2010-01-25 Includes\Revision.sbi (*)
2009-01-13 Includes\Security.sbi (*)
2011-03-08 Includes\SecurityC.sbi (*)
2008-06-03 Includes\Spybots.sbi (*)
2008-06-03 Includes\SpybotsC.sbi (*)
2011-02-24 Includes\Spyware.sbi (*)
2011-03-15 Includes\SpywareC.sbi (*)
2010-03-08 Includes\Tracks.uti
2010-12-28 Includes\Trojans.sbi (*)
2011-03-22 Includes\TrojansC-02.sbi (*)
2011-03-03 Includes\TrojansC-03.sbi (*)
2011-03-08 Includes\TrojansC-04.sbi (*)
2011-03-21 Includes\TrojansC-05.sbi (*)
2011-03-08 Includes\TrojansC.sbi (*)
2008-03-04 Plugins\Chai.dll
2008-03-05 Plugins\Fennel.dll
2008-02-26 Plugins\Mate.dll
2007-12-24 Plugins\TCPIPAddress.dll
aswMBR Log:
Code:
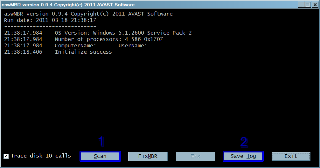
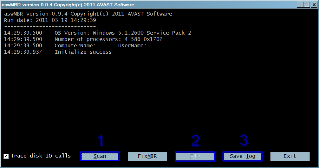
aswMBR version 0.9.4 Copyright(c) 2011 AVAST Software
Run date: 2011-04-04 14:26:10
-----------------------------
14:26:10.171 OS Version: Windows 5.1.2600 Service Pack 3
14:26:10.171 Number of processors: 2 586 0x301
14:26:10.171 ComputerName: ACER-A3FE35D430 UserName: Ben
14:26:14.250 Initialize success
14:26:24.984 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Scsi\ahcix861
14:26:25.031 Disk 0 Vendor: Hitachi_ 1.10 Size: 152627MB BusType: 1
14:26:25.109 Device \Device\Scsi\ahcix861Port0Path0Target0Lun0 -> \??\SCSI#Disk&Ven_Hitachi&Prod_HTS543216L9A3&Rev_1.10#4&30ce5629&0&000#{53f56307-b6bf-11d0-94f2-00a0c91efb8b} not found
14:26:25.187 Device \Driver\ahcix86 -> DriverStartIo 8a2d927f
14:26:27.265 Disk 0 MBR read successfully
14:26:27.359 Disk 0 MBR scan
14:26:27.453 Disk 0 TDL4@MBR code has been found
14:26:27.562 Disk 0 MBR hidden
14:26:27.671 Disk 0 MBR [TDL4] **ROOTKIT**
14:26:27.781 Disk 0 trace - called modules:
14:26:27.921 ntkrnlpa.exe CLASSPNP.SYS disk.sys ACPI.sys hal.dll >>UNKNOWN [0x8a2d9439]<<
14:26:28.046 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x8a2f8030]
14:26:28.187 3 CLASSPNP.SYS[ba168fd7] -> nt!IofCallDriver -> \Device\000000b6[0x8a847258]
14:26:28.343 5 ACPI.sys[b9e74620] -> nt!IofCallDriver -> [0x8a82da38]
14:26:28.500 \Driver\ahcix86[0x8a843680] -> IRP_MJ_CREATE -> 0x8a2d9439
14:26:28.703 Scan finished successfully
Gmer Log:
Code:
GMER 1.0.15.15570 - http://www.gmer.net
Rootkit scan 2011-04-04 15:20:40
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Scsi\ahcix861 Hitachi_ rev.1.10
Running: 7ljmggj8.exe; Driver: C:\DOCUME~1\Ben\LOCALS~1\Temp\ufacakog.sys
---- System - GMER 1.0.15 ----
SSDT Lbd.sys (Boot Driver/Lavasoft AB) ZwCreateKey [0xBA17887E]
SSDT sphf.sys ZwEnumerateKey [0xB9ECDDA4]
SSDT sphf.sys ZwEnumerateValueKey [0xB9ECE132]
SSDT sphf.sys ZwOpenKey [0xB9EB50C0]
SSDT \SystemRoot\system32\DRIVERS\AVGIDSShim.Sys (IDS Application Activity Monitor Loader Driver./AVG Technologies CZ, s.r.o. ) ZwOpenProcess [0xB93B56C0]
SSDT sphf.sys ZwQueryKey [0xB9ECE20A]
SSDT sphf.sys ZwQueryValueKey [0xB9ECE08A]
SSDT Lbd.sys (Boot Driver/Lavasoft AB) ZwSetValueKey [0xBA178BFE]
SSDT \SystemRoot\system32\DRIVERS\AVGIDSShim.Sys (IDS Application Activity Monitor Loader Driver./AVG Technologies CZ, s.r.o. ) ZwTerminateProcess [0xB93B5770]
SSDT \SystemRoot\system32\DRIVERS\AVGIDSShim.Sys (IDS Application Activity Monitor Loader Driver./AVG Technologies CZ, s.r.o. ) ZwTerminateThread [0xB93B5810]
SSDT \SystemRoot\system32\DRIVERS\AVGIDSShim.Sys (IDS Application Activity Monitor Loader Driver./AVG Technologies CZ, s.r.o. ) ZwWriteVirtualMemory [0xB93B58B0]
INT 0x73 ? 8A142E58
INT 0x94 ? 8A142E58
INT 0x94 ? 8A142E58
INT 0x94 ? 8A142E58
INT 0xA4 ? 8A90FBF8
---- Kernel code sections - GMER 1.0.15 ----
? sphf.sys The system cannot find the file specified. !
.text C:\WINDOWS\system32\DRIVERS\ati2mtag.sys section is writeable [0xB8238000, 0x189FCA, 0xE8000020]
.text USBPORT.SYS!DllUnload B80548AC 5 Bytes JMP 8A142438
.text ag8j1lst.SYS B7DBC386 35 Bytes [00, 00, 00, 00, 00, 00, 20, ...]
.text ag8j1lst.SYS B7DBC3AA 24 Bytes [00, 00, 00, 00, 00, 00, 00, ...]
.text ag8j1lst.SYS B7DBC3C4 3 Bytes [00, 80, 02]
.text ag8j1lst.SYS B7DBC3C9 1 Byte [30]
.text ag8j1lst.SYS B7DBC3C9 11 Bytes [30, 00, 00, 00, 5E, 02, 00, ...] {XOR [EAX], AL; ADD [EAX], AL; POP ESI; ADD AL, [EAX]; ADD [EAX], AL; ADD [EAX], AL}
.text ...
? C:\DOCUME~1\Ben\LOCALS~1\Temp\aswMBR.sys The system cannot find the file specified. !
---- User code sections - GMER 1.0.15 ----
.text C:\WINDOWS\system32\svchost.exe[844] ntdll.dll!NtProtectVirtualMemory 7C90D6EE 5 Bytes JMP 0071000A
.text C:\WINDOWS\system32\svchost.exe[844] ntdll.dll!NtWriteVirtualMemory 7C90DFAE 5 Bytes JMP 00DC000A
.text C:\WINDOWS\system32\svchost.exe[844] ntdll.dll!KiUserExceptionDispatcher 7C90E47C 5 Bytes JMP 0070000C
.text C:\WINDOWS\system32\svchost.exe[844] USER32.dll!GetCursorPos 7E42974E 5 Bytes JMP 00FB000A
.text C:\WINDOWS\system32\svchost.exe[844] USER32.dll!WindowFromPoint 7E429766 5 Bytes JMP 00FC000A
.text C:\WINDOWS\system32\svchost.exe[844] USER32.dll!GetForegroundWindow 7E429823 5 Bytes JMP 00FD000A
.text C:\WINDOWS\system32\svchost.exe[844] ole32.dll!CoCreateInstance 774FF1AC 5 Bytes JMP 00F0000A
.text C:\WINDOWS\Explorer.EXE[856] ntdll.dll!NtProtectVirtualMemory 7C90D6EE 5 Bytes JMP 00C2000A
.text C:\WINDOWS\Explorer.EXE[856] ntdll.dll!NtWriteVirtualMemory 7C90DFAE 5 Bytes JMP 00C3000A
.text C:\WINDOWS\Explorer.EXE[856] ntdll.dll!KiUserExceptionDispatcher 7C90E47C 5 Bytes JMP 00B8000C
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs 8A8871F8
AttachedDevice \FileSystem\Ntfs \Ntfs AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
Device \FileSystem\Fastfat \FatCdrom 85CD21F8
AttachedDevice \Driver\Tcpip \Device\Ip avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
Device \Driver\USBSTOR \Device\000000cf 8A14C330
Device \Driver\NetBT \Device\NetBT_Tcpip_{6D26E4D1-C34F-40BE-830E-4037CE269D6E} 8A0CC500
Device \Driver\usbohci \Device\USBPDO-0 8A13F500
Device \Driver\usbohci \Device\USBPDO-1 8A13F500
Device \Driver\dmio \Device\DmControl\DmIoDaemon 8A90D1F8
Device \Driver\dmio \Device\DmControl\DmConfig 8A90D1F8
Device \Driver\dmio \Device\DmControl\DmPnP 8A90D1F8
Device \Driver\dmio \Device\DmControl\DmInfo 8A90D1F8
Device \Driver\usbehci \Device\USBPDO-2 8A115500
Device \Driver\usbohci \Device\USBPDO-3 8A13F500
Device \Driver\usbehci \Device\USBPDO-4 8A115500
AttachedDevice \Driver\Tcpip \Device\Tcp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Tcp Lbd.sys (Boot Driver/Lavasoft AB)
Device \Driver\NetBT \Device\NetBT_Tcpip_{BAD1109F-EA5B-4F7A-8EF8-3BC50C0CE419} 8A0CC500
Device \Driver\Ftdisk \Device\HarddiskVolume1 8A89E1F8
Device \Driver\Ftdisk \Device\HarddiskVolume2 8A89E1F8
Device \Driver\Cdrom \Device\CdRom0 8A1621F8
Device \Driver\Ftdisk \Device\HarddiskVolume3 8A89E1F8
Device \Driver\Cdrom \Device\CdRom1 8A1621F8
Device \Driver\NetBT \Device\NetBT_Tcpip_{93277B27-BBF8-4BBC-A568-6E0D30B43B52} 8A0CC500
Device \Driver\NetBT \Device\NetBt_Wins_Export 8A0CC500
Device \Driver\USBSTOR \Device\000000d0 8A14C330
Device \Driver\NetBT \Device\NetbiosSmb 8A0CC500
Device \Driver\PCI_PNP1216 \Device\00000085 sphf.sys
Device \Driver\sptd \Device\2396817466 sphf.sys
AttachedDevice \Driver\Tcpip \Device\Udp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Udp Lbd.sys (Boot Driver/Lavasoft AB)
AttachedDevice \Driver\Tcpip \Device\RawIp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\RawIp Lbd.sys (Boot Driver/Lavasoft AB)
Device \Driver\usbohci \Device\USBFDO-0 8A13F500
Device \Driver\usbohci \Device\USBFDO-1 8A13F500
Device \FileSystem\MRxSmb \Device\LanmanDatagramReceiver 895231F8
Device \Driver\usbehci \Device\USBFDO-2 8A115500
Device \FileSystem\MRxSmb \Device\LanmanRedirector 895231F8
Device \Driver\usbohci \Device\USBFDO-3 8A13F500
Device \Driver\usbehci \Device\USBFDO-4 8A115500
Device \Driver\Ftdisk \Device\FtControl 8A89E1F8
Device \Driver\ahcix86 -> DriverStartIo \Device\Scsi\ahcix861 8A2D927F
Device \Driver\ahcix86 \Device\Scsi\ahcix861 8A8891F8
Device \Driver\ahcix86 -> DriverStartIo \Device\Scsi\ahcix861Port0Path0TargetaLun0 8A2D927F
Device \Driver\ahcix86 \Device\Scsi\ahcix861Port0Path0TargetaLun0 8A8891F8
Device \Driver\ag8j1lst \Device\Scsi\ag8j1lst1 8A089500
Device \Driver\ahcix86 -> DriverStartIo \Device\Scsi\ahcix861Port0Path0Target1Lun0 8A2D927F
Device \Driver\ahcix86 \Device\Scsi\ahcix861Port0Path0Target1Lun0 8A8891F8
Device \Driver\ag8j1lst \Device\Scsi\ag8j1lst1Port1Path0Target0Lun0 8A089500
Device \FileSystem\Fastfat \Fat 85CD21F8
AttachedDevice \FileSystem\Fastfat \Fat fltMgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
AttachedDevice \FileSystem\Fastfat \Fat AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
Device \FileSystem\Cdfs \Cdfs 8A1C9500
Device \Device\Scsi\ahcix861Port0Path0Target0Lun0 -> \??\SCSI#Disk&Ven_Hitachi&Prod_HTS543216L9A3&Rev_1.10#4&30ce5629&0&000#{53f56307-b6bf-11d0-94f2-00a0c91efb8b} device not found
---- Registry - GMER 1.0.15 ----
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@u0 0x00 0x00 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@h0 0
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@hdf12 0xD2 0x90 0x48 0x12 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@hdf12 0xB9 0x1E 0x1A 0xF9 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0@hdf12 0x92 0xEB 0x25 0x71 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@u0 0x00 0x00 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@h0 0
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@hdf12 0xD2 0x90 0x48 0x12 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@hdf12 0xB9 0x1E 0x1A 0xF9 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0@hdf12 0x92 0xEB 0x25 0x71 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@s1 771343423
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@s2 285507792
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@h0 1
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@u0 0x00 0x00 0x00 0x00 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@h0 0
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC@hdf12 0xD2 0x90 0x48 0x12 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001@hdf12 0xB9 0x1E 0x1A 0xF9 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\14919EA49A8F3B4AA3CF1058D9A64CEC\00000001\gdq0@hdf12 0x92 0xEB 0x25 0x71 ...
---- Disk sectors - GMER 1.0.15 ----
Disk \Device\Harddisk0\DR0 TDL4@MBR code has been found <-- ROOTKIT !!!
Disk \Device\Harddisk0\DR0 sector 00: rootkit-like behavior
---- EOF - GMER 1.0.15 ----