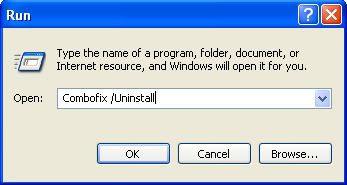
OCD,
Malwarebytes came up clean, but ESET showed a few threats. All listed below. The computer in runnung great.
Fujymo
Malwarebytes Anti-Malware 1.75.0.1300
www.malwarebytes.org
Database version: v2013.05.23.12
Windows 7 Service Pack 1 x86 NTFS
Internet Explorer 9.0.8112.16421
Matt :: MATT-DESKTOP [administrator]
5/23/2013 7:50:54 PM
mbam-log-2013-05-23 (19-50-54).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 238833
Time elapsed: 4 minute(s), 13 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
C:\Qoobox\Quarantine\C\Users\Matt\acrobatreader53868.exe.vir a variant of Win32/Kryptik.BBLX trojan
C:\Qoobox\Quarantine\C\Users\Matt\alg.exe.vir a variant of Win32/Kryptik.BBRA trojan
C:\Qoobox\Quarantine\C\Users\Matt\alg48478.exe.vir Win32/TrojanProxy.Agent.NMP trojan
C:\Qoobox\Quarantine\C\Users\Matt\chrome125524.exe.vir a variant of Win32/Medfos.PO trojan
C:\Qoobox\Quarantine\C\Users\Matt\icq442766.exe.vir a variant of Win32/Kryptik.BBRA trojan
C:\Qoobox\Quarantine\C\Users\Matt\java647518.exe.vir a variant of Win32/Kryptik.BBLX trojan
C:\Qoobox\Quarantine\C\Users\Matt\notepad582814.exe.vir a variant of Win32/TrojanProxy.Agent.NMP trojan
C:\Qoobox\Quarantine\C\Users\Matt\teamviewer.exe.vir a variant of Win32/Kryptik.BBLX trojan
C:\Qoobox\Quarantine\C\Users\Matt\windowsupdate.exe.vir a variant of Win32/Kryptik.BBRA trojan
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Local\miurtew.dll.vir a variant of Win32/TrojanProxy.Agent.NMV trojan
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\amsecure.exe.vir a variant of Win32/Kryptik.BBSL trojan
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\ashlp.dll.vir a variant of Win32/Medfos.PN trojan
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\msocpc.dll.vir a variant of Win32/Medfos.PN trojan
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\DefaultTab\DefaultTab\DefaultTabStart.exe.vir Win32/Toolbar.DefaultTab.A application
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\DefaultTab\DefaultTab\DefaultTabStart64.exe.vir Win64/Toolbar.DefaultTab.A application
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\DefaultTab\DefaultTab\DTUpdate.exe.vir Win32/Toolbar.DefaultTab.A application
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\DefaultTab\DefaultTab\update.exe.vir multiple threats
C:\Qoobox\Quarantine\C\Users\Matt\AppData\Roaming\Fiiwso\qyrygyy.exe.vir Win32/Spy.Zbot.ABA trojan
C:\Qoobox\Quarantine\C\Windows\spoolsvc.exe.vir a variant of Win32/Spy.Wagiclas.AB trojan
C:\Users\Public\Downloads\5thGrader_AOL-dm.exe a variant of Win32/Adware.Trymedia.A application