My guess is that it is related to an older version of Firefox. If something should be working and it's not related to Firefox would have to go to the Firefox forums to ask those questionsAh ok.
Well perhaps make a note on it stating on later release, you may not see the All Users checkbox, in which case you can ignore it...?
So I've been following along and reading these various articles you've linked me to. One of which was (when I eventually got) was speeding up Firefox, it says to look for this entry: browser.tabs.showSingleWindowModePrefs but such entry doesn't exist or no longer exist, so how does one follow this guide if it doesn't exist? The other two entries: network.http.pipelining and network.http.pipelining.maxrequests exist so I am able to change those values.
https://support.mozilla.org/en-US/kb/get-community-support
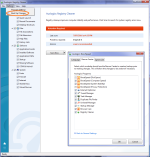
screen shots didn't work. I would keep system restore enabled in case an event happened and you needed to restore to an earlier date. I know that after a while the older ones will be deleted allowing newer ones to be created.Ok, so I've started to make use of group policy settings(from reading the linked articles of course), how does this look? Check the attachment for the screenshot.View attachment 12635 Anything needs to change or add to it so I am more proactively protected from virus and malware? I notice VSSAdmin.exe is optional which doesn't really do much if you're not making use of system restore or any of that kind of stuff, like me as it's completely disabled to save space as I'm only on a 128GB SSD. All virus and malware can do to it is make it remove all restoration points, but since I don't have any and it's disabled, it's effectively mute....hahahaha
I leave group policies where they are, can be difficult to change later. At least your educating yourself on the inner workings of an operating system.
I'm on the end of malware removal, I do know there are many people sending in samples daily so it might take a while to see and analyze files submitted and added to definitions.I do make use of 'principle of least privilege'(unfortunately this doesn't really work well with windows XP as some legitimate programs/games throw a fit if you're not an admin so I guess I'll stay as admin but at least enforce the same group policy settings I have for my lappy?) so I only get access to stuff I usually want to access and no more so if a virus/malware does somehow get a hold of my account, I'm only on a limited account so all it can do is what all I can do, unless I accidentally give it admin privileges from a legitimate looking executable file....such as said game trainer......I'm still a bit confused as it shouldn't really need admin access to alter a game's memory.....speaking of which, hows the analyses going? Or are you guys completely different to the person on the other end of detections @ spybot.info that I submitted the zipped file to?
Tools that go after cleaning the registry should actually be left alone. No registry cleaner is completely safe since most do not even create a backup the potential is ever present to cause more problems than they claim to fix.So in on of the posts, it says: View attachment 12636 I have Auslogics Boostspeed(and AVG PC Tuneup 2012 another program I've used in the past), and this program falls under that right, since it apparently also has a memory manager/optimizer/registry cleaner of sorts with it? So they are just a gimmick then? So I shouldn't really bother with these stuff and just be fine with only Ccleaner and a program to defrag HDDs and that's it for any cleaning and optimization? I remember reading something that it says it will just push those programs from memory into pagefile system, but if you don't have that(mine's disabled)....where does the memory allocation go to?
The other tools from Boostspeeds are convenient at times, such as Disk Defrag, Startup Manager, Tweak Manager, Locked Files Manager, Uninstall Manager(used to use this but Revo replaces this as it's superior), and Internet Optimizer. So what about registry defrag, is that another unneeded optimization?
I would have thought an optimization program like BoostSpeed is just a more comprehensive version of Ccleaner takes off where Ccleaner leaves as it would appear that BoostSpeeds picks up some more stuff that Ccleaner is wasn't able to pick up.
My usual routine I used to follow but don't anymore or not as much now (coz I'm lazy!) was this:
>Scan computer for virus/malware
>Clean with Ccleaner
>Further clean and optimize with BoostSpeed/PC TuneUp (which ever is installed)
> Backup/move files/folders now that you they are virus/malware free
>Profit
If you do not have knowledge of the registry, then you would probably be better off leaving it alone, and definitely not placing blind trust in a program to do the job for you. Ones that take care of more simpler jobs are acceptable, defrag or boost speed by disabling startups can be used so that later you can change these items if needed.
I would keep the host files setup from SpyBot since it's updated more frequently.Hm, I have a question about using online scanners like that ESET one you wanted me to do; some people have suggested it's best ot be 100% offline and *then* scan for possible viruses and malware. So by having your computer connected and letting the online scanner do it's job, wouldn't any virus/malware that are active could very well have started to do some damage or phone home and then do some damage in some way whilst you're scanning? Is that a risk that the user has to take...? For example, say I get infected with Cryptolocker or something of this caliber, and I am still connected so ESET can do it's scan, so CryptoLocker goes around, encrypting all my files and then gets to the scanner and screws it up somehow, by forcing it to crash or just fail and then afterwards, it finishes off the computers whilst I am being confused as to what has happened, besides knowing ESET online scanner failed to scan the entire computer.
Another question, should I use MVPS' HOSTS file or just keep using my own? Do take note that Spyware Blaster, Spybot Search and Destory and possibly other programs I have and myself included may have added additional entries to my own HOSTS file.
And lastly but not lease: Is my computer now confirmed to be virus/malware free?
If malware is running, or calling home, it does it with all tools running to catch the malicious files to be cleaned. Sometimes by going into safemode a virus isn't working because of how few windows files run at that time and is a good time to try and run removal tools to take advantage of this.
By the time we ask for an online scan, it's our hope we're going after remnants. Being connected to the internet makes no difference unless it was malware designed to make connections impossible.
The design of the Crypto (variants) run regardless connected to the internet or not, even run hidden for a very short time by design then deletes it's own executable file. What it does behind the scenes isn't caught till the damage done.
I think your computer is clean and your good to go.