I really hate to bother the forum with this, but I'm at my wit's end!
I've been trying to remove this virus for several days now with no success. I'm running Windows XP and the virus shows up in SpyBot. It will disappear in safe mode, then reappear in the next regular scan. I've searched the forum and tried everything that I can find, with no luck...
Any help is greatly appreciated. Thanks! Keith
(Original link first posted in Forum-Software-Spybot)http://forums.spybot.info/showthread...761#post444761
Here's the DDS.txt:
DDS (Ver_2012-11-20.01) - NTFS_x86
Internet Explorer: 8.0.6001.18702
Run by Keith Simmons at 12:46:50 on 2013-09-04
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.1014.462 [GMT -5:00]
.
AV: avast! Antivirus *Enabled/Updated* {7591DB91-41F0-48A3-B128-1A293FD8233D}
FW: COMODO Firewall *Enabled*
.
============== Running Processes ================
.
C:\Program Files\Alwil Software\Avast5\AvastSvc.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\PROGRA~1\ALWILS~1\Avast5\avastUI.exe
C:\WINDOWS\stsystra.exe
C:\WINDOWS\system32\igfxpers.exe
C:\Program Files\Intel\Intel Matrix Storage Manager\Iaanotif.exe
C:\Program Files\Hp\HP Software Update\HPWuSchd2.exe
C:\WINDOWS\system32\hkcmd.exe
C:\Program Files\Logitech\SetPointP\SetPoint.exe
C:\WINDOWS\etMon.exe
C:\WINDOWS\ehome\ehtray.exe
C:\WINDOWS\System32\DLA\DLACTRLW.EXE
C:\Program Files\Spybot - Search & Destroy\TeaTimer.exe
C:\Program Files\SUPERAntiSpyware\SUPERAntiSpyware.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Common Files\LogiShrd\KHAL3\KHALMNPR.EXE
C:\Program Files\SUPERAntiSpyware\SASCORE.EXE
C:\Program Files\Digital Line Detect\DLG.exe
C:\Program Files\Common Files\Intuit\QuickBooks\QBUpdate\qbupdate.exe
C:\WINDOWS\eHome\ehRecvr.exe
C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkCalRem.exe
C:\WINDOWS\eHome\ehSched.exe
C:\Program Files\Intel\Intel Matrix Storage Manager\Iaantmon.exe
C:\Program Files\Common Files\Symantec Shared\CCPD-LC\symlcsvc.exe
C:\WINDOWS\system32\fxssvc.exe
C:\WINDOWS\ehome\mcrdsvc.exe
C:\WINDOWS\system32\dllhost.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\eHome\ehmsas.exe
C:\Program Files\Common Files\Microsoft Shared\Works Shared\WksCal.exe
C:\Program Files\Microsoft Office\OFFICE11\OUTLOOK.EXE
C:\Program Files\Microsoft Office\OFFICE11\WINWORD.EXE
C:\Program Files\Microsoft Works\WkDStore.exe
C:\Program Files\Google\Chrome\Application\chrome.exe
C:\Program Files\Google\Chrome\Application\chrome.exe
C:\Program Files\Google\Chrome\Application\chrome.exe
C:\WINDOWS\system32\wbem\wmiprvse.exe
C:\WINDOWS\system32\svchost.exe -k netsvcs
C:\WINDOWS\system32\svchost.exe -k NetworkService
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\WINDOWS\system32\svchost.exe -k LocalService
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\WINDOWS\System32\svchost.exe -k HTTPFilter
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://us.yahoo.com?fr=fp-comodo
uSearch Page = hxxp://www.google.com
uDefault_Page_URL = www.google.com/ig/dell?hl=en&client=dell-usuk-rel&channel=us&ibd=6070111
uInternet Connection Wizard,ShellNext = hxxp://home.frontiernet.net/WelcomeCD.asp
uSearchAssistant = hxxp://www.google.com
uSearchURL,(Default) = hxxp://www.google.com/keyword/%s
mSearchAssistant = hxxp://www.google.com
BHO: {1E8A6170-7264-4D0F-BEAE-D42A53123C75} - <orphaned>
BHO: {53707962-6F74-2D53-2644-206D7942484F} - <orphaned>
BHO: {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - <orphaned>
BHO: avast! WebRep: {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - c:\program files\alwil software\avast5\aswWebRepIE.dll
BHO: Windows Live Sign-in Helper: {9030D464-4C02-4ABF-8ECC-5164760863C6} - c:\program files\common files\microsoft shared\windows live\WindowsLiveLogin.dll
BHO: {DBC80044-A445-435b-BC74-9C25C1C588A9} - <orphaned>
TB: Yahoo! Toolbar: {EF99BD32-C1FB-11D2-892F-0090271D4F88} - c:\program files\yahoo!\companion\installs\cpn\yt.dll
TB: avast! WebRep: {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - c:\program files\alwil software\avast5\aswWebRepIE.dll
EB: Real.com: {FE54FA40-D68C-11d2-98FA-00C0F0318AFE} - c:\windows\system32\shdocvw.dll
uRun: [SpybotSD TeaTimer] c:\program files\spybot - search & destroy\TeaTimer.exe
uRun: [SUPERAntiSpyware] c:\program files\superantispyware\SUPERAntiSpyware.exe
uRun: [ctfmon.exe] c:\windows\system32\ctfmon.exe
uRun: [ConduitFloatingPlugin_jcnkjmghmdigcjcajaemenhlleobnhih] "c:\windows\system32\rundll32.exe" "c:\program files\conduit\ct3309657\plugins\TBVerifier.dll",RunConduitFloatingPlugin jcnkjmghmdigcjcajaemenhlleobnhih
mRun: [COMODO Internet Security] "c:\program files\comodo\comodo internet security\cfp.exe" -h
mRun: [avast5] c:\progra~1\alwils~1\avast5\avastUI.exe /nogui
mRun: [SigmatelSysTrayApp] stsystra.exe
mRun: [Persistence] c:\windows\system32\igfxpers.exe
mRun: [ISUSScheduler] "c:\program files\common files\installshield\updateservice\issch.exe" -start
mRun: [ISUSPM Startup] c:\progra~1\common~1\instal~1\update~1\ISUSPM.exe -startup
mRun: [IgfxTray] c:\windows\system32\igfxtray.exe
mRun: [IAAnotif] c:\program files\intel\intel matrix storage manager\Iaanotif.exe
mRun: [HP Software Update] c:\program files\hp\hp software update\HPWuSchd2.exe
mRun: [HotKeysCmds] c:\windows\system32\hkcmd.exe
mRun: [EvtMgr6] c:\program files\logitech\setpointp\SetPoint.exe /launchGaming
mRun: [etMonitor] c:\windows\etMon.exe
mRun: [ehTray] c:\windows\ehome\ehtray.exe
mRun: [DLA] c:\windows\system32\dla\DLACTRLW.EXE
mRun: [QuickTime Task] "c:\program files\quicktime\QTTask.exe" -atboottime
StartupFolder: c:\docume~1\keiths~1\startm~1\programs\startup\erunta~1.lnk - c:\program files\erunt\AUTOBACK.EXE
StartupFolder: c:\docume~1\keiths~1\startm~1\programs\startup\wkcalrem.lnk - c:\program files\common files\microsoft shared\works shared\WkCalRem.exe
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\adober~1.lnk - c:\program files\adobe\acrobat 7.0\reader\reader_sl.exe
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\digita~1.lnk - c:\program files\digital line detect\DLG.exe
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\quickb~1.lnk - c:\program files\common files\intuit\quickbooks\qbupdate\qbupdate.exe
uPolicies-Explorer: NoDriveTypeAutoRun = dword:145
mPolicies-Windows\System: Allow-LogonScript-NetbiosDisabled = dword:1
mPolicies-Explorer: NoDriveTypeAutoRun = dword:145
IE: E&xport to Microsoft Excel - c:\progra~1\mi1933~1\office11\EXCEL.EXE/3000
IE: {92780B25-18CC-41C8-B9BE-3C9C571A8263} - {FF059E31-CC5A-4E2E-BF3B-96E929D65503}
IE: {B205A35E-1FC4-4CE3-818B-899DBBB3388C} - {552781AF-37E4-4FEE-920A-CED9E648EADD}
IE: {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - {FE54FA40-D68C-11d2-98FA-00C0F0318AFE}
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {FB5F1910-F110-11d2-BB9E-00C04F795683} - c:\program files\messenger\msmsgs.exe
.
INFO: HKCU has more than 50 listed domains.
If you wish to scan all of them, select the 'Force scan all domains' option.
.
.
INFO: HKLM has more than 50 listed domains.
If you wish to scan all of them, select the 'Force scan all domains' option.
.
DPF: {0067DBFC-A752-458C-AE6E-B9C7E63D4824} - hxxp://www.logitech.com/devicedetector/plugins/LogitechDeviceDetection32.cab
DPF: {56762DEC-6B0D-4AB4-A8AD-989993B5D08B} - hxxp://www.eset.eu/buxus/docs/OnlineScanner.cab
DPF: {8FFBE65D-2C9C-4669-84BD-5829DC0B603C} - hxxp://fpdownload.macromedia.com/get/flashplayer/current/ultrashim.cab
TCP: NameServer = 192.168.254.254
TCP: Interfaces\{87A4AD3F-113A-4EA7-8351-9EB8BFD5832D} : DHCPNameServer = 192.168.254.254
Notify: !SASWinLogon - c:\program files\superantispyware\SASWINLO.DLL
Notify: igfxcui - igfxdev.dll
Notify: LBTWlgn - c:\program files\common files\logishrd\bluetooth\LBTWlgn.dll
Notify: WgaLogon - <no file>
AppInit_DLLs= c:\windows\system32\guard32.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\WPDShServiceObj.dll
SEH: SABShellExecuteHook Class - {5AE067D3-9AFB-48E0-853A-EBB7F4A000DA} - c:\program files\superantispyware\SASSEH.DLL
mASetup: {8A69D345-D564-463c-AFF1-A69D9E530F96} - "c:\program files\google\chrome\application\29.0.1547.66\installer\chrmstp.exe" --configure-user-settings --verbose-logging --system-level --multi-install --chrome
Hosts: 127.0.0.1 www.spywareinfo.com
.
============= SERVICES / DRIVERS ===============
.
R0 aswRvrt;aswRvrt;c:\windows\system32\drivers\aswRvrt.sys [2013-3-19 49376]
R0 aswVmm;aswVmm;c:\windows\system32\drivers\aswVmm.sys [2013-3-19 175176]
R0 tffsport;M-Systems DiskOnChip 2000;c:\windows\system32\drivers\tffsport.sys [2008-11-25 149376]
R1 aswSnx;aswSnx;c:\windows\system32\drivers\aswSnx.sys [2011-5-31 770344]
R1 aswSP;aswSP;c:\windows\system32\drivers\aswSP.sys [2009-3-28 369584]
R1 cmdGuard;COMODO Internet Security Sandbox Driver;c:\windows\system32\drivers\cmdGuard.sys [2010-6-4 497952]
R1 cmdHlp;COMODO Internet Security Helper Driver;c:\windows\system32\drivers\cmdhlp.sys [2010-6-1 32640]
R1 SASDIFSV;SASDIFSV;c:\program files\superantispyware\sasdifsv.sys [2011-7-22 12880]
R1 SASKUTIL;SASKUTIL;c:\program files\superantispyware\SASKUTIL.SYS [2011-7-12 67664]
R2 !SASCORE;SAS Core Service;c:\program files\superantispyware\SASCore.exe [2011-8-11 116608]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [2009-3-28 29816]
R2 aswMonFlt;aswMonFlt;c:\windows\system32\drivers\aswMonFlt.sys [2013-3-19 66336]
R2 avast! Antivirus;avast! Antivirus;c:\program files\alwil software\avast5\AvastSvc.exe [2010-6-17 46808]
R2 cmdAgent;COMODO Internet Security Helper Service;c:\program files\comodo\comodo internet security\cmdagent.exe [2010-6-1 1990464]
R2 LBeepKE;Logitech Beep Suppression Driver;c:\windows\system32\drivers\LBeepKE.sys [2012-1-5 12184]
R2 McrdSvc;Media Center Extender Service;c:\windows\ehome\mcrdsvc.exe [2005-8-5 99328]
R2 Symantec Core LC;Symantec Core LC;c:\program files\common files\symantec shared\ccpd-lc\symlcsvc.exe [2007-1-11 1251720]
S0 Lbd;Lbd;c:\windows\system32\drivers\lbd.sys --> c:\windows\system32\drivers\Lbd.sys [?]
S3 DCamUSBET;ET USB 2710 Camera;c:\windows\system32\drivers\etDevice.sys [2007-6-27 88704]
S3 FiltUSBET;ET USB Device Lower Filter;c:\windows\system32\drivers\etFilter.sys [2007-6-27 103680]
S3 motccgp;Motorola USB Composite Device Driver;c:\windows\system32\drivers\motccgp.sys --> c:\windows\system32\drivers\motccgp.sys [?]
S3 motccgpfl;MotCcgpFlService;c:\windows\system32\drivers\motccgpfl.sys --> c:\windows\system32\drivers\motccgpfl.sys [?]
S3 motport;Motorola USB Diagnostic Port;c:\windows\system32\drivers\motport.sys --> c:\windows\system32\drivers\motport.sys [?]
S3 ScanUSBET;ET USB Still Image Capture Device;c:\windows\system32\drivers\etScan.sys [2007-6-27 5760]
S3 SIUSBXP;SIUSBXP;c:\windows\system32\drivers\SiUSBXp.sys [2010-11-8 14592]
.
=============== File Associations ===============
.
ShellExec: pi11.exe: Open="c:\program files\microsoft digital image 2006\pi.exe" "%1"
.
=============== Created Last 30 ================
.
2013-09-04 16:37:18 -------- d-----w- c:\windows\QIUEKXANT6IGFLKJ
2013-09-04 16:36:47 -------- d-----w- c:\windows\BM375WFYPGE5O1KX
2013-09-04 16:31:30 -------- d-----w- C:\AdwCleaner
2013-09-04 14:18:10 -------- d-----w- c:\windows\UJP2LYBHU7JWER3F
2013-09-04 14:17:36 -------- d-----w- c:\windows\3VCP2EKXAGFLRJAG
2013-09-04 05:19:41 -------- d-----w- c:\windows\NGT6IV8KP2FLRX1K
2013-09-04 05:13:51 -------- d-----w- c:\documents and settings\keith simmons\application data\PC VITALWARE
2013-09-04 05:13:51 -------- d-----w- c:\documents and settings\all users\application data\PC VITALWARE
2013-09-04 04:05:30 -------- d-----w- c:\windows\IQA1J2ZBVM68YH8Y
2013-09-04 03:00:39 -------- d-----w- c:\windows\LA1YI9ZI90J9XNEY
2013-09-04 00:55:17 -------- d-----w- c:\windows\D69TXG7XH1YO1LYI
2013-09-03 23:11:31 -------- d-----w- c:\windows\XLYB2LYBO1DX2MZJ
2013-09-03 21:19:48 -------- d-----w- c:\windows\R14HMR4G05AMZ5HG
2013-09-02 21:36:07 -------- d-----w- c:\windows\QFLYBOU7CPOUTLRX
2013-09-02 21:35:05 -------- d-----w- c:\windows\GBS5HU0CHU4GTZCP
2013-09-02 19:52:10 -------- d-----w- c:\windows\S9RA1RB9ZIE5OF6P
2013-09-02 19:47:52 -------- d-----w- c:\windows\AEA8C2ZWUSQA1KB2
2013-09-02 18:05:36 -------- d-----w- c:\windows\3SHU7CWG0H1EJW9L
2013-09-02 17:28:00 -------- d-----w- c:\windows\I5HMZCWNJW9ZJW9E
2013-09-02 17:21:30 -------- d-----w- c:\windows\96HTZCP27JONMEDC
2013-09-02 14:52:26 -------- d-----w- c:\windows\MWLY4NS5HMZBV8K2
2013-09-02 06:58:55 -------- d-----w- c:\windows\SZRUX0UWZ2IE03JW
2013-09-02 06:53:33 -------- d-----w- c:\windows\63EXOFZQHZQH8RI9
2013-09-02 06:50:53 -------- d-----w- c:\windows\930DAN7CP2EQ3GT6
2013-09-02 06:50:19 -------- d-----w- c:\windows\0XQTWZ24DFXTPLHD
2013-09-02 06:39:25 -------- d-----w- c:\windows\GCNT6IN05PNTSKJI
2013-09-02 06:38:45 -------- d-----w- c:\windows\JEH8YP9ZP9TDXH1K
2013-09-02 06:33:50 -------- d-----w- c:\windows\QS5O1DQV8KJB3RIV
2013-09-02 06:32:05 -------- d-----w- c:\windows\Y4YEV5EHRT3CFPZS
2013-09-02 06:22:01 -------- d-----w- c:\windows\Y6MORUX09IKUNQTW
2013-09-02 06:16:32 -------- d-----w- c:\windows\841ZI96W8R8YI2ZJ
2013-09-02 03:39:27 -------- d-----w- c:\windows\0AS5AN05IU05HMLK
2013-09-02 03:33:22 338 ----a-w- c:\documents and settings\keith simmons\local settings\application data\poetsch.bat
2013-09-01 22:17:29 -------- d-----w- c:\windows\SOS2SI2SBVL5H1DQ
2013-09-01 21:03:14 -------- d-----w- c:\windows\7HPZGQ7NXE7N4KUB
2013-08-31 22:43:11 -------- d-----w- c:\windows\QGY305386IDA7XUS
2013-08-31 22:25:11 -------- d-----w- c:\windows\X63N6XG7Q9ZI9SCP
2013-08-31 03:46:12 -------- d-----w- c:\windows\7I7JO16IN05A8DBA
2013-08-30 16:20:57 28552 ----a-w- c:\windows\system32\spool\prtprocs\w32x86\mdippr.dll
2013-08-30 16:20:57 28040 ----a-w- c:\windows\system32\mdimon.dll
2013-08-14 23:03:22 -------- d-----w- c:\windows\LAGT6IV8DPV7J3M6
2013-08-14 23:02:20 -------- d-----w- c:\windows\WDQ3T6IV0C3M6XGT
2013-08-08 14:18:17 -------- d-----w- c:\windows\RN7Q3FZC3FS5HCPG
.
==================== Find3M ====================
.
2013-08-03 19:18:38 1543680 ------w- c:\windows\system32\wmvdecod.dll
2013-07-29 22:07:42 692104 ----a-w- c:\windows\system32\FlashPlayerApp.exe
2013-07-29 22:07:41 71048 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2013-07-26 02:47:17 920064 ----a-w- c:\windows\system32\wininet.dll
2013-07-26 02:47:13 43520 ----a-w- c:\windows\system32\licmgr10.dll
2013-07-26 02:47:12 1469440 ----a-w- c:\windows\system32\inetcpl.cpl
2013-07-25 15:52:59 385024 ----a-w- c:\windows\system32\html.iec
2013-07-10 10:37:53 406016 ----a-w- c:\windows\system32\usp10.dll
2013-07-04 03:03:25 2149888 ----a-w- c:\windows\system32\ntoskrnl.exe
2013-07-04 02:08:30 2028544 ----a-w- c:\windows\system32\ntkrnlpa.exe
2013-06-27 19:34:32 770344 ----a-w- c:\windows\system32\drivers\aswSnx.sys
2013-06-27 19:34:32 175176 ----a-w- c:\windows\system32\drivers\aswVmm.sys
2008-11-13 21:56:09 11281 ----a-w- c:\program files\common files\woko.bin
.
============= FINISH: 12:49:30.12 ===============
Attachment 10908
Here is the asmMBR Log:
aswMBR version 0.9.9.1771 Copyright(c) 2011 AVAST Software
Run date: 2013-09-04 13:33:04
-----------------------------
13:33:04.203 OS Version: Windows 5.1.2600 Service Pack 3
13:33:04.203 Number of processors: 2 586 0xF06
13:33:04.203 ComputerName: D1Q0QCC1 UserName:
13:33:07.031 Initialize success
13:33:11.156 AVAST engine defs: 13090400
13:33:28.828 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IAAStorageDevice-1
13:33:28.828 Disk 0 Vendor: ST316081 3.AD Size: 152587MB BusType: 3
13:33:29.015 Disk 0 MBR read successfully
13:33:29.015 Disk 0 MBR scan
13:33:29.015 Disk 0 unknown MBR code
13:33:29.046 Disk 0 Partition 1 00 DE Dell Utility Dell 8.0 39 MB offset 63
13:33:29.062 Disk 0 Partition 2 80 (A) 07 HPFS/NTFS NTFS 147793 MB offset 80325
13:33:29.093 Disk 0 Partition 3 00 DB CP/M / CTOS Dell 8.0 4753 MB offset 302760990
13:33:29.093 Disk 0 scanning sectors +312496380
13:33:29.281 Disk 0 scanning C:\WINDOWS\system32\drivers
13:33:46.671 Service scanning
13:34:02.484 Modules scanning
13:34:16.140 Module: C:\WINDOWS\System32\DLA\DLADResN.SYS **SUSPICIOUS**
13:34:18.046 Disk 0 trace - called modules:
13:34:18.078 ntkrnlpa.exe CLASSPNP.SYS disk.sys iaStor.sys hal.dll
13:34:18.078 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x86f87870]
13:34:18.078 3 CLASSPNP.SYS[f75b0fd7] -> nt!IofCallDriver -> \Device\Ide\IAAStorageDevice-1[0x86f75030]
13:34:18.562 AVAST engine scan C:\WINDOWS
13:34:39.765 AVAST engine scan C:\WINDOWS\system32
13:38:40.796 AVAST engine scan C:\WINDOWS\system32\drivers
13:39:14.234 AVAST engine scan C:\Documents and Settings\Keith Simmons
14:45:05.640 AVAST engine scan C:\Documents and Settings\All Users
14:47:22.359 Scan finished successfully
14:55:25.500 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\Keith Simmons\My Documents\MBR.dat"
14:55:25.515 The log file has been saved successfully to "C:\Documents and Settings\Keith Simmons\My Documents\aswMBR.txt"
14:56:01.359 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\Keith Simmons\Desktop\MBR.dat"
14:56:01.359 The log file has been saved successfully to "C:\Documents and Settings\Keith Simmons\Desktop\aswMBR.txt"
In case the above attachment fails, here is the zipped attach.txt file. attachtxt.zip
Best,
Keith
I haven't attempted any fixes since posting this thread, but just now ran SpyBot to check the system.
Strangely, the virus isn't showing up. Can this virus go dormant for periods and then reactivate???
Thanks,
Keith






 AdwCleaner
AdwCleaner Please download
Please download 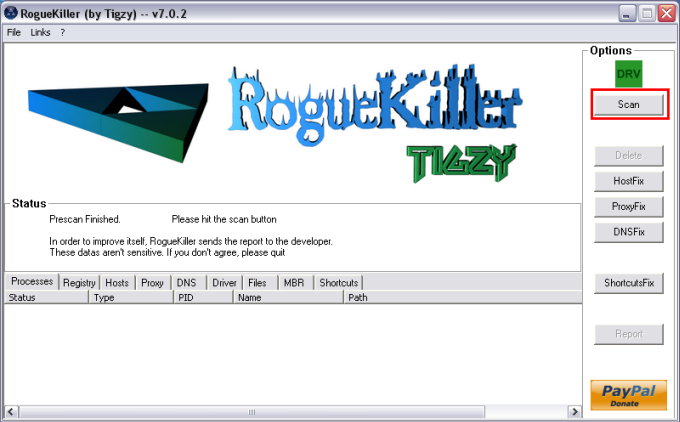
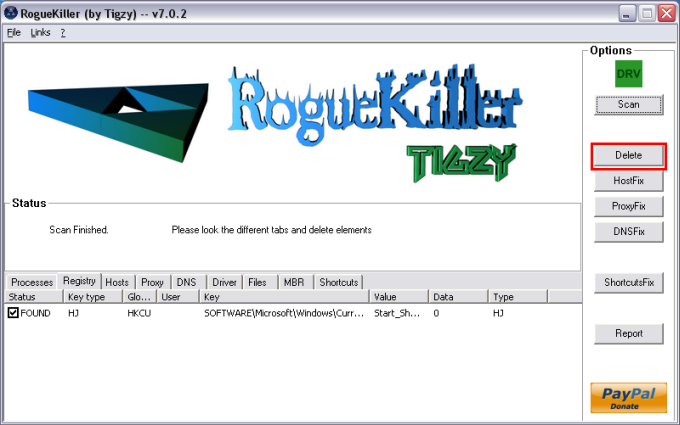
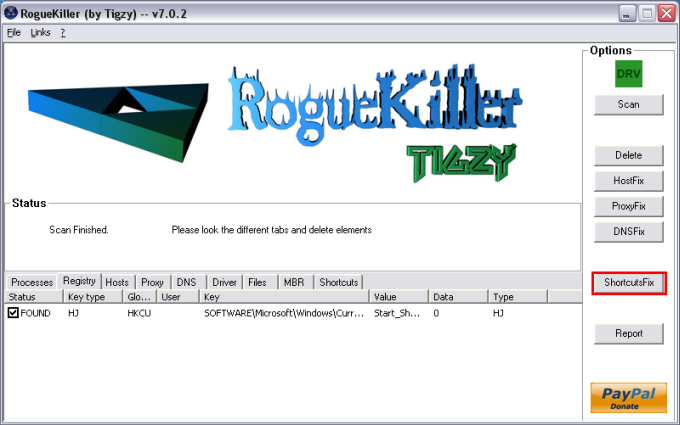
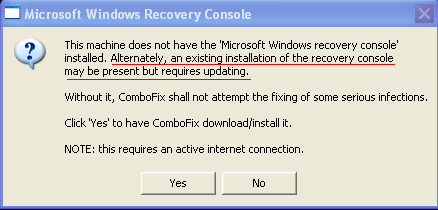
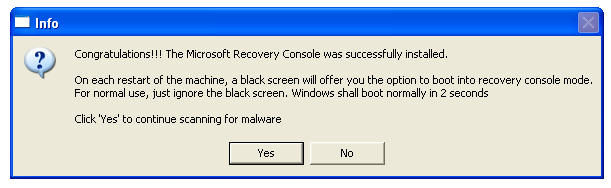


 button.
button. to download the ESET Smart Installer. Save it to your desktop.
to download the ESET Smart Installer. Save it to your desktop.
 button.
button.

 , and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply.
, and save the file to your desktop using a unique name, such as MyEsetScan. Alternatively, look for report in C:\Program Files\ESET\ESET Online Scanner\log.txt. Include the contents of this report in your next reply.
