You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
New advertising malware?
- Thread starter jhrowehl
- Start date
- Status
- Not open for further replies.
gotcha!
We'll be here if needed.
So far today, everything looked good. I'm going leave Firefox active for a bit tonight, to see if any rogue processes come up. I'm fairly confident that I won't see any, but, once bit, twice cautious.
Just out of curiosity, if that was the problem, will the offending DLL's be added to the definition files at some point? I still have them in the recycle bin, and am going to try to get them onto a memory stick or something.
I have the 2 DLL files isolated in secure storage. Here are the VirusTotal links:
colers.dll
https://www.virustotal.com/en/file/...27d8cae0ccfc8f2b78856b3c/analysis/1426108563/
tivesen.dll
https://www.virustotal.com/en/file/...a87892197fbb1870b8089eb6/analysis/1426108659/
colers.dll
https://www.virustotal.com/en/file/...27d8cae0ccfc8f2b78856b3c/analysis/1426108563/
tivesen.dll
https://www.virustotal.com/en/file/...a87892197fbb1870b8089eb6/analysis/1426108659/
wooohooo!So far today, everything looked good. I'm going leave Firefox active for a bit tonight, to see if any rogue processes come up. I'm fairly confident that I won't see any, but, once bit, twice cautious.
I'm checking into the other to see if the R&D team needs those.
It's possible you may want to contact your antivirus vendor with these.
wooohooo!
I'm checking into the other to see if the R&D team needs those.
It's possible you may want to contact your antivirus vendor with these.
The status report for today is... still no rogue processes.
It looks like we have the problem under control. Quick question... what program was calling the DLL's? Do I need to remove that program and associated registry entries?
The status report for today is... still no rogue processes.
It looks like we have the problem under control. Quick question... what program was calling the DLL's? Do I need to remove that program and associated registry entries?
To give you an exact program name..., don't know if I can but from what we did find and remove
C:\ProgramData\Optimizer ---> 3 / 68 (PUP)
Publisher: MicroTools
Both of those are capable of adding entries into the C:\Users\Henry\AppData\Roaming folder where malware so often does.
I honestly think if there was anything residual left behind it would had reared it's ugly head by now.
We need to remove tools and quarantine folders.
DelFix
- Please download DelFix
or from here http://www.bleepingcomputer.com/download/delfix/ and save the file to your Desktop. - Double-click DelFix.exe to run the programme.
- Place a checkmark next to the following items:
- Activate UAC
- Remove disinfection tools
- Purge system restore
- Click the Run button.
~~~~~~~~~~~~~~~~~~~
- Answers to common security questions - Best Practices by quietman7, MVP
- How Malware Spreads - How did I get infected? by quietman7, MVP
- Simple and easy ways to keep your computer safe and secure on the Internet by Lawrence Abrams, MVP
- How to Prevent Malware by miekiemoes, MVP
- How to backup and restore your data using Cobian Backup by YourHighness
- Slow Computer/browser? It May Not Be Malware by quietman7, MVP
-
AdBlock is a browser add-on that blocks annoying banners, pop-ups and video ads.

- CryptoPrevent places policy restrictions on loading points for ransomware (eg.CryptoPrevent), preventing your files from being encrypted.

- Malwarebytes Anti-Exploit (MBAE) is designed to prevent zero-day malware from exploiting vulnerable software.

- Malwarebytes Anti-Malware Premium (MBAM) works in real-time along side your Anti-Virus to prevent malware execution.

- NoScript is a Firefox add-on that blocks the actions of malicious scripts by using whitelisting and other technology.

 Sandboxie isolates programmes of your choice, preventing files from being written to your HDD unless approved by you.
Sandboxie isolates programmes of your choice, preventing files from being written to your HDD unless approved by you.- Secuina PSI will scan your computer for vulnerable software that is outdated, and automatically find the latest update for you.

- SpywareBlaster is a form of passive protection, designed to block the actions of malicious websites and tracking cookies.

- Web of Trust (WOT) is a browser add-on designed to alert you before interacting with a potentially malicious website.

Want to help others? Join the ClassRoom and learn how.
I did a quick search of the registry, and came up with the colers.dll file in 4 locations. I didn't find the other one that was in the deleted directory, tivesen.dll.
I've attached a file with the registry keys listed. Don't know if it will help or not, but, I figured it couldn't hurt.
I've attached a file with the registry keys listed. Don't know if it will help or not, but, I figured it couldn't hurt.
Attachments
It was a battle!OK, I think I'm ready to say that the problem is gone.
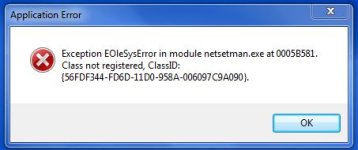
CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090} which I think can mean task bar, tool bar or BHO
56FDF344-FD6D-11d0-958A-006097C9A090 is a windows system Taskbar Communication component.
AdwCleaner in different logs took it out
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
When searching it was also located when asking someone to do a Search for "ask"
Now, if this applies to you, heaven only knows.
Have you done a search to see if this folder is still on the computer?
C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej
We can take out those reg entries
Next, launch Notepad, (Start > Run, type in: notepad) copy and paste next present in the quotebox below in it:
Windows Registry Editor Version 5.00
[-HKEY_CLASSES_ROOT\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
[-HKEY_CLASSES_ROOT\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
[-HKEY_CURRENT_USER\Software\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
[-HKEY_CURRENT_USER\Software\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
[-HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
[-HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
[-HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
[-HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
Save this as fix.reg and change the "Save as type" to "All Files" and place it on your desktop. It should look like this:

Double-click on it and when it asks you if you want to merge the contents to the registry, click "Yes" or "OK". You should receive a message that it was successful. You may delete the file afterwards
Last edited:
Yes, it was a battle! But, we managed to track it down, and win the fight.
Yes I did, no it's not. I had removed it per your instructions in a prior message. That's when the problem went away. I managed to recover it, and the contents, from the recycle bin, and have the folder and the files isolated in a secure storage area.
The second DLL file, that was in the folder with the colers.dll file, wasn't in the registry. Makes me curious...
Have you done a search to see if this folder is still on the computer?
C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej
Yes I did, no it's not. I had removed it per your instructions in a prior message. That's when the problem went away. I managed to recover it, and the contents, from the recycle bin, and have the folder and the files isolated in a secure storage area.
The second DLL file, that was in the folder with the colers.dll file, wasn't in the registry. Makes me curious...
I reckon it was a ghost file?..but I am so glad it's gone. (I danced a little jig, if your from the south you'll know what that means)
but want to say, it's been a pleasure.
I know what dancing a jig is all about!
Just out of curiosity, I have something going on now (not related to the original problem!). One of the registry keys seems to have been... corrupted? System restore is not working due to a known problem put out by Microsoft. Somewhere along the line, a registry backup was done. I still have those files where the program put them. How can I restore the registry?
I know that's going to put back entries that we removed, but, I still have the scripts available in this thread, so I can remove them again.
Early on, did you download and use Tweaking, registry backup
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Tweaking.com
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\Program Files (x86)\Tweaking.com
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
http://forums.spybot.info/showthrea...ocedure-Before-Requesting-Assistance)-Updated
did you follow requirements here on post #2?
There will now be a folder at the root of the Hard-Drive named C:\RegBackup
Can you give me info on what registry key is messing up?
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Tweaking.com
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\Program Files (x86)\Tweaking.com
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
http://forums.spybot.info/showthrea...ocedure-Before-Requesting-Assistance)-Updated
did you follow requirements here on post #2?
There will now be a folder at the root of the Hard-Drive named C:\RegBackup
Can you give me info on what registry key is messing up?
Last edited:
Early on, did you download and use Tweaking, registry backup
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Tweaking.com
2015-02-28 18:21 - 2015-02-28 18:21 - 00000000 ____D () C:\Program Files (x86)\Tweaking.com
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
2015-02-21 11:06 - 2015-02-21 11:06 - 00000207 _____ () C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
C:\Windows\tweaking.com-regbackup-ELSERVICE13-Windows-7-Professional-(64-bit).dat
http://forums.spybot.info/showthrea...ocedure-Before-Requesting-Assistance)-Updated
did you follow requirements here on post #2?
There will now be a folder at the root of the Hard-Drive named C:\RegBackup
Can you give me info on what registry key is messing up?
Yes, I did, and I have the backups still available. I thought I had posted this already, but I figured out how to do the registry restore, and all is working well again. The registry key that was 'not quite right' is in the attached screen capture.
Before I did the restore, I exported the entire registry into a separate folder. Now, I'm going to export it again into another folder, and then do a file compare to see what changed. If you've ever heard of TotalCommand, it absolutely outstanding for that. Highlight one file in the left window, highlight another file in the right window, and have it compare by content. It will highlight all the differences. Once I find the difference with that class ID, I'll let you know.
Attachments
OK... the following is the results of comparing the two registry files. The section "Reg2" is the registry that I was having the problem with. The section "Reg3" is the restored registry that works. Note that there a 5 entries in the problem registry, and 10 entries in the working registry.
Missing ClassID
Reg2
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
"LastKey"="Computer\\HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Classes\\CLSID\\{56FDF344-FD6D-
11d0-958A-006097C9A090}"
Reg3
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-
006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-
006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID
\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID
\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@="C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej\\colers.dll"
"ThreadingModel"="Apartment"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-
FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-
FD6D-11d0-958A-006097C9A090}\InProcServer32]
@="C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej\\colers.dll"
"ThreadingModel"="Apartment"
Missing ClassID
Reg2
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
"LastKey"="Computer\\HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Classes\\CLSID\\{56FDF344-FD6D-
11d0-958A-006097C9A090}"
Reg3
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{56FDF344-FD6D-11d0-958A-
006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{56FDF344-FD6D-11d0-958A-
006097C9A090}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,65,00,78,00,\
70,00,6c,00,6f,00,72,00,65,00,72,00,66,00,72,00,61,00,6d,00,65,00,2e,00,64,\
00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID
\{56FDF344-FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000\Software\Classes\Wow6432Node\CLSID
\{56FDF344-FD6D-11d0-958A-006097C9A090}\InProcServer32]
@="C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej\\colers.dll"
"ThreadingModel"="Apartment"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-
FD6D-11d0-958A-006097C9A090}]
@="Task Bar Communication"
[HKEY_USERS\S-1-5-21-1310488628-551009281-1505269296-1000_Classes\Wow6432Node\CLSID\{56FDF344-
FD6D-11d0-958A-006097C9A090}\InProcServer32]
@="C:\\Users\\Henry\\AppData\\Roaming\\xaeojhej\\colers.dll"
"ThreadingModel"="Apartment"
yes!I figured out how to do the registry restore, and all is working well again
In Reg3, all those items were restored?
I see the bad folder and the bad file?
yes!
In Reg3, all those items were restored?
I see the bad folder and the bad file?
The entire registry was restored - the whole shootin' match. Like I had mentioned in one of my last posts, this will restore all the 'bad' stuff too... but we know what was removed. The fixlist entries are still in the messages here. Even though it will be 'been there, done that', at least we're not shooting in the dark looking for the problem. And on that subject, the original problem did *not* return with the registry restore. The registry entries were restored, not the folder or the files. When the folder with the files was deleted, the problem went away. Those files are still gone.
The restored registry now references non-existent files, but I can fix that. I can go back through the message thread, get all the FRST fixlist files, and re-run them.
Was thinking I was getting ready to shoot you!, then read it over again and see it's better then expected.the original problem did *not* return with the registry restore. The registry entries were restored, not the folder or the files. When the folder with the files was deleted, the problem went away. Those files are still gone.
The restored registry now references non-existent files, but I can fix that. I can go back through the message thread, get all the FRST fixlist files, and re-run them.
goodness gracious, ok, the computer still in good shape?
Was thinking I was getting ready to shoot you!, then read it over again and see it's better then expected.
goodness gracious, ok, the computer still in good shape?
I was wearing my bulletproof vest...
And so far, so good. I haven't seen the rogue processes yet. I'll be keeping an eye on it for a few days again, but I'm confident that I won't see the problem.
LOL!I was wearing my bulletproof vest
You know, if it ain't broke?
- Status
- Not open for further replies.