-
 "Windows Care" called me about my freezing up problem!
"Windows Care" called me about my freezing up problem!
A foreign sounding man called me at home and said he was from Windows Care, calling about my freezing up problem. I have had this freezing up problem since early December. Didn't trust him but did a few things he said:
In RUN I typed eventvwr where he showed me the errors showing up.
In RUN I typed cmd then assoc where he proceeded to read me off my "my computer security number"...all but the last two numbers which I wouldn't read to him. He said he knew they were xx but I wouldn't tell him anything. He started getting mad so I told him to get lost.
My computer is freezing up and I am disturbed that he had my unlisted phone number.
I ran spybot (but I couldn't get to safe mode) but didn't know what was bad or not to remove. I did remove:
Freeze.com, GoForFiles, and Google Chrome from my add/remove programs.
After that I printed out and read instructions on this site.
I have downloaded Spybot, ERUNT, DDS Log, aswMBR, and hijackthis.
I sure would appreciate help in cleaning out my computer.
Thanks.
Michele
DDS (Ver_2012-11-20.01) - NTFS_x86
Internet Explorer: 8.0.6001.18702
Run by Owner at 22:38:09 on 2012-12-22
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.1983.1496 [GMT -6:00]
.
AV: avast! Antivirus *Enabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
.
============== Running Processes ================
.
C:\Program Files\AVAST Software\Avast\AvastSvc.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
C:\Program Files\Bonjour\mDNSResponder.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\Program Files\Google\Update\GoogleUpdate.exe
C:\Program Files\CDBurnerXP\NMSAccessU.exe
C:\Program Files\Spybot - Search & Destroy 2\SDFSSvc.exe
C:\Program Files\Spybot - Search & Destroy 2\SDUpdSvc.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\system32\wscntfy.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\VTtrayp.exe
C:\WINDOWS\system32\VTTimer.exe
C:\program files\real\realplayer\update\realsched.exe
C:\Program Files\iTunes\iTunesHelper.exe
C:\Program Files\AVAST Software\Avast\avastUI.exe
C:\WINDOWS\RTHDCPL.EXE
C:\Program Files\Common Files\Java\Java Update\jusched.exe
C:\Program Files\Spybot - Search & Destroy 2\SDTray.exe
C:\Program Files\iPod\bin\iPodService.exe
C:\WINDOWS\system32\wbem\wmiprvse.exe
C:\WINDOWS\System32\svchost.exe -k netsvcs
C:\WINDOWS\System32\svchost.exe -k NetworkService
C:\WINDOWS\System32\svchost.exe -k LocalService
C:\WINDOWS\System32\svchost.exe -k LocalService
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxps://www.google.com/
uDefault_Page_URL = hxxp://www.msn.com
mWinlogon: Userinit = c:\windows\system32\userinit.exe
BHO: Adobe PDF Link Helper: {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - c:\program files\common files\adobe\acrobat\activex\AcroIEHelperShim.dll
BHO: RealPlayer Download and Record Plugin for Internet Explorer: {3049C3E9-B461-4BC5-8870-4C09146192CA} - c:\documents and settings\all users\application data\real\realplayer\browserrecordplugin\ie\rpbrowserrecordplugin.dll
BHO: Spybot-S&D IE Protection: {53707962-6F74-2D53-2644-206D7942484F} - c:\program files\spybot - search & destroy 2\SDHelper.dll
BHO: Java(tm) Plug-In SSV Helper: {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - c:\program files\java\jre6\bin\ssv.dll
BHO: avast! WebRep: {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - c:\program files\avast software\avast\aswWebRepIE.dll
BHO: Google Toolbar Helper: {AA58ED58-01DD-4d91-8333-CF10577473F7} - c:\program files\google\google toolbar\GoogleToolbar_32.dll
BHO: Google Toolbar Notifier BHO: {AF69DE43-7D58-4638-B6FA-CE66B5AD205D} - c:\program files\google\googletoolbarnotifier\5.7.8313.1002\swg.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {DBC80044-A445-435b-BC74-9C25C1C588A9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl Class: {E7E6F031-17CE-4C07-BC86-EABFE594F69C} - c:\program files\java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
TB: Google Toolbar: {2318C2B1-4965-11D4-9B18-009027A5CD4F} - c:\program files\google\google toolbar\GoogleToolbar_32.dll
TB: avast! WebRep: {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - c:\program files\avast software\avast\aswWebRepIE.dll
TB: Google Toolbar: {2318C2B1-4965-11d4-9B18-009027A5CD4F} - c:\program files\google\google toolbar\GoogleToolbar_32.dll
EB: {32683183-48a0-441b-a342-7c2a440a9478} - <orphaned>
mRun: [VTTrayp] VTtrayp.exe
mRun: [VTTimer] VTTimer.exe
mRun: [SMSERIAL] sm56hlpr.exe
mRun: [SkyTel] SkyTel.EXE
mRun: [TkBellExe] "c:\program files\real\realplayer\update\realsched.exe" -osboot
mRun: [QuickTime Task] "c:\program files\quicktime\qttask.exe" -atboottime
mRun: [iTunesHelper] "c:\program files\itunes\iTunesHelper.exe"
mRun: [Adobe ARM] "c:\program files\common files\adobe\arm\1.0\AdobeARM.exe"
mRun: [avast] "c:\program files\avast software\avast\avastUI.exe" /nogui
mRun: [RTHDCPL] RTHDCPL.EXE
mRun: [Alcmtr] ALCMTR.EXE
mRun: [SunJavaUpdateSched] "c:\program files\common files\java\java update\jusched.exe"
mRun: [SDTray] "c:\program files\spybot - search & destroy 2\SDTray.exe"
dRunOnce: [RunNarrator] Narrator.exe
dRunOnce: [AutoLaunch] c:\program files\lavasoft\ad-aware\AutoLaunch.exe monthly
uPolicies-Explorer: NoDriveTypeAutoRun = dword:145
mPolicies-Windows\System: Allow-LogonScript-NetbiosDisabled = dword:1
mPolicies-Explorer: NoDriveTypeAutoRun = dword:145
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\program files\spybot - search & destroy 2\SDHelper.dll
.
INFO: HKCU has more than 50 listed domains.
If you wish to scan all of them, select the 'Force scan all domains' option.
.
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_37-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0007-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_07-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0020-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_20-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0037-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_37-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_37-windows-i586.cab
TCP: NameServer = 192.168.1.1
TCP: Interfaces\{41C246EC-EDEB-4581-8F34-6727F5A5B550} : DHCPNameServer = 192.168.1.1
Handler: belarc - {6318E0AB-2E93-11D1-B8ED-00608CC9A71F} - c:\program files\belarc\advisor\system\BAVoilaX.dll
Notify: SDWinLogon - SDWinLogon.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\WPDShServiceObj.dll
.
============= SERVICES / DRIVERS ===============
.
R1 aswSnx;aswSnx;c:\windows\system32\drivers\aswSnx.sys [2012-4-5 738504]
R1 aswSP;aswSP;c:\windows\system32\drivers\aswSP.sys [2012-4-5 361032]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [2012-4-5 21256]
R2 avast! Antivirus;avast! Antivirus;c:\program files\avast software\avast\AvastSvc.exe [2012-4-5 44808]
R2 SDScannerService;Spybot-S&D 2 Scanner Service;c:\program files\spybot - search & destroy 2\SDFSSvc.exe [2012-12-22 1103392]
R2 SDUpdateService;Spybot-S&D 2 Updating Service;c:\program files\spybot - search & destroy 2\SDUpdSvc.exe [2012-12-22 1369624]
S2 SDWSCService;Spybot-S&D 2 Security Center Service;c:\program files\spybot - search & destroy 2\SDWSCSvc.exe [2012-12-22 168384]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;\??\c:\program files\lavasoft\ad-aware\kernexplorer.sys --> c:\program files\lavasoft\ad-aware\KernExplorer.sys [?]
S3 USB-100;Realtek RTL8150 USB 10/100 Fast Ethernet Adapter;c:\windows\system32\drivers\RTL8150.SYS [2009-4-2 27519]
.
=============== Created Last 30 ================
.
2012-12-22 16:23:57 15224 ----a-w- c:\windows\system32\sdnclean.exe
2012-12-22 16:23:42 -------- d-----w- c:\program files\Spybot - Search & Destroy 2
2012-12-22 14:20:53 -------- d-----w- C:\tdsskiller
.
==================== Find3M ====================
.
2012-11-15 12:31:08 73728 ----a-w- c:\windows\system32\javacpl.cpl
2012-11-15 12:31:07 477168 ----a-w- c:\windows\system32\npdeployJava1.dll
2012-11-15 12:31:07 473072 ----a-w- c:\windows\system32\deployJava1.dll
2012-10-30 23:51:58 738504 ----a-w- c:\windows\system32\drivers\aswSnx.sys
2012-10-30 23:51:07 41224 ----a-w- c:\windows\avastSS.scr
2009-01-21 16:14:40 9780224 -c--a-w- c:\program files\openofficeorg30.msi
2002-03-11 09:06:30 1822520 -c--a-w- c:\program files\instmsiw.exe
2002-03-11 08:45:04 1708856 -c--a-w- c:\program files\instmsia.exe
.
============= FINISH: 22:38:50.70 ===============
aswMBR version 0.9.9.1707 Copyright(c) 2011 AVAST Software
Run date: 2012-12-22 22:41:16
-----------------------------
22:41:16.937 OS Version: Windows 5.1.2600 Service Pack 3
22:41:16.937 Number of processors: 1 586 0x409
22:41:16.937 ComputerName: MICHELLE-3WVINT UserName: Owner
22:41:17.921 Initialize success
22:41:18.171 AVAST engine defs: 12122201
22:41:23.562 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3
22:41:23.562 Disk 0 Vendor: WDC_WD1600AAJS-08B4A0 01.03A01 Size: 152627MB BusType: 3
22:41:23.609 Disk 0 MBR read successfully
22:41:23.625 Disk 0 MBR scan
22:41:23.625 Disk 0 Windows XP default MBR code
22:41:23.625 Disk 0 Partition 1 80 (A) 07 HPFS/NTFS NTFS 152617 MB offset 63
22:41:23.625 Disk 0 scanning sectors +312560640
22:41:23.687 Disk 0 scanning C:\WINDOWS\system32\drivers
22:41:32.015 Service scanning
22:41:43.375 Modules scanning
22:41:47.687 Disk 0 trace - called modules:
22:41:47.703 ntkrnlpa.exe CLASSPNP.SYS disk.sys ACPI.sys hal.dll atapi.sys pciide.sys PCIIDEX.SYS
22:41:47.703 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x89d39ab8]
22:41:48.218 3 CLASSPNP.SYS[ba8e8fd7] -> nt!IofCallDriver -> \Device\00000068[0x89d7ff18]
22:41:48.218 5 ACPI.sys[ba77f620] -> nt!IofCallDriver -> \Device\Ide\IdeDeviceP0T0L0-3[0x89d45940]
22:41:48.640 AVAST engine scan C:\WINDOWS
22:41:55.921 AVAST engine scan C:\WINDOWS\system32
22:44:11.687 AVAST engine scan C:\WINDOWS\system32\drivers
22:44:27.390 AVAST engine scan C:\Documents and Settings\Owner
22:45:09.234 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\Owner\Desktop\MBR.dat"
22:45:09.265 The log file has been saved successfully to "C:\Documents and Settings\Owner\Desktop\aswMBR.txt"
-

Hi and  Michele2012
Michele2012 
My name is Robybel.
I would be more than happy to take a look at your log and help you with solving any malware problems you might have. Logs can take a while to research, so please be patient and know that I am working hard to get you a clean and functional system back in your hands. I'd be grateful if you would note the following:- I will be working on your Malware issues, this may or may not, solve other issues you have with your machine.
- The fixes are specific to your problem and should only be used for the issues on this machine.
- Please continue to review my answers until I tell you your machine appears to be clear. Absence of symptoms does not mean that everything is clear.
- It's often worth reading through these instructions and printing them for ease of reference.
- If you don't know or understand something, please don't hesitate to say or ask!! It's better to be sure and safe than sorry.
- Please reply to this thread. Do not start a new topic.
Please be adviced, as I am still in training, all my replies to you will be checked for accuracy by one of our experts to ensure that I am giving you the best possible advise, this will be a team effort.
This may cause a delay, but I will do my best to keep it as short as possible. Please bear with me, I will post back to you as soon as I can.
IMPORTANT NOTE : Please do not delete, download or install anything unless instructed to do so.
DO NOT use any TOOLS such as Combofix or HijackThis fixes without supervision. Doing so could make your system inoperable and could require a full reinstall of your Operating System and losing all your programs and data.
Vista and Windows 7 users:
These tools MUST be run from the executable. (.exe) every time you run them
with Admin Rights (Right click, choose "Run as Administrator")
Stay with this topic until I give you the all clean post.
Having said that....Let's get going!!
-
 Thank you
Thank you
Thank you. I won't touch anything until instructed. I am not a computer whiz so please make instructions as detailed as possible. Michele
-

Hi michele2012, sorry for the delay.
First of all: Happy Holidays. 
That phone call was a scam, you were right to tell him to get lost.
very good
Now, follow these steps
Please post Attach.txt, which you can find in the same location of DDS.txt
Next
Download Security Check by screen317 from here or here.- Save it to your Desktop.
- Double click SecurityCheck.exe and follow the onscreen instructions inside of the black box.
- A Notepad document should open automatically called checkup.txt; please post the contents of that document.
Next
AdwCleaner
- Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool.
- Click on Delete.
- Confirm each time with Ok.
- Your computer will be rebooted automatically. A text file will open after the restart.
- Please post the content of that logfile with your next answer.
- You can find the logfile at C:\AdwCleaner[S1].txt as well.
On your next reply please post :
- Attach.txt
- Security check report
- AdwCleaner log
Let me know if you have any problems in performing with the steps above or any questions you may have.
Good Day!
-

Dear Robybel--I appreciate you taking the time to help me and your easy-to-follow instructions. Happy Holidays to you also. Following is what you asked for:
.
UNLESS SPECIFICALLY INSTRUCTED, DO NOT POST THIS LOG.
IF REQUESTED, ZIP IT UP & ATTACH IT
.
DDS (Ver_2012-11-20.01)
.
Microsoft Windows XP Home Edition
Boot Device: \Device\HarddiskVolume1
Install Date: 4/2/2009 12:23:51 PM
System Uptime: 12/22/2012 7:57:36 PM (3 hours ago)
.
Motherboard: ASUSTeK Computer INC. | | P5VD2-MX SE
Processor: Intel(R) Celeron(R) CPU 2.80GHz | CPU 1 | 2800/133mhz
.
==== Disk Partitions =========================
.
A: is Removable
C: is FIXED (NTFS) - 149 GiB total, 26.318 GiB free.
D: is CDROM ()
F: is Removable
.
==== Disabled Device Manager Items =============
.
Class GUID: {4D36E96D-E325-11CE-BFC1-08002BE10318}
Description: Motorola SM56 Speakerphone Modem
Device ID: PCI\VEN_1057&DEV_5608&SUBSYS_00001057&REV_00\3&267A616A&0&48
Manufacturer: Motorola Inc
Name: Motorola SM56 Speakerphone Modem
PNP Device ID: PCI\VEN_1057&DEV_5608&SUBSYS_00001057&REV_00\3&267A616A&0&48
Service: Modem
.
Class GUID:
Description:
Device ID: ACPI\ATK0110\1010110
Manufacturer:
Name:
PNP Device ID: ACPI\ATK0110\1010110
Service:
.
==== System Restore Points ===================
.
RP258: 12/2/2012 3:22:05 PM - System Checkpoint
RP259: 12/5/2012 2:48:35 PM - System Checkpoint
RP260: 12/6/2012 8:00:42 PM - System Checkpoint
RP261: 12/10/2012 9:33:41 PM - System Checkpoint
RP262: 12/16/2012 1:50:24 PM - System Checkpoint
RP263: 12/22/2012 11:41:16 AM - Removed NetAssistant
RP264: 12/22/2012 11:57:07 AM - working on computer freeze up problem
.
==== Installed Programs ======================
.
Adobe AIR
Adobe Flash Player 11 ActiveX
Adobe Flash Player 11 Plugin
Adobe Reader X (10.1.0)
Amazon Kindle
Apple Application Support
Apple Mobile Device Support
Apple Software Update
Avant Browser (remove only)
avast! Free Antivirus
Belarc Advisor 7.2
Bonjour
CCleaner
CDBurnerXP
Cook'n Collection
Critical Update for Windows Media Player 11 (KB959772)
DVD Suite
ERUNT 1.1j
Google Toolbar for Internet Explorer
Google Update Helper
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB953595)
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB958484)
Hotfix for Windows Media Format 11 SDK (KB929399)
Hotfix for Windows Media Player 11 (KB939683)
Hotfix for Windows XP (KB952287)
Hotfix for Windows XP (KB954550-v5)
Hotfix for Windows XP (KB961118)
InstaCodecs
iTunes
Java Auto Updater
Java(TM) 6 Update 20
Java(TM) 6 Update 37
Java(TM) 6 Update 7
Malwarebytes' Anti-Malware
Microsoft .NET Framework 1.1
Microsoft .NET Framework 1.1 Hotfix (KB928366)
Microsoft .NET Framework 2.0 Service Pack 2
Microsoft .NET Framework 3.0 Service Pack 2
Microsoft .NET Framework 3.5 SP1
Microsoft Access 2000 SR-1
Microsoft Base Smart Card Cryptographic Service Provider Package
Microsoft Compression Client Pack 1.0 for Windows XP
Microsoft Excel 2000 SR-1
Microsoft Internationalized Domain Names Mitigation APIs
Microsoft National Language Support Downlevel APIs
Microsoft Silverlight
Microsoft User-Mode Driver Framework Feature Pack 1.0
Microsoft Visual C++ 2005 Redistributable
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.17
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148
Microsoft Word 2000 SR-1
MSXML 4.0 SP2 (KB954430)
neroxml
Octoshape add-in for Adobe Flash Player
OpenOffice.org 3.2
PDFKey Pro
Platform
PowerDVD
PowerProducer
QuickTime
RealNetworks - Microsoft Visual C++ 2008 Runtime
RealPlayer
Realtek High Definition Audio Driver
RealUpgrade 1.1
Security Update for Windows Internet Explorer 7 (KB938127-v2)
Security Update for Windows Internet Explorer 7 (KB961260)
Security Update for Windows Internet Explorer 7 (KB963027)
Security Update for Windows Internet Explorer 8 (KB2618444)
Security Update for Windows Internet Explorer 8 (KB2744842)
Security Update for Windows Internet Explorer 8 (KB982381)
Security Update for Windows Media Player (KB952069)
Security Update for Windows Media Player 11 (KB936782)
Security Update for Windows Media Player 11 (KB954154)
Security Update for Windows XP (KB923561)
Security Update for Windows XP (KB923789)
Security Update for Windows XP (KB938464-v2)
Security Update for Windows XP (KB941569)
Security Update for Windows XP (KB946648)
Security Update for Windows XP (KB950760)
Security Update for Windows XP (KB950762)
Security Update for Windows XP (KB950974)
Security Update for Windows XP (KB951066)
Security Update for Windows XP (KB951376-v2)
Security Update for Windows XP (KB951698)
Security Update for Windows XP (KB951748)
Security Update for Windows XP (KB952004)
Security Update for Windows XP (KB952954)
Security Update for Windows XP (KB954459)
Security Update for Windows XP (KB954600)
Security Update for Windows XP (KB955069)
Security Update for Windows XP (KB956572)
Security Update for Windows XP (KB956802)
Security Update for Windows XP (KB956803)
Security Update for Windows XP (KB956841)
Security Update for Windows XP (KB957097)
Security Update for Windows XP (KB958215)
Security Update for Windows XP (KB958644)
Security Update for Windows XP (KB958687)
Security Update for Windows XP (KB958690)
Security Update for Windows XP (KB959426)
Security Update for Windows XP (KB960225)
Security Update for Windows XP (KB960714)
Security Update for Windows XP (KB960715)
Security Update for Windows XP (KB960803)
Security Update for Windows XP (KB961373)
Security Update for Windows XP (KB979309)
Spybot - Search & Destroy
TaxCut Basic 2007
Update for Windows Internet Explorer 8 (KB2598845)
Update for Windows XP (KB2467659)
Update for Windows XP (KB951978)
Update for Windows XP (KB955839)
Update for Windows XP (KB967715)
VIA Platform Device Manager
VIA Rhine-Family Fast-Ethernet Adapter
VIA/S3G Display Driver
Visual C++ 2008 x86 Runtime - (v9.0.30729)
Visual C++ 2008 x86 Runtime - v9.0.30729.01
WebFldrs XP
Windows Genuine Advantage Validation Tool (KB892130)
Windows Internet Explorer 7
Windows Internet Explorer 8
Windows Media Format 11 runtime
Windows Media Player 11
Windows PowerShell(TM) 1.0
Windows XP Service Pack 3
Xvid 1.2.1 final uninstall
Yahoo! Detect
.
==== Event Viewer Messages From Past Week ========
.
12/22/2012 10:24:18 AM, error: Service Control Manager [7009] - Timeout (30000 milliseconds) waiting for the Spybot-S&D 2 Security Center Service service to connect.
12/22/2012 10:24:18 AM, error: Service Control Manager [7000] - The Spybot-S&D 2 Security Center Service service failed to start due to the following error: The service did not respond to the start or control request in a timely fashion.
12/18/2012 10:20:28 AM, error: Service Control Manager [7023] - The Application Management service terminated with the following error: The specified module could not be found.
12/18/2012 10:20:24 AM, error: W32Time [17] - Time Provider NtpClient: An error occurred during DNS lookup of the manually configured peer 'time.windows.com,0x1'. NtpClient will try the DNS lookup again in 15 minutes. The error was: A socket operation was attempted to an unreachable host. (0x80072751)
.
==== End Of File ===========================
Results of screen317's Security Check version 0.99.56
Windows XP Service Pack 3 x86
Internet Explorer 8
``````````````Antivirus/Firewall Check:``````````````
Windows Firewall Enabled!
avast! Free Antivirus
`````````Anti-malware/Other Utilities Check:`````````
Spybot - Search & Destroy
CCleaner
Java(TM) 6 Update 20
Java(TM) 6 Update 37
Java(TM) 6 Update 7
Java version out of Date!
Adobe Flash Player 11.3.300.271
Adobe Reader 10.1.0 Adobe Reader out of Date!
````````Process Check: objlist.exe by Laurent````````
Spybot Teatimer.exe is disabled!
AVAST Software Avast AvastSvc.exe
AVAST Software Avast avastUI.exe
`````````````````System Health check`````````````````
Total Fragmentation on Drive C:: 6%
````````````````````End of Log``````````````````````
# AdwCleaner v2.103 - Logfile created 12/27/2012 at 11:02:50
# Updated 25/12/2012 by Xplode
# Operating system : Microsoft Windows XP Service Pack 3 (32 bits)
# User : Owner - MICHELLE-3WVINT
# Boot Mode : Normal
# Running from : C:\Documents and Settings\Owner\Desktop\adwcleaner.exe
# Option [Delete]
***** [Services] *****
***** [Files / Folders] *****
Folder Deleted : C:\Documents and Settings\Owner\Application Data\PriceGong
Folder Deleted : C:\Documents and Settings\Owner\Local Settings\Application Data\Conduit
Folder Deleted : C:\Documents and Settings\Owner\Local Settings\Application Data\ConduitEngine
Folder Deleted : C:\Program Files\ConduitEngine
***** [Registry] *****
Key Deleted : HKCU\Software\Conduit
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Settings\{E38FA08E-F56A-4169-ABF5-5C71E3C153A1}
Key Deleted : HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E38FA08E-F56A-4169-ABF5-5C71E3C153A1}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\{D2083641-E57F-4EAB-BB85-0582424F4A29}
Key Deleted : HKLM\SOFTWARE\Classes\AppID\NCTAudioCDGrabber2.DLL
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{CADAF6BE-BF50-4669-8BFD-C27BD4E6181B}
Key Deleted : HKLM\Software\Conduit
Key Deleted : HKLM\Software\Freeze.com
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\clickpotatolitesa
***** [Internet Browsers] *****
-\\ Internet Explorer v8.0.6001.18702
[OK] Registry is clean.
-\\ Google Chrome v [Unable to get version]
File : C:\Documents and Settings\Owner\Local Settings\Application Data\Google\Chrome\User Data\Default\Preferences
[OK] File is clean.
*************************
AdwCleaner[S1].txt - [1710 octets] - [27/12/2012 11:02:50]
########## EOF - C:\AdwCleaner[S1].txt - [1770 octets] ##########
-
-

ComboFix 12-12-28.02 - Owner 12/28/2012 7:33.1.1 - x86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.1983.1397 [GMT -6:00]
Running from: c:\documents and settings\Owner\Desktop\ComboFix.exe
AV: avast! Antivirus *Disabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
* Created a new restore point
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\documents and settings\All Users\Application Data\TEMP
c:\documents and settings\Owner\WINDOWS
c:\program files\Internet Explorer\SET1247.tmp
c:\program files\Internet Explorer\SET1248.tmp
c:\program files\Internet Explorer\SET1249.tmp
c:\program files\Internet Explorer\SET34.tmp
c:\program files\Internet Explorer\SET35.tmp
c:\program files\Internet Explorer\SET36.tmp
c:\windows\system32\SET1258.tmp
c:\windows\system32\SET1259.tmp
c:\windows\system32\SET125A.tmp
c:\windows\system32\SET125B.tmp
c:\windows\system32\SET125C.tmp
c:\windows\system32\SET125D.tmp
c:\windows\system32\SET125E.tmp
c:\windows\system32\SET125F.tmp
c:\windows\system32\SET1260.tmp
c:\windows\system32\SET1261.tmp
c:\windows\system32\SET1262.tmp
c:\windows\system32\SET1263.tmp
c:\windows\system32\SET1264.tmp
c:\windows\system32\SET1265.tmp
c:\windows\system32\SET1266.tmp
c:\windows\system32\SET1268.tmp
c:\windows\system32\SET1269.tmp
c:\windows\system32\SET126A.tmp
c:\windows\system32\SET126B.tmp
c:\windows\system32\SET126C.tmp
c:\windows\system32\SET126D.tmp
c:\windows\system32\SET126E.tmp
c:\windows\system32\SET126F.tmp
c:\windows\system32\SET1270.tmp
c:\windows\system32\SET1271.tmp
c:\windows\system32\SET1272.tmp
c:\windows\system32\SET1273.tmp
c:\windows\system32\SET1274.tmp
c:\windows\system32\SET1275.tmp
c:\windows\system32\SET1276.tmp
c:\windows\system32\SET1277.tmp
c:\windows\system32\SET1278.tmp
c:\windows\system32\SET1279.tmp
c:\windows\system32\SET12C2.tmp
c:\windows\system32\SET12C8.tmp
c:\windows\system32\SET45.tmp
c:\windows\system32\SET46.tmp
c:\windows\system32\SET47.tmp
c:\windows\system32\SET48.tmp
c:\windows\system32\SET49.tmp
c:\windows\system32\SET4A.tmp
c:\windows\system32\SET4B.tmp
c:\windows\system32\SET4C.tmp
c:\windows\system32\SET4D.tmp
c:\windows\system32\SET4E.tmp
c:\windows\system32\SET4F.tmp
c:\windows\system32\SET50.tmp
c:\windows\system32\SET51.tmp
c:\windows\system32\SET52.tmp
c:\windows\system32\SET53.tmp
c:\windows\system32\SET55.tmp
c:\windows\system32\SET56.tmp
c:\windows\system32\SET57.tmp
c:\windows\system32\SET58.tmp
c:\windows\system32\SET59.tmp
c:\windows\system32\SET5A.tmp
c:\windows\system32\SET5B.tmp
c:\windows\system32\SET5C.tmp
c:\windows\system32\SET5D.tmp
c:\windows\system32\SET5E.tmp
c:\windows\system32\SET5F.tmp
c:\windows\system32\SET60.tmp
c:\windows\system32\SET61.tmp
c:\windows\system32\SET62.tmp
c:\windows\system32\SET63.tmp
c:\windows\system32\SET64.tmp
c:\windows\system32\SET65.tmp
c:\windows\system32\SET66.tmp
c:\windows\system32\SETAF.tmp
c:\windows\system32\SETB5.tmp
c:\windows\system32\URTTemp
c:\windows\system32\URTTemp\fusion.dll
c:\windows\system32\URTTemp\mscoree.dll
c:\windows\system32\URTTemp\mscoree.dll.local
c:\windows\system32\URTTemp\mscorsn.dll
c:\windows\system32\URTTemp\mscorwks.dll
c:\windows\system32\URTTemp\msvcr71.dll
c:\windows\system32\URTTemp\regtlib.exe
.
.
((((((((((((((((((((((((( Files Created from 2012-11-28 to 2012-12-28 )))))))))))))))))))))))))))))))
.
.
2012-12-22 17:54 . 2012-12-22 17:58 -------- d-----w- c:\program files\ERUNT
2012-12-22 16:23 . 2009-01-25 18:14 15224 ----a-w- c:\windows\system32\sdnclean.exe
2012-12-22 16:23 . 2012-12-22 16:24 -------- d-----w- c:\program files\Spybot - Search & Destroy 2
2012-12-22 14:20 . 2012-12-22 14:22 -------- d-----w- C:\tdsskiller
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2012-11-15 12:31 . 2009-04-04 16:49 73728 ----a-w- c:\windows\system32\javacpl.cpl
2012-11-15 12:31 . 2012-11-15 12:31 477168 ----a-w- c:\windows\system32\npdeployJava1.dll
2012-11-15 12:31 . 2010-06-10 18:24 473072 ----a-w- c:\windows\system32\deployJava1.dll
2012-10-30 23:51 . 2012-04-06 00:30 361032 ----a-w- c:\windows\system32\drivers\aswSP.sys
2012-10-30 23:51 . 2012-04-06 00:30 35928 ----a-w- c:\windows\system32\drivers\aswRdr.sys
2012-10-30 23:51 . 2012-04-06 00:30 738504 ----a-w- c:\windows\system32\drivers\aswSnx.sys
2012-10-30 23:51 . 2012-04-06 00:30 54232 ----a-w- c:\windows\system32\drivers\aswTdi.sys
2012-10-30 23:51 . 2012-04-06 00:30 97608 ----a-w- c:\windows\system32\drivers\aswmon2.sys
2012-10-30 23:51 . 2012-04-06 00:30 89752 ----a-w- c:\windows\system32\drivers\aswmon.sys
2012-10-30 23:51 . 2012-04-06 00:30 21256 ----a-w- c:\windows\system32\drivers\aswFsBlk.sys
2012-10-30 23:51 . 2012-04-06 00:30 25256 ----a-w- c:\windows\system32\drivers\aavmker4.sys
2012-10-30 23:51 . 2010-08-24 23:40 41224 ----a-w- c:\windows\avastSS.scr
2012-10-30 23:50 . 2012-04-06 00:29 227648 ----a-w- c:\windows\system32\aswBoot.exe
2009-01-21 16:14 . 2009-01-21 16:14 9780224 -c--a-w- c:\program files\openofficeorg30.msi
2002-03-11 09:06 . 2002-03-11 09:06 1822520 -c--a-w- c:\program files\instmsiw.exe
2002-03-11 08:45 . 2002-03-11 08:45 1708856 -c--a-w- c:\program files\instmsia.exe
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\00avast]
@="{472083B0-C522-11CF-8763-00608CC02F24}"
[HKEY_CLASSES_ROOT\CLSID\{472083B0-C522-11CF-8763-00608CC02F24}]
2012-10-30 23:50 121528 ----a-w- c:\program files\AVAST Software\Avast\ashShell.dll
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"VTTrayp"="VTtrayp.exe" [2009-04-03 163840]
"VTTimer"="VTTimer.exe" [2009-04-03 53248]
"SMSERIAL"="sm56hlpr.exe" [2003-06-19 548864]
"SkyTel"="SkyTel.EXE" [2009-04-03 2879488]
"TkBellExe"="c:\program files\real\realplayer\update\realsched.exe" [2010-12-21 274608]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2010-11-29 421888]
"iTunesHelper"="c:\program files\iTunes\iTunesHelper.exe" [2011-04-14 421160]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2011-06-06 937920]
"avast"="c:\program files\AVAST Software\Avast\avastUI.exe" [2012-10-30 4297136]
"RTHDCPL"="RTHDCPL.EXE" [2009-04-03 16264192]
"SunJavaUpdateSched"="c:\program files\Common Files\Java\Java Update\jusched.exe" [2012-09-17 254896]
"SDTray"="c:\program files\Spybot - Search & Destroy 2\SDTray.exe" [2012-11-13 3825176]
.
[HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\RunOnce]
"RunNarrator"="Narrator.exe" [2008-04-14 53760]
.
[HKEY_LOCAL_MACHINE\system\currentcontrolset\control\session manager]
BootExecute REG_MULTI_SZ autocheck autochk *\0\0sdnclean.exe
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\WINDOWS\\system32\\dpvsetup.exe"=
"c:\\WINDOWS\\system32\\mmc.exe"=
"c:\\Program Files\\Avant Browser\\avant.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
"c:\\Program Files\\Spybot - Search & Destroy 2\\SDTray.exe"=
"c:\\Program Files\\Spybot - Search & Destroy 2\\SDFSSvc.exe"=
"c:\\Program Files\\Spybot - Search & Destroy 2\\SDUpdate.exe"=
"c:\\Program Files\\Spybot - Search & Destroy 2\\SDUpdSvc.exe"=
.
R1 aswSnx;aswSnx;c:\windows\system32\drivers\aswSnx.sys [4/5/2012 6:30 PM 738504]
R1 aswSP;aswSP;c:\windows\system32\drivers\aswSP.sys [4/5/2012 6:30 PM 361032]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [4/5/2012 6:30 PM 21256]
R2 SDScannerService;Spybot-S&D 2 Scanner Service;c:\program files\Spybot - Search & Destroy 2\SDFSSvc.exe [12/22/2012 10:23 AM 1103392]
R2 SDUpdateService;Spybot-S&D 2 Updating Service;c:\program files\Spybot - Search & Destroy 2\SDUpdSvc.exe [12/22/2012 10:24 AM 1369624]
S2 SDWSCService;Spybot-S&D 2 Security Center Service;c:\program files\Spybot - Search & Destroy 2\SDWSCSvc.exe [12/22/2012 10:24 AM 168384]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;\??\c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys --> c:\program files\Lavasoft\Ad-Aware\KernExplorer.sys [?]
S3 USB-100;Realtek RTL8150 USB 10/100 Fast Ethernet Adapter;c:\windows\system32\drivers\RTL8150.SYS [4/2/2009 11:31 AM 27519]
.
Contents of the 'Scheduled Tasks' folder
.
2012-12-28 c:\windows\Tasks\avast! Emergency Update.job
- c:\program files\AVAST Software\Avast\AvastEmUpdate.exe [2012-07-10 23:50]
.
2012-12-22 c:\windows\Tasks\Check for updates (Spybot - Search & Destroy).job
- c:\program files\Spybot - Search & Destroy 2\SDUpdate.exe [2012-12-22 20:08]
.
2012-12-28 c:\windows\Tasks\GoogleUpdateTaskMachineCore1cdc3344bffabd8.job
- c:\program files\Google\Update\GoogleUpdate.exe [2012-11-15 13:07]
.
2012-12-28 c:\windows\Tasks\RealUpgradeLogonTaskS-1-5-21-1708537768-1715567821-682003330-1003.job
- c:\program files\Real\RealUpgrade\realupgrade.exe [2010-11-05 17:33]
.
2012-12-28 c:\windows\Tasks\RealUpgradeScheduledTaskS-1-5-21-1708537768-1715567821-682003330-1003.job
- c:\program files\Real\RealUpgrade\realupgrade.exe [2010-11-05 17:33]
.
2012-12-21 c:\windows\Tasks\ReclaimerResumeInstall_Owner.job
- c:\documents and settings\Owner\Application Data\Real\Update\UpgradeHelper\RealPlayer\10.30\agent\rnupgagent.exe [2012-12-21 19:56]
.
2012-12-22 c:\windows\Tasks\Refresh immunization (Spybot - Search & Destroy).job
- c:\program files\Spybot - Search & Destroy 2\SDImmunize.exe [2012-12-22 20:07]
.
2012-12-22 c:\windows\Tasks\Scan the system (Spybot - Search & Destroy).job
- c:\program files\Spybot - Search & Destroy 2\SDScan.exe [2012-12-22 20:07]
.
2012-12-28 c:\windows\Tasks\User_Feed_Synchronization-{AFD2C05C-E64F-4ADA-91AC-4F506764F063}.job
- c:\windows\system32\msfeedssync.exe [2007-08-13 10:31]
.
.
------- Supplementary Scan -------
.
uStart Page = https://www.google.com/
uInternet Settings,ProxyOverride = *.local
TCP: DhcpNameServer = 192.168.1.1
.
- - - - ORPHANS REMOVED - - - -
.
Toolbar-Locked - (no file)
HKU-Default-RunOnce-AutoLaunch - c:\program files\Lavasoft\Ad-Aware\AutoLaunch.exe
Notify-SDWinLogon - SDWinLogon.dll
AddRemove-Octoshape add-in for Adobe Flash Player - c:\documents and settings\Owner\Application Data\Macromedia\Flash Player\www.macromedia.com\bin\octoshape\octoshape.exe
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2012-12-28 07:41
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
.
[HKEY_USERS\S-1-5-21-1708537768-1715567821-682003330-1003\Software\Microsoft\SystemCertificates\AddressBook*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="FlashBroker"
"LocalizedString"="@c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_4_402_265_ActiveX.exe,-101"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\Elevation]
"Enabled"=dword:00000001
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\LocalServer32]
@="c:\\WINDOWS\\system32\\Macromed\\Flash\\FlashUtil32_11_4_402_265_ActiveX.exe"
.
[HKEY_LOCAL_MACHINE\software\Classes\CLSID\{73C9DFA0-750D-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}]
@Denied: (A 2) (Everyone)
@="IFlashBroker5"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\ProxyStubClsid32]
@="{00020424-0000-0000-C000-000000000046}"
.
[HKEY_LOCAL_MACHINE\software\Classes\Interface\{6AE38AE0-750C-11E1-B0C4-0800200C9A66}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
"Version"="1.0"
.
Completion time: 2012-12-28 07:44:06
ComboFix-quarantined-files.txt 2012-12-28 13:44
.
Pre-Run: 28,281,712,640 bytes free
Post-Run: 33,183,825,920 bytes free
.
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Home Edition" /fastdetect /NoExecute=OptIn
.
- - End Of File - - 729B13BBBD6836AB7B35CC7A872F1E92
-

Hi Michele2012
Please unistall your old java version, via Add/remove programs
Go to Start > Control Panel, double-click on Add or Remove Programs
Select the program you want to uninstall by clicking on it, and then click the Uninstall button.
Download TFC to your desktop
- Close any open windows.
- Double click the TFC icon to run the program
- TFC will close all open programs itself in order to run,
- Click the Start button to begin the process.
- Allow TFC to run uninterrupted.
- The program should not take long to finish it's job
- Once its finished it should automatically reboot your machine,
- if it doesn't, manually reboot to ensure a complete clean
Next
Please download Malwarebytes' Anti-Malware to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.

- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected .
- When completed, a log will open in Notepad. Please save it to a convenient location and post the results.
- Note: If you receive a notice that some of the items couldn't be removed, that they have been added to the delete on reboot list, please reboot.
Next
ESET Online Scanner
I'd like us to scan your machine with ESET OnlineScan
Note: If you are using Windows Vista/7, open your browser by right-clicking on its icon and select 'Run as administrator' to perform this scan.
*Note
It is recommended to disable onboard antivirus program and antispyware programs while performing scans so there are no conflicts and it will speed up scan time.
Please don't go surfing while your resident protection is disabled!
Once the scan is finished remember to re-enable your antivirus along with your antispyware programs.
- Hold down Control and click on the following link to open ESET OnlineScan in a new window.
ESET OnlineScan - Click the
 button.
button. - For alternate browsers only: (Microsoft Internet Explorer users can skip these steps)
- Click on
 to download the ESET Smart Installer. Save it to your desktop.
to download the ESET Smart Installer. Save it to your desktop. - Double click on the
 icon on your desktop.
icon on your desktop.
- Check

- Click the
 button.
button. - Accept any security warnings from your browser.
- Check

- Make sure that the option "Remove found threats" is Unchecked
- Push the Start button.
- ESET will then download updates for itself, install itself, and begin
scanning your computer. Please be patient as this can take some time. - When the scan completes, push

- Push
 , and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply.
, and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply. - Push the Back button.
- Select Uninstall application on close check box and push

Please let me know how your machine is running now
On your next reply please post :
- Malwarebytes log
- Eset scan report
Let me know if you have any problems in performing with the steps above or any questions you may have.
Good Day!
-

Java uninstall - Which ones should I delete? All of them:
Java(TM) 6 Update 20
Java(TM) 6 Update 37
Java(TM) 6 Update 7
It doesn't say which one is the latest.
-

Hello Robybel:
I haven't used the computer much since you were helping me and since right before that when I removed the following programs: GoForFiles, Google Chrome, Freeze.com. It used to hang up mainly when I was copying text from a website to Microsoft Word. It would hang up every time using Windows Internet Explorer and then when Avast downloaded Google Chrome I could copy from a website to Word with less errors. I am able now to copy from Explorer to Word, I think, I haven't tried it much. It did hang up on an application today, one that you had me download, TFC I think, because it said it was using it but I rebooted and then it worked.
Anyway, I ended up removing Java 7 and Java 20 and kept Java 37. Here is my Malwarebytes log but I forgot to save the Eset scan log but it had 0 infected files and 0 cleand files after a 50-minute scan.
Malwarebytes Anti-Malware 1.70.0.1100
www.malwarebytes.org
Database version: v2012.12.29.06
Windows XP Service Pack 3 x86 NTFS
Internet Explorer 8.0.6001.18702
Owner :: MICHELLE-3WVINT [administrator]
12/29/2012 8:12:49 AM
mbam-log-2012-12-29 (08-12-49).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 240534
Time elapsed: 5 minute(s), 1 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules



 Michele2012
Michele2012 



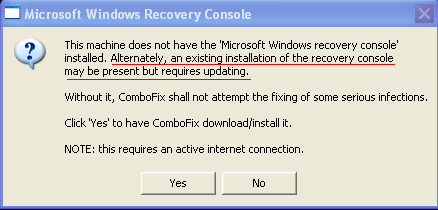
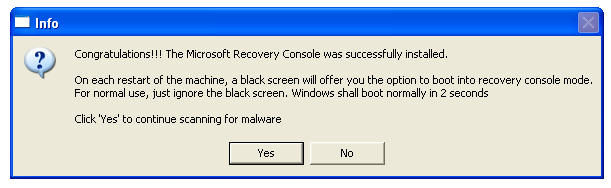

 button.
button. to download the ESET Smart Installer. Save it to your desktop.
to download the ESET Smart Installer. Save it to your desktop.
 button.
button.

 , and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply.
, and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply.
