-
 CLick.Giftloader Re-appearing and possible rootkit infection.
CLick.Giftloader Re-appearing and possible rootkit infection.
Hi,
I have been reading other forums and it seems this has been reading around alot.
Well basically i have a click.Giftload that re-appears every time it is "removed."
The windows OS is legitimate nothing is torrent-ed .
.
hears is my DDS.txt
Thank you very much for your help it is greatly appreciated.
.
DDS (Ver_11-03-05.01) - NTFSx86
Run by User at 10:29:36.47 on Sat 04/23/2011
Internet Explorer: 8.0.6001.18702
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2046.513 [GMT -7:00]
.
AV: Symantec AntiVirus Corporate Edition *Enabled/Updated* {FB06448E-52B8-493A-90F3-E43226D3305C}
.
============== Running Processes ===============
.
C:\WINDOWS\system32\svchost -k DcomLaunch
svchost.exe
C:\WINDOWS\System32\svchost.exe -k netsvcs
svchost.exe
svchost.exe
C:\Program Files\Common Files\Symantec Shared\ccSetMgr.exe
C:\Program Files\Common Files\Symantec Shared\ccEvtMgr.exe
C:\Program Files\Common Files\Symantec Shared\SPBBC\SPBBCSvc.exe
C:\WINDOWS\system32\spoolsv.exe
svchost.exe
C:\Program Files\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
C:\Program Files\Bonjour\mDNSResponder.exe
C:\Program Files\Symantec AntiVirus\DefWatch.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\Program Files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE
C:\Program Files\Norton SystemWorks\Norton Utilities\NPROTECT.EXE
C:\Program Files\Microsoft\Search Enhancement Pack\SeaPort\SeaPort.exe
C:\Program Files\Analog Devices\SoundMAX\SMAgent.exe
C:\WINDOWS\Explorer.EXE
C:\PROGRA~1\NORTON~1\SPEEDD~1\nopdb.exe
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\Program Files\Symantec AntiVirus\Rtvscan.exe
C:\Program Files\TortoiseSVN\bin\TSVNCache.exe
C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE
C:\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe
C:\Program Files\Canon\CAL\CALMAIN.exe
C:\Program Files\Analog Devices\SoundMAX\SMax4PNP.exe
C:\Program Files\Analog Devices\SoundMAX\Smax4.exe
C:\Program Files\Common Files\Symantec Shared\ccApp.exe
C:\PROGRA~1\SYMANT~1\VPTray.exe
C:\Program Files\Adobe\Acrobat 7.0\Distillr\Acrotray.exe
C:\Program Files\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe
C:\Program Files\Common Files\Java\Java Update\jusched.exe
C:\Program Files\iTunes\iTunesHelper.exe
C:\Program Files\Common Files\ArcSoft\Connection Service\Bin\ArcCon.ac
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\Program Files\Trusteer\Rapport\bin\RapportService.exe
C:\WINDOWS\system32\wbem\wmiapsrv.exe
C:\Program Files\iPod\bin\iPodService.exe
C:\Program Files\Symantec AntiVirus\vpc32.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\Program Files\Mozilla Firefox\plugin-container.exe
C:\Program Files\Adobe\Acrobat 7.0\Acrobat\Acrobat.exe
C:\WINDOWS\PCHEALTH\HELPCTR\Binaries\HelpCtr.exe
C:\WINDOWS\PCHealth\HelpCtr\Binaries\HelpSvc.exe
C:\Documents and Settings\User\My Documents\Downloads\dds.com
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://www.google.com/
uSearch Page =
uSearch Bar =
mStart Page = hxxp://www.att.net
uInternet Settings,ProxyOverride = *.local
mSearchAssistant =
uURLSearchHooks: ToolbarURLSearchHook Class: {ca3eb689-8f09-4026-aa10-b9534c691ce0} - c:\program files\search toolbar\tbhelper.dll
mWinlogon: Userinit=userinit.exe
BHO: AcroIEHlprObj Class: {06849e9f-c8d7-4d59-b87d-784b7d6be0b3} - c:\program files\adobe\acrobat 7.0\activex\AcroIEHelper.dll
BHO: Spybot-S&D IE Protection: {53707962-6f74-2d53-2644-206d7942484f} - c:\progra~1\spybot~1\SDHelper.dll
BHO: {9030d464-4c02-4abf-8ecc-5164760863c6} - Windows Live ID Sign-in Helper
BHO: Adobe PDF Conversion Toolbar Helper: {ae7cd045-e861-484f-8273-0445ee161910} - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {dbc80044-a445-435b-bc74-9c25c1c588a9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl: {e7e6f031-17ce-4c07-bc86-eabfe594f69c} - JQSIEStartDetectorImpl Class
TB: Adobe PDF: {47833539-d0c5-4125-9fa8-0819e2eaac93} - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll
TB: &Windows Live Toolbar: {21fa44ef-376d-4d53-9b0f-8a89d3229068} - c:\program files\windows live\toolbar\wltcore.dll
TB: Search Toolbar: {0c8413c1-fad1-446c-8584-be50576f863e} - c:\program files\search toolbar\tbcore3.dll
TB: {D4027C7F-154A-4066-A1AD-4243D8127440} - No File
EB: Adobe PDF: {182ec0be-5110-49c8-a062-beb1d02a220b} - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll
uRun: [EPSON WorkForce 500 Series] c:\windows\system32\spool\drivers\w32x86\3\e_fatieqa.exe /fu "c:\windows\temp\E_S308.tmp" /EF "HKCU"
uRun: [SpybotSD TeaTimer] c:\program files\spybot - search & destroy\TeaTimer.exe
uRun: [Rapportexe] "c:\program files\trusteer\rapport\bin\RapportService.exe" -start -after_boot
mRun: [SoundMAXPnP] c:\program files\analog devices\soundmax\SMax4PNP.exe
mRun: [SoundMAX] "c:\program files\analog devices\soundmax\Smax4.exe" /tray
mRun: [ccApp] "c:\program files\common files\symantec shared\ccApp.exe"
mRun: [vptray] c:\progra~1\symant~1\VPTray.exe
mRun: [Acrobat Assistant 7.0] "c:\program files\adobe\acrobat 7.0\distillr\Acrotray.exe"
mRun: [<NO NAME>]
mRun: [ArcSoft Connection Service] c:\program files\common files\arcsoft\connection service\bin\ACDaemon.exe
mRun: [SunJavaUpdateSched] "c:\program files\common files\java\java update\jusched.exe"
mRun: [iTunesHelper] "c:\program files\itunes\iTunesHelper.exe"
mRun: [QuickTime Task] "c:\program files\quicktime\qttask.exe" -atboottime
uExplorerRun: [Policies] c:\windows\install\javaupdate.exe
mExplorerRun: [Policies] c:\windows\install\javaupdate.exe
StartupFolder: c:\docume~1\user\startm~1\programs\startup\erunta~1.lnk - c:\program files\erunt\AUTOBACK.EXE
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\adobea~1.lnk - c:\windows\installer\{ac76ba86-1033-0000-7760-100000000002}\SC_Acrobat.exe
IE: &Search - ?s=100000341&p=GRxdm136YYUS&si=&a=4dVGR09GIOBoyvmLASuKpA&n=2010040317
IE: Convert link target to Adobe PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert link target to existing PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert selected links to Adobe PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
IE: Convert selected links to existing PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Convert selection to Adobe PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert selection to existing PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert to Adobe PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert to existing PDF - c:\program files\adobe\acrobat 7.0\acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: E&xport to Microsoft Excel - c:\progra~1\micros~2\office11\EXCEL.EXE/3000
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {FB5F1910-F110-11d2-BB9E-00C04F795683} - c:\program files\messenger\msmsgs.exe
IE: {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} - {5F7B1267-94A9-47F5-98DB-E99415F33AEC} - c:\program files\windows live\writer\WriterBrowserExtension.dll
IE: {92780B25-18CC-41C8-B9BE-3C9C571A8263} - {FF059E31-CC5A-4E2E-BF3B-96E929D65503} - c:\progra~1\micros~2\office11\REFIEBAR.DLL
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\progra~1\spybot~1\SDHelper.dll
DPF: {166B1BCA-3F9C-11CF-8075-444553540000} - hxxp://fpdownload.macromedia.com/get/shockwave/cabs/director/sw.cab
DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} - hxxp://www.update.microsoft.com/microsoftupdate/v6/V5Controls/en/x86/client/muweb_site.cab?1256651880125
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_20-windows-i586.cab
DPF: {BEA7310D-06C4-4339-A784-DC3804819809} - hxxp://www.cvsphoto.com/upload/activex/v3_0_0_7/PhotoCenter_ActiveX_Control.cab
DPF: {CAFEEFAC-0016-0000-0000-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_20-windows-i586.cab
Notify: NavLogon - c:\windows\system32\NavLogon.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\WPDShServiceObj.dll
SEH: Quick View Plus - ShellExecute Hook: {0cab0400-7395-11d0-a5e5-0020afe2fdd9} - qvphook.dll
mASetup: {08B0E5JF-4FCB-11CF-AAA5-00401C6XX500} - c:\windows\install\javaupdate.exe
Hosts: 127.0.0.1 www.spywareinfo.com
.
================= FIREFOX ===================
.
FF - ProfilePath - c:\docume~1\user\applic~1\mozilla\firefox\profiles\ljvrwzqo.default\
FF - plugin: c:\program files\canon\zoombrowser ex\program\NPCIG.dll
FF - plugin: c:\program files\microsoft\office live\npOLW.dll
FF - plugin: c:\program files\windows live\photo gallery\NPWLPG.dll
FF - plugin: c:\windows\microsoft.net\framework\v4.0.20506\wpf\NPWPF.dll
FF - Ext: Default: {972ce4c6-7e08-4474-a285-3208198ce6fd} - c:\program files\mozilla firefox\extensions\{972ce4c6-7e08-4474-a285-3208198ce6fd}
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\microsoft.net\framework\v4.0.20506\wpf\DotNetAssistantExtension
FF - Ext: Java Quick Starter:  - c:\program files\java\jre6\lib\deploy\jqs\ff
- c:\program files\java\jre6\lib\deploy\jqs\ff
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - %profile%\extensions\{20a82645-c095-46ed-80e3-08825760534b}
FF - Ext: ReloadEvery: {888d99e7-e8b5-46a3-851e-1ec45da1e644} - %profile%\extensions\{888d99e7-e8b5-46a3-851e-1ec45da1e644}
FF - Ext: Web Developer: {c45c406e-ab73-11d8-be73-000a95be3b12} - %profile%\extensions\{c45c406e-ab73-11d8-be73-000a95be3b12}
FF - Ext: Clear Cache Button: {563e4790-7e70-11da-a72b-0800200c9a66} - %profile%\extensions\{563e4790-7e70-11da-a72b-0800200c9a66}
FF - Ext: Torbutton: {e0204bd5-9d31-402b-a99d-a6aa8ffebdca} - %profile%\extensions\{e0204bd5-9d31-402b-a99d-a6aa8ffebdca}
.
---- FIREFOX POLICIES ----
FF - user.js: yahoo.homepage.dontask - true
============= SERVICES / DRIVERS ===============
.
R1 SAVRT;SAVRT;c:\program files\symantec antivirus\savrt.sys [2006-9-6 337592]
R1 SAVRTPEL;SAVRTPEL;c:\program files\symantec antivirus\Savrtpel.sys [2006-9-6 54968]
R2 ccEvtMgr;Symantec Event Manager;c:\program files\common files\symantec shared\ccEvtMgr.exe [2006-7-19 192160]
R2 ccSetMgr;Symantec Settings Manager;c:\program files\common files\symantec shared\ccSetMgr.exe [2006-7-19 169632]
R2 fssfltr;FssFltr;c:\windows\system32\drivers\fssfltr_tdi.sys [2009-10-27 54752]
R2 NProtectService;Norton Unerase Protection;c:\program files\norton systemworks\norton utilities\NPROTECT.EXE [2009-10-27 135168]
R2 Symantec AntiVirus;Symantec AntiVirus;c:\program files\symantec antivirus\Rtvscan.exe [2006-9-27 1813232]
R3 EraserUtilRebootDrv;EraserUtilRebootDrv;c:\program files\common files\symantec shared\eengine\EraserUtilRebootDrv.sys [2011-4-1 102448]
R3 NAVENG;NAVENG;c:\progra~1\common~1\symant~1\virusd~1\20110423.002\naveng.sys [2011-4-23 86136]
R3 NAVEX15;NAVEX15;c:\progra~1\common~1\symant~1\virusd~1\20110423.002\navex15.sys [2011-4-23 1393144]
R3 qic157;qic157;c:\windows\system32\drivers\qic157.sys [2009-10-26 6016]
S3 clr_optimization_v4.0.20506_32;.NET Runtime Optimization Service v4.0.20506_X86;c:\windows\microsoft.net\framework\v4.0.20506\mscorsvw.exe [2009-5-6 104272]
S3 EraserUtilDrv11010;EraserUtilDrv11010;\??\c:\program files\common files\symantec shared\eengine\eraserutildrv11010.sys --> c:\program files\common files\symantec shared\eengine\EraserUtilDrv11010.sys [?]
S3 fsssvc;Windows Live Family Safety Service;c:\program files\windows live\family safety\fsssvc.exe [2009-8-5 704864]
S3 npggsvc;nProtect GameGuard Service;c:\windows\system32\gamemon.des -service --> c:\windows\system32\GameMon.des -service [?]
S3 SavRoam;SAVRoam;c:\program files\symantec antivirus\SavRoam.exe [2006-9-27 116464]
.
=============== Created Last 30 ================
.
2011-04-22 16:07:24 -------- d-----w- c:\docume~1\user\locals~1\applic~1\Trusteer
2011-04-22 15:58:13 -------- d-----w- c:\windows\system32\wbem\repository\FS
2011-04-22 15:58:13 -------- d-----w- c:\windows\system32\wbem\Repository
2011-04-22 04:00:17 -------- d-----w- c:\docume~1\user\applic~1\Trusteer
2011-04-22 04:00:11 -------- d-----w- c:\program files\Trusteer
2011-04-22 03:58:08 -------- d-----w- c:\docume~1\alluse~1\applic~1\Trusteer
2011-04-21 23:25:23 53248 ----a-w- c:\windows\system32\6to4v32.dll
2011-04-21 23:25:19 34816 ----a-w- c:\windows\system32\itlnfw32.dll
2011-04-21 23:25:19 215552 ----a-w- c:\windows\system32\itlpfw32.dll
2011-04-20 04:37:34 -------- d-----w- c:\docume~1\user\locals~1\applic~1\{14A884BB-57A8-45D0-A887-9F388313E24B}
2011-04-08 17:17:38 53816 ----a-w- c:\windows\system32\drivers\RapportKELL.sys
.
==================== Find3M ====================
.
2011-03-07 05:33:50 692736 ----a-w- c:\windows\system32\inetcomm.dll
2011-03-04 06:37:06 420864 ----a-w- c:\windows\system32\vbscript.dll
2011-03-03 13:21:11 1857920 ----a-w- c:\windows\system32\win32k.sys
2011-02-22 23:06:29 916480 ----a-w- c:\windows\system32\wininet.dll
2011-02-22 23:06:29 43520 ----a-w- c:\windows\system32\licmgr10.dll
2011-02-22 23:06:29 1469440 ------w- c:\windows\system32\inetcpl.cpl
2011-02-22 11:41:59 385024 ----a-w- c:\windows\system32\html.iec
2011-02-17 12:32:12 5120 ----a-w- c:\windows\system32\xpsp4res.dll
2011-02-15 12:56:39 290432 ----a-w- c:\windows\system32\atmfd.dll
2011-02-09 13:53:52 270848 ----a-w- c:\windows\system32\sbe.dll
2011-02-09 13:53:52 186880 ----a-w- c:\windows\system32\encdec.dll
2011-02-08 13:33:55 978944 ----a-w- c:\windows\system32\mfc42.dll
2011-02-08 13:33:55 974848 ----a-w- c:\windows\system32\mfc42u.dll
2011-02-02 07:58:35 2067456 ----a-w- c:\windows\system32\mstscax.dll
2011-01-27 11:57:06 677888 ----a-w- c:\windows\system32\mstsc.exe
.
=================== ROOTKIT ====================
.
Stealth MBR rootkit/Mebroot/Sinowal/TDL4 detector 0.4.2 by Gmer, http://www.gmer.net
Windows 5.1.2600 Disk: Maxtor_7Y250P0 rev.YAR41BW0 -> Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3
.
device: opened successfully
user: MBR read successfully
.
Disk trace:
called modules: ntoskrnl.exe CLASSPNP.SYS disk.sys ACPI.sys hal.dll >>UNKNOWN [0x8A6654F0]<<
_asm { PUSH EBP; MOV EBP, ESP; PUSH ECX; MOV EAX, [EBP+0x8]; CMP EAX, [0x8a66b7d0]; MOV EAX, [0x8a66b84c]; PUSH EBX; PUSH ESI; MOV ESI, [EBP+0xc]; MOV EBX, [ESI+0x60]; PUSH EDI; JNZ 0x20; MOV [EBP+0x8], EAX; }
1 nt!IofCallDriver[0x804E13B9] -> \Device\Harddisk0\DR0[0x8A691AB8]
3 CLASSPNP[0xF7637FD7] -> nt!IofCallDriver[0x804E13B9] -> \Device\00000069[0x8A68EF18]
5 ACPI[0xF75AE620] -> nt!IofCallDriver[0x804E13B9] -> [0x8A68D940]
\Driver\atapi[0x8A697B78] -> IRP_MJ_CREATE -> 0x8A6654F0
error: Read A device attached to the system is not functioning.
kernel: MBR read successfully
_asm { XOR AX, AX; MOV SS, AX; MOV SP, 0x7c00; STI ; PUSH AX; POP ES; PUSH AX; POP DS; CLD ; MOV SI, 0x7c1b; MOV DI, 0x61b; PUSH AX; PUSH DI; MOV CX, 0x1e5; REP MOVSB ; RETF ; MOV BP, 0x7be; MOV CL, 0x4; CMP [BP+0x0], CH; JL 0x2e; JNZ 0x3a; }
detected disk devices:
detected hooks:
\Driver\atapi DriverStartIo -> 0x8A66533B
user & kernel MBR OK
Warning: possible TDL3 rootkit infection !
.
============= FINISH: 10:34:01.59 ===============
Sorry, for the post , i was not able to edit the above.
I did some research and some of my other registry keys are altered, the same keys in the same way as the "TR/Alureon.DX.236"
the following is my S&D report. I removed some of it because this will only allow me to post 64000 characters.
--- Search result list ---
Click.GiftLoad: [SBI $89783858] User settings (Registry value, nothing done)
HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\Main\featurecontrol\FEATURE_BROWSER_EMULATION\svchost.exe
--- Spybot - Search & Destroy version: 1.6.2 (build: 20090126) ---
2009-01-26 blindman.exe (1.0.0.8)
2009-01-26 SDFiles.exe (1.6.1.7)
2009-01-26 SDMain.exe (1.0.0.6)
2009-01-26 SDShred.exe (1.0.2.5)
2009-01-26 SDUpdate.exe (1.6.0.12)
2009-01-26 SpybotSD.exe (1.6.2.46)
2009-03-05 TeaTimer.exe (1.6.6.32)
2010-05-12 unins000.exe (51.49.0.0)
2009-01-26 Update.exe (1.6.0.7)
2009-11-04 advcheck.dll (1.6.5.20)
2007-04-02 aports.dll (2.1.0.0)
2008-06-14 DelZip179.dll (1.79.11.1)
2009-01-26 SDHelper.dll (1.6.2.14)
2008-06-19 sqlite3.dll
2009-01-26 Tools.dll (2.1.6.10)
2009-01-16 UninsSrv.dll (1.0.0.0)
2011-03-18 Includes\Adware.sbi (*)
2011-03-22 Includes\AdwareC.sbi (*)
2010-08-13 Includes\Cookies.sbi (*)
2010-12-14 Includes\Dialer.sbi (*)
2011-03-08 Includes\DialerC.sbi (*)
2011-02-24 Includes\HeavyDuty.sbi (*)
2011-03-29 Includes\Hijackers.sbi (*)
2011-03-29 Includes\HijackersC.sbi (*)
2010-09-15 Includes\iPhone.sbi (*)
2010-12-14 Includes\Keyloggers.sbi (*)
2011-03-08 Includes\KeyloggersC.sbi (*)
2004-11-29 Includes\LSP.sbi (*)
2011-04-05 Includes\Malware.sbi (*)
2011-04-19 Includes\MalwareC.sbi (*)
2011-02-24 Includes\PUPS.sbi (*)
2011-03-15 Includes\PUPSC.sbi (*)
2010-01-25 Includes\Revision.sbi (*)
2009-01-13 Includes\Security.sbi (*)
2011-03-08 Includes\SecurityC.sbi (*)
2008-06-03 Includes\Spybots.sbi (*)
2008-06-03 Includes\SpybotsC.sbi (*)
2011-02-24 Includes\Spyware.sbi (*)
2011-03-15 Includes\SpywareC.sbi (*)
2010-03-08 Includes\Tracks.uti (*)
2010-12-28 Includes\Trojans.sbi (*)
2011-04-20 Includes\TrojansC-02.sbi (*)
2011-04-18 Includes\TrojansC-03.sbi (*)
2011-04-18 Includes\TrojansC-04.sbi (*)
2011-04-11 Includes\TrojansC-05.sbi (*)
2011-03-08 Includes\TrojansC.sbi (*)
2008-03-04 Plugins\Chai.dll
2008-03-05 Plugins\Fennel.dll
2008-02-26 Plugins\Mate.dll
2007-12-24 Plugins\TCPIPAddress.dll
This is not a complete list i tried to fit what i could.
Last edited by tashi; 2011-04-24 at 03:10.
Reason: Merged two posts, snipped SB log as only the top is required :-)
-


Please read Before You Post
While best efforts are made to assist in removing infections safely, unexpected stuff can happen. It is advisable that you back up your important data before starting any clean up procedure. Neither Safer Networking Forums nor the Analyst providing the advice may be held responsible for any loss.
Until we deem your system clean I am going to ask you not to install or uninstall any software or hardware except for the programs we may run.
Your infected with a nasty Rootkit , I am going to ask you to run TDSSKiller but the variant you have may prevent it from running and if thats the case we will use another method to remove it
Please download TDSSKiller.zip- Extract it to your desktop
- Double click TDSSKiller.exe
- Press Start Scan
- Only if Malicious objects are found then ensure Cure is selected
- Then click Continue > Reboot now
- Copy and paste the log in your next reply
- A copy of the log will be saved automatically to the root of the drive (typically C:\)
-

great your online. and May i Thank you once again for your help. You where right The TDSSkiller did not work.
Also after i attemptted it i restarted my computer and got this Spy bot SD mesage:
Process ID 208
Scchost.exe
C:\\Windows\system32\win32.Shark.bw
This has a very severe threat level if i am correct.
his backdoor is related to the other problem?
thanks. I will disconnect my internt and leav it only connected when i check this forum.
-

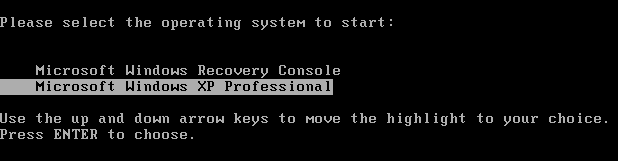
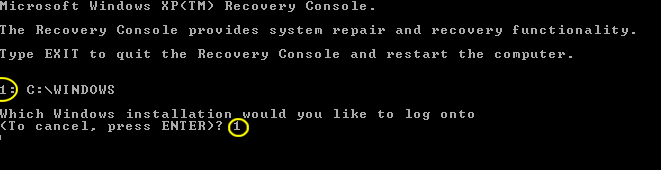
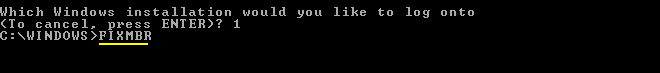
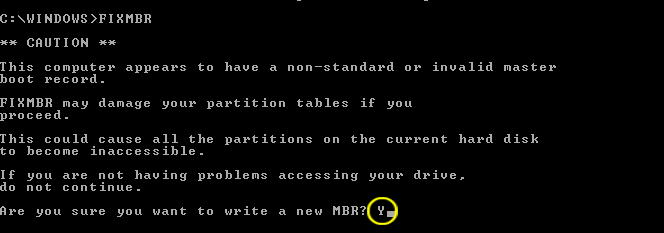
Whats going on is your Master Boot Record is infected, I need you to run Combofix, when Combofix runs it will check to see if you have a Recovery Console and if not it will prompt you to install one, do so because we are going to need to fix your MBR through the Recovery Console
Download Combofix from any of the links below. You must rename it before saving it. Save it to your desktop.
Link 1
Link 2


* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:
Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply.
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
-
-

before it is actually saved it has to be renamed "Combo-Fix" correct? do i need to add an extension such as "exe" ?
-

ComboFix 11-04-25.02 - User 04/25/2011 18:33:20.1.2 - x86
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2046.1304 [GMT -7:00]
Running from: c:\documents and settings\User\Desktop\Combo-Fix.exe
AV: Symantec AntiVirus Corporate Edition *Disabled/Updated* {FB06448E-52B8-493A-90F3-E43226D3305C}
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\p18_812875.dll
c:\documents and settings\All Users\Application Data\Toolbar4
c:\documents and settings\User\Application Data\logs.dat
c:\documents and settings\User\Local Settings\Application Data\{14A884BB-57A8-45D0-A887-9F388313E24B}
c:\documents and settings\User\Local Settings\Application Data\{14A884BB-57A8-45D0-A887-9F388313E24B}\chrome.manifest
c:\documents and settings\User\Local Settings\Application Data\{14A884BB-57A8-45D0-A887-9F388313E24B}\chrome\content\_cfg.js
c:\documents and settings\User\Local Settings\Application Data\{14A884BB-57A8-45D0-A887-9F388313E24B}\chrome\content\overlay.xul
c:\documents and settings\User\Local Settings\Application Data\{14A884BB-57A8-45D0-A887-9F388313E24B}\install.rdf
c:\documents and settings\User\WINDOWS
c:\program files\Search Toolbar
c:\program files\Search Toolbar\basis.xml
c:\program files\Search Toolbar\bg.bmp
c:\program files\Search Toolbar\bing_logo.png
c:\program files\Search Toolbar\celebrity.png
c:\program files\Search Toolbar\drop_images.png
c:\program files\Search Toolbar\drop_maps.png
c:\program files\Search Toolbar\drop_news.png
c:\program files\Search Toolbar\drop_videos.png
c:\program files\Search Toolbar\drop_web.png
c:\program files\Search Toolbar\facebook.png
c:\program files\Search Toolbar\favicon.png
c:\program files\Search Toolbar\games.png
c:\program files\Search Toolbar\hotmail.png
c:\program files\Search Toolbar\icon.ico
c:\program files\Search Toolbar\images.png
c:\program files\Search Toolbar\include.xml
c:\program files\Search Toolbar\info.txt
c:\program files\Search Toolbar\lifestyle.png
c:\program files\Search Toolbar\maps.png
c:\program files\Search Toolbar\messenger.png
c:\program files\Search Toolbar\msn.png
c:\program files\Search Toolbar\news.png
c:\program files\Search Toolbar\SearchToolbar.dll
c:\program files\Search Toolbar\SearchToolbarUninstall.exe
c:\program files\Search Toolbar\tbcore3.dll
c:\program files\Search Toolbar\tbhelper.dll
c:\program files\Search Toolbar\twitter.png
c:\program files\Search Toolbar\uninstall.exe
c:\program files\Search Toolbar\update.exe
c:\program files\Search Toolbar\version.txt
c:\program files\Search Toolbar\video.png
c:\program files\Search Toolbar\videos.png
c:\program files\Search Toolbar\weather.png
c:\program files\Search Toolbar\web.png
c:\windows\Install
c:\windows\system32\certstore.dat
c:\windows\system32\itlnfw32.dll
c:\windows\wuasirvy.dll
.
Infected copy of c:\windows\system32\clipsrv.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\clipsrv.exe
.
Infected copy of c:\windows\system32\alg.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\alg.exe
.
Infected copy of c:\windows\system32\cisvc.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\cisvc.exe
.
Infected copy of c:\windows\system32\dllhost.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\dllhost.exe
.
Infected copy of c:\windows\system32\dmadmin.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\dmadmin.exe
.
Infected copy of c:\windows\system32\imapi.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\imapi.exe
.
Infected copy of c:\windows\system32\locator.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\locator.exe
.
Infected copy of c:\windows\system32\mnmsrvc.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\mnmsrvc.exe
.
Infected copy of c:\windows\system32\msdtc.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\msdtc.exe
.
Infected copy of c:\windows\system32\msiexec.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\msiexec.exe
.
Infected copy of c:\windows\system32\netdde.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\netdde.exe
.
Infected copy of c:\windows\system32\rsvp.exe was found and disinfected
Restored copy from - c:\windows\system32\dllcache\rsvp.exe
.
Infected copy of c:\windows\system32\scardsvr.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\scardsvr.exe
.
Infected copy of c:\windows\system32\sessmgr.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\sessmgr.exe
.
Infected copy of c:\windows\system32\smlogsvc.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\smlogsvc.exe
.
Infected copy of c:\windows\system32\tlntsvr.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\tlntsvr.exe
.
Infected copy of c:\windows\system32\ups.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\ups.exe
.
Infected copy of c:\windows\system32\vssvc.exe was found and disinfected
Restored copy from - c:\windows\ServicePackFiles\i386\vssvc.exe
.
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
-------\Legacy_MYWEBSEARCHSERVICE
.
.
((((((((((((((((((((((((( Files Created from 2011-03-26 to 2011-04-26 )))))))))))))))))))))))))))))))
.
.
2011-04-26 01:52 . 2011-04-26 01:52 63115 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\USERTILE.JS
2011-04-26 01:52 . 2011-04-26 01:52 4599 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\UIRESOURCE.JS
2011-04-26 01:52 . 2011-04-26 01:52 9310 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\TEXTBOX.JS
2011-04-26 01:52 . 2011-04-26 01:52 8646 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\TILEBOX.JS
2011-04-26 01:52 . 2011-04-26 01:52 6429 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\UICORE.JS
2011-04-26 01:52 . 2011-04-26 01:52 5927 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\TEXT.JS
2011-04-26 01:52 . 2011-04-26 01:52 8613 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\SAVEDUSER.JS
2011-04-26 01:52 . 2011-04-26 01:52 1651 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\QUERYSTRING.JS
2011-04-26 01:52 . 2011-04-26 01:52 6910 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\NEWUSERCOMM.JS
2011-04-26 01:52 . 2011-04-26 01:52 6208 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\LINK.JS
2011-04-26 01:52 . 2011-04-26 01:52 18541 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\LOCALIZATION.JS
2011-04-26 01:52 . 2011-04-26 01:52 8288 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\IMAGE.JS
2011-04-26 01:51 . 2011-04-26 01:51 51852 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\EXTERNALWRAPPER.JS
2011-04-26 01:51 . 2011-04-26 01:51 20719 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\DIVWRAPPER.JS
2011-04-26 01:51 . 2011-04-26 01:51 23327 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\COMBOBOX.JS
2011-04-26 01:51 . 2011-04-26 01:51 8782 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\BUTTON.JS
2011-04-26 01:51 . 2011-04-26 01:51 7271 ----a-w- c:\documents and settings\All Users\Application Data\Microsoft\IdentityCRL\production\temp\wlidui_WLIDSVC\CHECKBOX.JS
2011-04-23 22:01 . 2011-04-23 22:01 -------- d-----w- c:\program files\Safer Networking
2011-04-23 17:23 . 2011-04-23 17:23 -------- d-----w- c:\program files\ERUNT
2011-04-23 00:39 . 2011-04-23 00:39 -------- d-----w- c:\documents and settings\Administrator.INTEL\Application Data\Trusteer
2011-04-22 16:07 . 2011-04-22 16:07 -------- d-----w- c:\documents and settings\User\Local Settings\Application Data\Trusteer
2011-04-22 15:58 . 2011-04-22 15:58 -------- d-----w- c:\windows\system32\wbem\Repository
2011-04-22 05:30 . 2011-04-22 05:30 -------- d-----w- c:\documents and settings\LocalService\Application Data\AdobeUM
2011-04-22 05:29 . 2011-04-22 05:30 -------- d-----w- c:\documents and settings\LocalService\Local Settings\Application Data\Adobe
2011-04-22 04:00 . 2011-04-22 04:00 -------- d-----w- c:\documents and settings\User\Application Data\Trusteer
2011-04-22 04:00 . 2011-04-22 04:00 -------- d-----w- c:\program files\Trusteer
2011-04-22 03:58 . 2011-04-22 03:58 -------- d-----w- c:\documents and settings\All Users\Application Data\Trusteer
2011-04-22 03:42 . 2011-04-22 03:42 -------- d-----w- c:\documents and settings\NetworkService\Application Data\AdobeUM
2011-04-20 15:52 . 2011-04-22 03:42 -------- d-----w- c:\documents and settings\NetworkService\Local Settings\Application Data\Adobe
2011-04-19 20:35 . 2008-04-14 00:12 26624 ----a-w- c:\documents and settings\LocalService\Application Data\Microsoft\UPnP Device Host\upnphost\udhisapi.dll
2011-04-16 03:50 . 2011-04-16 03:50 -------- d-----w- c:\documents and settings\User\Application Data\EPSON
2011-04-08 17:17 . 2011-04-08 17:17 53816 ----a-w- c:\windows\system32\drivers\RapportKELL.sys
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2011-04-26 01:53 . 2004-08-04 07:56 400384 ----a-w- c:\windows\system32\vssvc.exe
2011-04-26 01:53 . 2004-08-04 07:56 129024 ----a-w- c:\windows\system32\ups.exe
2011-04-26 01:53 . 2004-08-04 07:56 183808 ----a-w- c:\windows\system32\tlntsvr.exe
2011-04-26 01:53 . 2004-08-04 07:56 200192 ----a-w- c:\windows\system32\smlogsvc.exe
2011-04-26 01:53 . 2004-08-04 07:56 206336 ----a-w- c:\windows\system32\scardsvr.exe
2011-04-26 01:53 . 2004-08-04 07:56 185856 ----a-w- c:\windows\system32\locator.exe
2011-04-26 01:52 . 2004-08-04 07:56 221696 ----a-w- c:\windows\system32\netdde.exe
2011-04-26 01:52 . 2009-10-27 06:55 116736 ----a-w- c:\windows\system32\msdtc.exe
2011-04-26 01:52 . 2004-08-04 07:56 143872 ----a-w- c:\windows\system32\clipsrv.exe
2011-04-26 01:52 . 2004-08-04 07:56 116224 ----a-w- c:\windows\system32\cisvc.exe
2011-04-26 01:52 . 2004-08-04 07:56 155136 ----a-w- c:\windows\system32\alg.exe
2011-03-07 05:33 . 2009-10-27 06:57 692736 ----a-w- c:\windows\system32\inetcomm.dll
2011-03-04 06:37 . 2004-08-04 07:56 420864 ----a-w- c:\windows\system32\vbscript.dll
2011-03-03 13:21 . 2004-08-03 23:17 1857920 ----a-w- c:\windows\system32\win32k.sys
2011-02-22 23:06 . 2004-08-04 07:56 1469440 ------w- c:\windows\system32\inetcpl.cpl
2011-02-22 23:06 . 2004-08-04 07:56 916480 ----a-w- c:\windows\system32\wininet.dll
2011-02-22 23:06 . 2004-08-04 07:56 43520 ----a-w- c:\windows\system32\licmgr10.dll
2011-02-22 11:41 . 2004-08-03 22:59 385024 ----a-w- c:\windows\system32\html.iec
2011-02-17 13:18 . 2004-08-03 23:15 455936 ----a-w- c:\windows\system32\drivers\mrxsmb.sys
2011-02-17 13:18 . 2004-08-03 23:14 357888 ----a-w- c:\windows\system32\drivers\srv.sys
2011-02-17 12:32 . 2009-10-27 11:12 5120 ----a-w- c:\windows\system32\xpsp4res.dll
2011-02-15 12:56 . 2004-08-04 07:56 290432 ----a-w- c:\windows\system32\atmfd.dll
2011-02-09 13:53 . 2004-08-04 07:56 270848 ----a-w- c:\windows\system32\sbe.dll
2011-02-09 13:53 . 2004-08-04 07:56 186880 ----a-w- c:\windows\system32\encdec.dll
2011-02-08 13:33 . 2004-08-04 07:56 978944 ----a-w- c:\windows\system32\mfc42.dll
2011-02-08 13:33 . 2004-08-04 07:56 974848 ----a-w- c:\windows\system32\mfc42u.dll
2011-02-02 07:58 . 2009-10-27 06:55 2067456 ----a-w- c:\windows\system32\mstscax.dll
2011-01-27 11:57 . 2009-10-27 06:55 677888 ----a-w- c:\windows\system32\mstsc.exe
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\1TortoiseNormal]
@="{C5994560-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994560-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\2TortoiseModified]
@="{C5994561-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994561-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\3TortoiseConflict]
@="{C5994562-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994562-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\4TortoiseLocked]
@="{C5994563-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994563-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\5TortoiseReadOnly]
@="{C5994564-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994564-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\6TortoiseDeleted]
@="{C5994565-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994565-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\7TortoiseAdded]
@="{C5994566-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994566-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\8TortoiseIgnored]
@="{C5994567-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994567-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\9TortoiseUnversioned]
@="{C5994568-53D9-4125-87C9-F193FC689CB2}"
[HKEY_CLASSES_ROOT\CLSID\{C5994568-53D9-4125-87C9-F193FC689CB2}]
2009-08-14 02:55 85768 ----a-w- c:\program files\Common Files\TortoiseOverlays\TortoiseOverlays.dll
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-05 2260480]
"Rapportexe"="c:\program files\Trusteer\Rapport\bin\RapportService.exe" [2011-04-08 1550136]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SoundMAXPnP"="c:\program files\Analog Devices\SoundMAX\SMax4PNP.exe" [2004-07-27 1388544]
"ccApp"="c:\program files\Common Files\Symantec Shared\ccApp.exe" [2006-07-20 52896]
"vptray"="c:\progra~1\SYMANT~1\VPTray.exe" [2006-09-28 125168]
"Acrobat Assistant 7.0"="c:\program files\Adobe\Acrobat 7.0\Distillr\Acrotray.exe" [2008-04-23 483328]
"ArcSoft Connection Service"="c:\program files\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe" [2010-10-28 207424]
"SunJavaUpdateSched"="c:\program files\Common Files\Java\Java Update\jusched.exe" [2010-02-18 248040]
"iTunesHelper"="c:\program files\iTunes\iTunesHelper.exe" [2010-09-01 421160]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2010-09-08 421888]
.
c:\documents and settings\User\Start Menu\Programs\Startup\
ERUNT AutoBackup.lnk - c:\program files\ERUNT\AUTOBACK.EXE [2005-10-20 38912]
.
c:\documents and settings\All Users\Start Menu\Programs\Startup\
Adobe Acrobat Speed Launcher.lnk - c:\windows\Installer\{AC76BA86-1033-0000-7760-100000000002}\SC_Acrobat.exe [2009-10-27 25214]
.
[hkey_local_machine\software\microsoft\windows\currentversion\explorer\ShellExecuteHooks]
"{0cab0400-7395-11d0-a5e5-0020afe2fdd9}"= "qvphook.dll" [2002-04-10 45056]
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\SymantecAntiVirus]
"DisableMonitoring"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Windows Live\\Sync\\WindowsLiveSync.exe"=
"c:\\WINDOWS\\system32\\sessmgr.exe"=
"c:\\Program Files\\Windows Live\\Messenger\\wlcsdk.exe"=
"c:\\Program Files\\Windows Live\\Messenger\\msnmsgr.exe"=
"c:\\WINDOWS\\Downloaded Program Files\\ijjiOptimizer.exe"=
"c:\\WINDOWS\\Downloaded Program Files\\PurpleBean.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"58954:TCP"= 58954:TCP:Pando Media Booster
"58954:UDP"= 58954:UDP:Pando Media Booster
.
R2 NProtectService;Norton Unerase Protection;c:\program files\Norton SystemWorks\Norton Utilities\NPROTECT.EXE [10/27/2009 1:33 AM 135168]
R3 EraserUtilRebootDrv;EraserUtilRebootDrv;c:\program files\Common Files\Symantec Shared\EENGINE\EraserUtilRebootDrv.sys [4/1/2011 8:02 PM 102448]
R3 qic157;qic157;c:\windows\system32\drivers\qic157.sys [10/26/2009 12:34 PM 6016]
S3 clr_optimization_v4.0.20506_32;.NET Runtime Optimization Service v4.0.20506_X86;c:\windows\Microsoft.NET\Framework\v4.0.20506\mscorsvw.exe [5/6/2009 10:08 AM 104272]
S3 EraserUtilDrv11010;EraserUtilDrv11010;\??\c:\program files\Common Files\Symantec Shared\EENGINE\EraserUtilDrv11010.sys --> c:\program files\Common Files\Symantec Shared\EENGINE\EraserUtilDrv11010.sys [?]
S3 npggsvc;nProtect GameGuard Service;c:\windows\system32\GameMon.des -service --> c:\windows\system32\GameMon.des -service [?]
S3 SavRoam;SAVRoam;c:\program files\Symantec AntiVirus\SavRoam.exe [9/27/2006 9:33 PM 116464]
.
Contents of the 'Scheduled Tasks' folder
.
2010-06-29 c:\windows\Tasks\AppleSoftwareUpdate.job
- c:\program files\Apple Software Update\SoftwareUpdate.exe [2008-07-30 20:34]
.
2011-04-09 c:\windows\Tasks\Norton SystemWorks One Button Checkup.job
- c:\program files\Norton SystemWorks\OBC.exe [2002-08-30 05:30]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.google.com/
mStart Page = hxxp://www.att.net
uInternet Settings,ProxyOverride = *.local
IE: Convert link target to Adobe PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert link target to existing PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert selected links to Adobe PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
IE: Convert selected links to existing PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Convert selection to Adobe PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert selection to existing PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert to Adobe PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert to existing PDF - c:\program files\Adobe\Acrobat 7.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
FF - ProfilePath - c:\documents and settings\User\Application Data\Mozilla\Firefox\Profiles\ljvrwzqo.default\
FF - Ext: Default: {972ce4c6-7e08-4474-a285-3208198ce6fd} - c:\program files\Mozilla Firefox\extensions\{972ce4c6-7e08-4474-a285-3208198ce6fd}
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\Microsoft.NET\Framework\v4.0.20506\WPF\DotNetAssistantExtension
FF - Ext: Java Quick Starter: jqs@sun.com - c:\program files\Java\jre6\lib\deploy\jqs\ff
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - %profile%\extensions\{20a82645-c095-46ed-80e3-08825760534b}
FF - Ext: ReloadEvery: {888d99e7-e8b5-46a3-851e-1ec45da1e644} - %profile%\extensions\{888d99e7-e8b5-46a3-851e-1ec45da1e644}
FF - Ext: Web Developer: {c45c406e-ab73-11d8-be73-000a95be3b12} - %profile%\extensions\{c45c406e-ab73-11d8-be73-000a95be3b12}
FF - Ext: Clear Cache Button: {563e4790-7e70-11da-a72b-0800200c9a66} - %profile%\extensions\{563e4790-7e70-11da-a72b-0800200c9a66}
FF - Ext: Torbutton: {e0204bd5-9d31-402b-a99d-a6aa8ffebdca} - %profile%\extensions\{e0204bd5-9d31-402b-a99d-a6aa8ffebdca}
FF - user.js: yahoo.homepage.dontask - true
.
- - - - ORPHANS REMOVED - - - -
.
Toolbar-{0C8413C1-FAD1-446C-8584-BE50576F863E} - c:\program files\Search Toolbar\tbcore3.dll
WebBrowser-{D4027C7F-154A-4066-A1AD-4243D8127440} - (no file)
WebBrowser-{0C8413C1-FAD1-446C-8584-BE50576F863E} - c:\program files\Search Toolbar\tbcore3.dll
AddRemove-Yahoo! BrowserPlus - c:\documents and settings\User\Local Settings\Application Data\Yahoo!\BrowserPlus\BrowserPlusUninstaller.exe
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2011-04-25 18:52
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
Stealth MBR rootkit/Mebroot/Sinowal/TDL4 detector 0.4.2 by Gmer, http://www.gmer.net
Windows 5.1.2600 Disk: Maxtor_7Y250P0 rev.YAR41BW0 -> Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3
.
device: opened successfully
user: MBR read successfully
error: Read A device attached to the system is not functioning.
kernel: MBR read successfully
detected disk devices:
detected hooks:
\Driver\atapi DriverStartIo -> 0x8A66633B
user & kernel MBR OK
.
**************************************************************************
.
[HKEY_LOCAL_MACHINE\System\ControlSet003\Services\npggsvc]
"ImagePath"="c:\windows\system32\GameMon.des -service"
.
--------------------- DLLs Loaded Under Running Processes ---------------------
.
- - - - - - - > 'winlogon.exe'(688)
c:\windows\system32\WININET.dll
.
- - - - - - - > 'lsass.exe'(748)
c:\windows\system32\WININET.dll
.
- - - - - - - > 'explorer.exe'(3252)
c:\windows\system32\WININET.dll
.
------------------------ Other Running Processes ------------------------
.
c:\program files\Common Files\Symantec Shared\ccSetMgr.exe
c:\program files\Common Files\Symantec Shared\ccEvtMgr.exe
c:\program files\Common Files\Symantec Shared\SPBBC\SPBBCSvc.exe
c:\program files\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
c:\program files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
c:\program files\Bonjour\mDNSResponder.exe
c:\program files\Symantec AntiVirus\DefWatch.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\program files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE
c:\windows\system32\msiexec.exe
c:\windows\system32\sessmgr.exe
c:\program files\Microsoft\Search Enhancement Pack\SeaPort\SeaPort.exe
c:\program files\Analog Devices\SoundMAX\SMAgent.exe
c:\progra~1\NORTON~1\SPEEDD~1\nopdb.exe
c:\program files\Symantec AntiVirus\Rtvscan.exe
c:\program files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE
c:\program files\Canon\CAL\CALMAIN.exe
c:\program files\Common Files\Microsoft Shared\Windows Live\WLIDSvcM.exe
c:\windows\system32\wbem\wmiapsrv.exe
c:\program files\TortoiseSVN\bin\TSVNCache.exe
c:\program files\Common Files\ArcSoft\Connection Service\Bin\ArcCon.ac
c:\program files\iPod\bin\iPodService.exe
.
**************************************************************************
.
Completion time: 2011-04-25 19:00:33 - machine was rebooted
ComboFix-quarantined-files.txt 2011-04-26 02:00
.
Pre-Run: 186,559,680,512 bytes free
Post-Run: 187,589,365,760 bytes free
.
WindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /noexecute=optin /fastdetect
[spybotsd]
timeout.old=30
.
- - End Of File - - 355F0270281334F237357C2A4E659BE0
-

anything on what changes to registry to allow Spybot to change?
-
-

Done. 
Tags for this Thread
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules
.
- c:\program files\java\jre6\lib\deploy\jqs\ff