-
 Frustrated with repeated infection NEED HELP
Frustrated with repeated infection NEED HELP
Hi. I hope I've followed the proper steps here. I have cleaned up the XP anti virus 2011, XP antimalware 2012 , and other variation at least 6 times, and just when it seems like I've got it licked, it pops up again, usually when I'm out of town and my kids are on the computer.
I have used Rkill, FixNCR and TDSSkiller during these multiple attempts to rid myself of these bugs. Also malwarebytes, and microsoft security essentials and spybot.
I need help to get to the root problem. Thanks. Here is the dds.txt I am having a bit of trouble figuring out how to comress and add the attach.txt file, it is not that large, and could copy and past. Seems smaller than the dds.txt file. I'll wait for instruction to do so.
Thanks. T
.
DDS (Ver_2011-08-26.01) - NTFSx86
Internet Explorer: 8.0.6001.18702 BrowserJavaVersion: 1.6.0_26
Run by Customer at 10:27:28 on 2011-12-19
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2038.1483 [GMT -6:00]
.
AV: Microsoft Security Essentials *Enabled/Updated* {EDB4FA23-53B8-4AFA-8C5D-99752CCA7095}
.
============== Running Processes ===============
.
C:\WINDOWS\system32\svchost -k DcomLaunch
svchost.exe
c:\Program Files\Microsoft Security Client\Antimalware\MsMpEng.exe
C:\WINDOWS\System32\svchost.exe -k netsvcs
svchost.exe
svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
svchost.exe
C:\Program Files\Broadcom\ASFIPMon\AsfIpMon.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\WINDOWS\system32\igfxpers.exe
C:\Program Files\Analog Devices\Core\smax4pnp.exe
C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
C:\Program Files\Common Files\Java\Java Update\jusched.exe
C:\Program Files\Lexmark 2300 Series\lxcgmon.exe
C:\Program Files\Microsoft Security Client\msseces.exe
C:\Program Files\TaskSwitchXP\TaskSwitchXP.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe
C:\WINDOWS\system32\lxcgcoms.exe
C:\Program Files\Common Files\Java\Java Update\jucheck.exe
C:\Program Files\FinalMediaPlayer\FMPCheckForUpdates.exe
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://www.google.com/
uURLSearchHooks: UrlSearchHook Class: {00000000-6e41-4fd3-8538-502f5495e5fc} - c:\program files\ask.com\GenericAskToolbar.dll
uURLSearchHooks: YTNavAssist.YTNavAssistPlugin Class: {81017ea9-9aa8-4a6a-9734-7af40e7d593f} - c:\program files\yahoo!\companion\installs\cpn0\YTNavAssist.dll
mWinlogon: SfcDisable=-99 (0xffffff9d)
mWinlogon: UIHost=XPize_Logon.exe
BHO: &Yahoo! Toolbar Helper: {02478d38-c3f9-4efb-9b51-7695eca05670} - c:\program files\yahoo!\companion\installs\cpn0\yt.dll
BHO: Adobe PDF Link Helper: {18df081c-e8ad-4283-a596-fa578c2ebdc3} - c:\program files\common files\adobe\acrobat\activex\AcroIEHelperShim.dll
BHO: Spybot-S&D IE Protection: {53707962-6f74-2d53-2644-206d7942484f} - c:\progra~1\spybot~1\SDHelper.dll
BHO: Google Toolbar Helper: {aa58ed58-01dd-4d91-8333-cf10577473f7} - c:\program files\google\google toolbar\GoogleToolbar_32.dll
BHO: Google Toolbar Notifier BHO: {af69de43-7d58-4638-b6fa-ce66b5ad205d} - c:\program files\google\googletoolbarnotifier\5.7.7018.1622\swg.dll
BHO: Ask Toolbar: {d4027c7f-154a-4066-a1ad-4243d8127440} - c:\program files\ask.com\GenericAskToolbar.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {dbc80044-a445-435b-bc74-9c25c1c588a9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl Class: {e7e6f031-17ce-4c07-bc86-eabfe594f69c} - c:\program files\java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
BHO: Yontoo Layers: {fd72061e-9fde-484d-a58a-0bab4151cad8} - c:\program files\yontoo layers runtime\YontooIEClient.dll
BHO: SingleInstance Class: {fdad4da1-61a2-4fd8-9c17-86f7ac245081} - c:\program files\yahoo!\companion\installs\cpn0\YTSingleInstance.dll
TB: Ask Toolbar: {d4027c7f-154a-4066-a1ad-4243d8127440} - c:\program files\ask.com\GenericAskToolbar.dll
TB: Yahoo! Toolbar: {ef99bd32-c1fb-11d2-892f-0090271d4f88} - c:\program files\yahoo!\companion\installs\cpn0\yt.dll
TB: Google Toolbar: {2318c2b1-4965-11d4-9b18-009027a5cd4f} - c:\program files\google\google toolbar\GoogleToolbar_32.dll
uRun: [TaskSwitchXP] c:\program files\taskswitchxp\TaskSwitchXP.exe
uRun: [ctfmon.exe] c:\windows\system32\ctfmon.exe
uRun: [OM2_Monitor] "c:\program files\olympus\olympus master 2\MMonitor.exe" -NoStart
uRun: [swg] "c:\program files\google\googletoolbarnotifier\GoogleToolbarNotifier.exe"
mRun: [igfxpers] c:\windows\system32\igfxpers.exe
mRun: [SoundMAXPnP] c:\program files\analog devices\core\smax4pnp.exe
mRun: [Adobe ARM] "c:\program files\common files\adobe\arm\1.0\AdobeARM.exe"
mRun: [SunJavaUpdateSched] "c:\program files\common files\java\java update\jusched.exe"
mRun: [lxcgmon.exe] "c:\program files\lexmark 2300 series\lxcgmon.exe"
mRun: [FaxCenterServer] "c:\program files\lexmark fax solutions\fm3032.exe" /s
mRun: [LXCGCATS] rundll32 c:\windows\system32\spool\drivers\w32x86\3\LXCGtime.dll,_RunDLLEntry@16
mRun: [MSC] "c:\program files\microsoft security client\msseces.exe" -hide -runkey
dRun: [TaskSwitchXP] c:\program files\taskswitchxp\TaskSwitchXP.exe
dRunOnce: [nltide_3] rundll32 advpack.dll,LaunchINFSectionEx nLite.inf,C,,4,N
uPolicies-explorer: NoSMConfigurePrograms = 1 (0x1)
mPolicies-system: DisableCAD = 1 (0x1)
dPolicies-explorer: NoSMHelp = 1 (0x1)
dPolicies-explorer: ForceClassicControlPanel = 1 (0x1)
dPolicies-explorer: NoSMConfigurePrograms = 1 (0x1)
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {FB5F1910-F110-11d2-BB9E-00C04F795683} - c:\program files\messenger\msmsgs.exe
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\progra~1\spybot~1\SDHelper.dll
LSP: mswsock.dll
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_26-windows-i586.cab
DPF: {9191F686-7F0A-441D-8A98-2FE3AC1BD913} - hxxp://acs.pandasoftware.com/activescan/cabs/as2stubie.cab
DPF: {CAFEEFAC-0016-0000-0026-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_26-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_26-windows-i586.cab
TCP: DhcpNameServer = 68.115.71.53 68.113.206.10 66.189.0.100
TCP: Interfaces\{3214AEA9-EA8E-464D-A799-898AC30BD94D} : DhcpNameServer = 68.115.71.53 68.113.206.10 66.189.0.100
Notify: igfxcui - igfxdev.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\wpdshserviceobj.dll
Hosts: 127.0.0.1 www.spywareinfo.com
.
================= FIREFOX ===================
.
FF - ProfilePath - c:\documents and settings\customer\application data\mozilla\firefox\profiles\gjtiigq7.default\
FF - plugin: c:\program files\adobe\reader 10.0\reader\air\nppdf32.dll
FF - plugin: c:\program files\google\update\1.3.21.79\npGoogleUpdate3.dll
FF - plugin: c:\program files\java\jre6\bin\new_plugin\npdeployJava1.dll
FF - plugin: c:\program files\mozilla firefox\plugins\npdeployJava1.dll
.
---- FIREFOX POLICIES ----
FF - user.js: extentions.y2layers.installId - 15c823d4-f91b-4a8a-be3f-9d7e8c08246a
FF - user.js: extentions.y2layers.defaultEnableAppsList - Buzzdock,BuzzdockTease,DropDownDeals,DropDownDeals,
.
============= SERVICES / DRIVERS ===============
.
R0 pavboot;pavboot;c:\windows\system32\drivers\pavboot.sys [2011-11-27 28552]
R1 MpFilter;Microsoft Malware Protection Driver;c:\windows\system32\drivers\MpFilter.sys [2011-4-18 165648]
R1 MpKsl0ff5d91a;MpKsl0ff5d91a;c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{7819fcb6-56ba-4980-92fc-3702c9ccbdb8}\MpKsl0ff5d91a.sys [2011-12-19 29904]
R2 ASFIPmon;Broadcom ASF IP Monitor;c:\program files\broadcom\asfipmon\AsfIpMon.exe [2005-3-8 61440]
S1 MpKsl9608db61;MpKsl9608db61;\??\c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{9614342f-6495-4bfb-b11a-759a21ffa7ba}\mpksl9608db61.sys --> c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{9614342f-6495-4bfb-b11a-759a21ffa7ba}\MpKsl9608db61.sys [?]
S1 MpKsle6849be9;MpKsle6849be9;\??\c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{910340c3-0871-4046-b821-53d085c08f6e}\mpksle6849be9.sys --> c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{910340c3-0871-4046-b821-53d085c08f6e}\MpKsle6849be9.sys [?]
S2 gupdate;Google Update Service (gupdate);c:\program files\google\update\GoogleUpdate.exe [2011-8-3 136176]
S3 gupdatem;Google Update Service (gupdatem);c:\program files\google\update\GoogleUpdate.exe [2011-8-3 136176]
.
=============== Created Last 30 ================
.
2011-12-19 14:13:40 29904 ----a-w- c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{7819fcb6-56ba-4980-92fc-3702c9ccbdb8}\MpKsl0ff5d91a.sys
2011-12-19 14:13:25 56200 ----a-w- c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{7819fcb6-56ba-4980-92fc-3702c9ccbdb8}\offreg.dll
2011-12-19 14:13:18 6823496 ----a-w- c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\{7819fcb6-56ba-4980-92fc-3702c9ccbdb8}\mpengine.dll
2011-12-19 13:40:57 -------- d-----w- c:\windows\system32\wbem\repository\FS
2011-12-19 13:40:57 -------- d-----w- c:\windows\system32\wbem\Repository
2011-12-09 15:33:26 6823496 ----a-w- c:\documents and settings\all users\application data\microsoft\microsoft antimalware\definition updates\backup\mpengine.dll
2011-12-09 04:00:06 -------- d-----w- c:\program files\Spybot - Search & Destroy
2011-12-09 04:00:06 -------- d-----w- c:\documents and settings\all users\application data\Spybot - Search & Destroy
2011-12-09 00:42:28 -------- d-----w- c:\program files\Microsoft Security Client
2011-12-09 00:40:51 -------- d--h--w- c:\windows\system32\GroupPolicy
2011-12-03 20:20:00 -------- d-----w- c:\documents and settings\customer\local settings\application data\OLYMPUS
2011-12-03 20:19:20 -------- d-----w- c:\program files\OLYMPUS
2011-11-27 16:16:58 28552 ----a-w- c:\windows\system32\drivers\pavboot.sys
2011-11-27 16:16:38 -------- d-----w- c:\program files\Panda Security
2011-11-21 15:31:36 -------- d-----w- c:\documents and settings\customer\application data\uvD2onF4a
2011-11-21 15:31:36 -------- d-----w- c:\documents and settings\customer\application data\c7fEL8gTZjCkVzN
2011-11-21 14:05:54 -------- d-----w- c:\documents and settings\customer\application data\t4amH6sWKfLgXjC
2011-11-21 14:05:54 -------- d-----w- c:\documents and settings\customer\application data\IUVelOBtz0c1v3n
2011-11-21 14:03:15 22216 ----a-w- c:\windows\system32\drivers\mbam.sys
2011-11-21 13:44:42 -------- d-----w- c:\documents and settings\customer\application data\lNyxA1uvSoFpGsJ
2011-11-21 13:44:42 -------- d-----w- c:\documents and settings\customer\application data\GdE8gRZqhXUrOtP
2011-11-20 16:51:22 -------- d-----w- c:\documents and settings\customer\application data\e6dEK8gRZhXkVlB
2011-11-20 16:51:21 -------- d-----w- c:\documents and settings\customer\application data\WWK8fRZ9hXjVlBz
2011-11-20 05:43:43 221184 ----a-w- c:\windows\system32\wmpns.dll
2011-11-20 00:47:10 270848 ------w- c:\windows\system32\dllcache\sbe.dll
2011-11-20 00:47:10 186880 ------w- c:\windows\system32\dllcache\encdec.dll
2011-11-20 00:47:05 99840 ------w- c:\windows\system32\dllcache\srvsvc.dll
2011-11-20 00:47:01 90112 ------w- c:\windows\system32\dllcache\wshext.dll
2011-11-20 00:47:01 180224 ------w- c:\windows\system32\dllcache\scrobj.dll
2011-11-20 00:47:01 172032 ------w- c:\windows\system32\dllcache\scrrun.dll
2011-11-20 00:47:01 155648 ------w- c:\windows\system32\dllcache\wscript.exe
2011-11-20 00:47:01 135168 ------w- c:\windows\system32\dllcache\cscript.exe
2011-11-20 00:45:42 617472 ------w- c:\windows\system32\dllcache\comctl32.dll
2011-11-20 00:45:24 40960 ------w- c:\windows\system32\dllcache\ndproxy.sys
2011-11-20 00:44:57 139656 ------w- c:\windows\system32\dllcache\rdpwd.sys
2011-11-20 00:44:40 105472 ------w- c:\windows\system32\dllcache\mup.sys
2011-11-20 00:43:51 10496 ------w- c:\windows\system32\dllcache\ndistapi.sys
2011-11-20 00:43:42 45568 ------w- c:\windows\system32\dllcache\wab.exe
2011-11-19 18:58:56 -------- d-----w- c:\windows\pss
2011-11-19 17:07:04 -------- d-----w- c:\program files\Ask.com
2011-11-19 17:07:04 -------- d-----w- c:\documents and settings\customer\local settings\application data\AskToolbar
2011-11-19 17:07:02 -------- d-----w- c:\program files\Abbyy FineReader 6.0 Sprint
.
==================== Find3M ====================
.
2011-12-17 15:25:37 75264 ----a-w- c:\windows\system32\drivers\ipsec.sys
2011-12-08 22:47:20 138496 ----a-w- c:\windows\system32\drivers\afd.sys
2011-11-23 13:25:32 1859584 ----a-w- c:\windows\system32\win32k.sys
2011-11-15 20:29:56 222080 ------w- c:\windows\system32\MpSigStub.exe
2011-11-04 19:20:51 916992 ----a-w- c:\windows\system32\wininet.dll
2011-11-04 19:20:51 43520 ----a-w- c:\windows\system32\licmgr10.dll
2011-11-04 19:20:51 1469440 ------w- c:\windows\system32\inetcpl.cpl
2011-11-04 11:23:59 385024 ----a-w- c:\windows\system32\html.iec
2011-11-01 16:07:10 1288704 ----a-w- c:\windows\system32\ole32.dll
2011-10-28 05:31:48 33280 ----a-w- c:\windows\system32\csrsrv.dll
2011-10-25 13:37:08 2148864 ----a-w- c:\windows\system32\ntoskrnl.exe
2011-10-25 12:52:02 2027008 ----a-w- c:\windows\system32\ntkrnlpa.exe
2011-10-18 11:13:22 186880 ----a-w- c:\windows\system32\encdec.dll
2011-10-10 14:22:41 692736 ----a-w- c:\windows\system32\inetcomm.dll
2011-09-28 07:06:50 599040 ----a-w- c:\windows\system32\crypt32.dll
2011-09-26 17:41:20 611328 ----a-w- c:\windows\system32\uiautomationcore.dll
2011-09-26 17:41:20 220160 ----a-w- c:\windows\system32\oleacc.dll
2011-09-26 17:41:14 20480 ----a-w- c:\windows\system32\oleaccrc.dll
.
============= FINISH: 10:28:11.29 ===============
-

Hi and Welcome!!  My name is Jeff. I would be more than happy to take a look at your malware results logs and help you with solving any malware problems you might have. Logs can take a while to research, so please be patient and know that I am working hard to get you a clean and functional system back in your hands. I'd be grateful if you would note the following:
My name is Jeff. I would be more than happy to take a look at your malware results logs and help you with solving any malware problems you might have. Logs can take a while to research, so please be patient and know that I am working hard to get you a clean and functional system back in your hands. I'd be grateful if you would note the following:- I will be working on your Malware issues, this may or may not, solve other issues you have with your machine.
- Please subscribe to this topic, if you haven't already. You can subscribe by clicking the Watch Topic button to the right of your topic title and then choosing the notification method ( Recommended: Inmediate Notification)
- The fixes are specific to your problem and should only be used for the issues on this machine.
- Please continue to review my answers until I tell you your machine appears to be clear. Absence of symptoms does not mean that everything is clear.
- It's often worth reading through these instructions and printing them for ease of reference.
- If you don't know or understand something, please don't hesitate to say or ask!! It's better to be sure and safe than sorry.
- Please reply to this thread. Do not start a new topic.
IMPORTANT NOTE : Please do not delete anything unless instructed to.
DO NOT use any TOOLS such as Combofix or HijackThis fixes without supervision.
Doing so could make your system inoperable and could require a full reinstall of your OS losing all your programs and data.
Vista and Windows 7 users:
These tools MUST be run from the executable (.exe) every time you run them
with Admin Rights (Right click, choose "Run as Administrator")
Stay with this topic until I give you the all clean post.
----------
**WARNING**Unfortunately one or more of the infections I have identified are Backdoor Trojans, IRCBots or other Malware capable of stealing very important information. You need to stop using all Internet Banking sites, change passwords to all sites with sensitive information from a clean computer and phone your bank to inform them that you may be a victim of identify theft. More often than not, we advise users that a full reinstallation of their Operating System is the only way to ensure that their computer will ever be 100% clean again.
Unfortunately I have found what is known as the ZeroAccess rootkit on your system. It is an especially nasty infection that can take quite some time to clean as well as may have damaged your system files itself. As a warning, during the cleaning (if you choose to do so) you may lose internet access with this computer and in the end we may need to reinstall the operating system anyway depending on the extent of the infection.
If you would like to format and reinstall your Operating System please let me know and I can assist you with that.
If you would like to continue with the cleaning, please continue with the following instructions and I will be more than happy to help. 
----------
GMER
Download GMER Rootkit Scanner from here or here.
- Extract the contents of the zipped file to desktop.
- Double click GMER.exe. If asked to allow gmer.sys driver to load, please consent .
- If it gives you a warning about rootkit activity and asks if you want to run scan...click on NO.
Click the image to enlarge it
- In the right panel, you will see several boxes that have been checked. Uncheck the following ...
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "Gmer.txt" or it will save as a .log file which cannot be uploaded to your post.
- Save it where you can easily find it, such as your desktop, and attach it in your reply.
**Caution**
Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries.
----------
Please download TDSSKiller.zip
- Extract it to your desktop
- Double click TDSSKiller.exe
- Press Start Scan
- Only if Malicious objects are found then ensure Cure is selected
- Then click Continue > Reboot now
- Copy and paste the log in your next reply
- A copy of the log will be saved automatically to the root of the drive (typically C:\)
----------
Download ComboFix from one of these locations:
Link 1
Link 2
* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. Note: If you are having difficulty properly disabling your protective programs, or are unsure as to what programs need to be disabled, please refer to the information available through this link : How to Disable your Security Programs
- Double click on ComboFix.exe & follow the prompts.
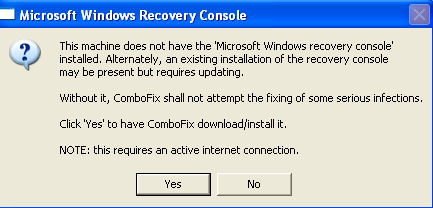
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.
Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply.
Notes:
1.Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. ComboFix may reset a number of Internet Explorer's settings, including making I-E the default browser.
3. CF disconnects your machine from the internet. The connection is automatically restored before CF completes its run. If CF runs into difficulty and terminates prematurely, the connection can be manually restored by restarting your machine.
----------
If you have chose to continue with cleaning please post the logs created by GMER, TDSSKiller and ComboFix. 
-
 Thanks for quick reply
Thanks for quick reply
Hi thanks for your help. I will not be home until later today and will follow your first instructions as soon as I can.
T
-

Hi,
Thanks for letting me know. 
-
 GMER.txt
GMER.txt
Hi Jeff. Tried and could not find the watch topic button anywhere. It's probably right under my nose, but got stumped on that one right away.
Here is the GMER.txt. This was a long scan.
Crap. I saved it to my desktop, but not there or anywhere else to be found. Will do it again.
-

Hi,
At the top of your topic you will see a Topic Tool button >> Press that and then select to Subscribe. 
------------
You may try to find the GMER log in the Downloads folder as it may have gone there.
-----------
Don't worry about running it (GMER) again right yet. Just when you get TDSSKiller and ComboFix run post those logs.
-
 Gmer.txt
Gmer.txt
Here we go, I hope this thing is attached. Thanks. Now on to tdsskiller.
-
 TDSSKiller can't copy
TDSSKiller can't copy
Ran TDSSkiller. Says found no problems, but when I have the report on the screen, I cannot copy. Right click does not bring up any menu box or prompts at all.
-
 TDSSKILLER screenshots
TDSSKILLER screenshots
Hi sorry, this is the only way I could think of to get the tdsskiller report on here. There are 11 screenshots, and these are the last five. More on next post.
-
 tdsskiller screenshots 2
tdsskiller screenshots 2
should be one more left the first screenshot.
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules



 My name is Jeff. I would be more than happy to take a look at your malware results logs and help you with solving any malware problems you might have. Logs can take a while to research, so please be patient and know that I am working hard to get you a clean and functional system back in your hands. I'd be grateful if you would note the following:
My name is Jeff. I would be more than happy to take a look at your malware results logs and help you with solving any malware problems you might have. Logs can take a while to research, so please be patient and know that I am working hard to get you a clean and functional system back in your hands. I'd be grateful if you would note the following: