You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
remove Generic.Ransom.VxLock.E31AD1D6
- Thread starter Chris Haslam
- Start date
- Status
- Not open for further replies.
Chris Haslam
New member
Chris Haslam
New member
Hovering over each of the 2 shows that they are reporting on FRST.exe
Chris Haslam
New member
scan_220415-161119.txt
-----------------------
Emsisoft Emergency Kit - Version 2021.9
Last update: 2022-04-15 12:42:23
My own Molly\Chris
MOLLY
Windows 7x86 Service Pack 1
Scan settings:
Scan type: Malware Scan
Objects: Rootkits, Memory, Traces, Files
Detect PUPs: ON
Scan archives: OFF
Scan mail archives: OFF
ADS Scan: ON
Direct disk access: OFF
Scan start: 2022-04-15 16:11:19
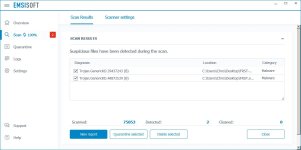
C:\Users\Chris\Desktop\FRST-OlderVersion\FRST.exe detected: Trojan.GenericKD.39437243 (B) [krnl.xmd]
C:\Users\Chris\Desktop\FRST.exe detected: Trojan.GenericKD.48872539 (B) [krnl.xmd]
Scanned 75053
Found 2
Scan end: 2022-04-15 16:12:28
Scan time: 0:01:09
-----------------------
Emsisoft Emergency Kit - Version 2021.9
Last update: 2022-04-15 12:42:23
My own Molly\Chris
MOLLY
Windows 7x86 Service Pack 1
Scan settings:
Scan type: Malware Scan
Objects: Rootkits, Memory, Traces, Files
Detect PUPs: ON
Scan archives: OFF
Scan mail archives: OFF
ADS Scan: ON
Direct disk access: OFF
Scan start: 2022-04-15 16:11:19
C:\Users\Chris\Desktop\FRST-OlderVersion\FRST.exe detected: Trojan.GenericKD.39437243 (B) [krnl.xmd]
C:\Users\Chris\Desktop\FRST.exe detected: Trojan.GenericKD.48872539 (B) [krnl.xmd]
Scanned 75053
Found 2
Scan end: 2022-04-15 16:12:28
Scan time: 0:01:09
Chris Haslam
New member
What's the computer doing now?[/QUOTE]
Still sitting at the Scan Results window
Still sitting at the Scan Results window
Chris Haslam
New member
I've got to sign off for the evening.
If all that was found related to the Farbar Recovery tool then we're in good shape.
Let me know if your ready to remove tools and quarantine folders.
I see that Farbar found 10 files. Trusting in your guidance, I believe that I am ready to remove tools and quarantine folders. Is there a risk in doing so?
I note that we have seen no sign of the ransom ware. Does this surprise you?
The files we removed with FRST was a tidy up event, they were lose files that added nothing to the machine.I see that Farbar found 10 files. Trusting in your guidance, I believe that I am ready to remove tools and quarantine folders. Is there a risk in doing so?
I note that we have seen no sign of the ransom ware. Does this surprise you?
As for having a Ransomeware infection, no signs of it.
And there was no mention of any notes or alerts telling you your computer had been infected and of money to get your files back.
The encrypted files for this specific infection will have the extension '.VXLOCK' appended to the end of the file name and on this machine there were none.
I can't say why, but I think what you saw was a false-positive.
Use this tool to remove quarantined items:
Please download KpRm by Kernel-panik and save to your Desktop.
- Click on KpRm.exe to run the tool.
Vista/Windows 7/8/10 users right-click and select Run As Administrator. - Put a check mark next to these items:
- Delete tools
- Delete now - Click the "Run" button.

- When the tool has finished, it will create and open a log report and delete itself.
Chris Haslam
New member
Thank you for your further instructions. Your idea that this is a false positive are potentially comforting!
I am wondering a bit about EEK's new user interface. You wrote, in Post 13, that EEK would take some time to run: it ran rapidly.
I also see in #13 that, with the old UI, I would have needed to check Run Directly. In scan...txt, I see Direct Disk Access: Off. Should I have turned it on in Settings?
Another thought: I do not use Outlook. Is the email application I am using protecting my PC?
I am wondering a bit about EEK's new user interface. You wrote, in Post 13, that EEK would take some time to run: it ran rapidly.
I also see in #13 that, with the old UI, I would have needed to check Run Directly. In scan...txt, I see Direct Disk Access: Off. Should I have turned it on in Settings?
Another thought: I do not use Outlook. Is the email application I am using protecting my PC?
I say potentially false-positive because I and the tools used to scan for infections were not there.Thank you for your further instructions. Your idea that this is a false positive are potentially comforting!
I am wondering a bit about EEK's new user interface. You wrote, in Post 13, that EEK would take some time to run: it ran rapidly.
I also see in #13 that, with the old UI, I would have needed to check Run Directly. In scan...txt, I see Direct Disk Access: Off. Should I have turned it on in Settings?
Another thought: I do not use Outlook. Is the email application I am using protecting my PC?
In the past, online scanners took hours to scan a computer because hard drives can be so full and people save tons of items.
The interface of the scanner had changed recently, they don't contact those who help with malware removal, kinda wish they did so I wouldn't look so stupid.
If you feel we should run other scanners to try and find something we can but since you haven't mentioned anything out of the ordinary happening I just don't think it's necessary.
Email servers
It's the person behind the computer who is your best security tool.
I did a few minutes of research on Pegasus Mail (Of which I have never used, not saying good or bad about this email client I just don't know anything about it myself)
Pegasus Mail
is a donationware, proprietary email client
distribution and development of Pegasus Mail had ceased due to inadequate financial support from the sale of the manuals
I personally use the email client that came with the ISP provided here, I do not freely give it out.
I hate, I absolutely hate having to open attachments. I have windows defender scan it before opening and use MalwareBytes to scan.
I get junk mail and out it goes.
Happy Easter.
Chris Haslam
New member
Happy Easter!
I downloaded and ran (as Administrator) KpRm as you suggested. Here's the log:
# Run at 2022-04-17 16:51:06
# KpRm (Kernel-panik) version 2.9.3
# Website https://kernel-panik.me/tool/kprm/
# Run by Chris from C:\Users\Chris\Desktop
# Computer Name: MOLLY
# OS: Windows 7 X86 (7601) Service Pack 1
# Number of passes: 1
- Checked options -
~ Delete Tools
~ Delete Quarantines
- Delete Tools -
## AdwCleaner
[OK] C:\AdwCleaner deleted
## Emisoft Emergency Kit
[R] C:\Users\Chris\Desktop\EmsisoftEmergencyKit.exe deleted
[R] C:\EEK deleted
## ESET Online Scanner
[OK] C:\Users\Chris\AppData\Local\ESET\ESETOnlineScanner deleted
[OK] HKLM\SOFTWARE\ESET\ESET Online Scanner deleted
## FRST
[OK] C:\Users\Chris\Desktop\Addition.txt deleted
[OK] C:\Users\Chris\Desktop\Fixlog.txt deleted
[OK] C:\Users\Chris\Desktop\FRST-OlderVersion deleted
[OK] C:\Users\Chris\Desktop\FRST.exe deleted
[OK] C:\Users\Chris\Desktop\FRST.txt deleted
[OK] C:\FRST deleted
-- KPRM finished in 92.13s --
- Need to Restart -
I restarted.
BTW I remember Opening an email in Pegasus back in March. The text was in green, not the normal black. The window blurred for several seconds then the email disappeared from the screen, and was not in any likely Pegasus folder. Perhaps this was Pegasus successfully defeating the ransomware? I think that the rest of the screen stayed in focus.
Here are SS&D's current schedule settings.
View attachment 13304
View attachment 13305
Do these look reasonable? I thought I had set Scan to once a week.
I downloaded and ran (as Administrator) KpRm as you suggested. Here's the log:
# Run at 2022-04-17 16:51:06
# KpRm (Kernel-panik) version 2.9.3
# Website https://kernel-panik.me/tool/kprm/
# Run by Chris from C:\Users\Chris\Desktop
# Computer Name: MOLLY
# OS: Windows 7 X86 (7601) Service Pack 1
# Number of passes: 1
- Checked options -
~ Delete Tools
~ Delete Quarantines
- Delete Tools -
## AdwCleaner
[OK] C:\AdwCleaner deleted
## Emisoft Emergency Kit
[R] C:\Users\Chris\Desktop\EmsisoftEmergencyKit.exe deleted
[R] C:\EEK deleted
## ESET Online Scanner
[OK] C:\Users\Chris\AppData\Local\ESET\ESETOnlineScanner deleted
[OK] HKLM\SOFTWARE\ESET\ESET Online Scanner deleted
## FRST
[OK] C:\Users\Chris\Desktop\Addition.txt deleted
[OK] C:\Users\Chris\Desktop\Fixlog.txt deleted
[OK] C:\Users\Chris\Desktop\FRST-OlderVersion deleted
[OK] C:\Users\Chris\Desktop\FRST.exe deleted
[OK] C:\Users\Chris\Desktop\FRST.txt deleted
[OK] C:\FRST deleted
-- KPRM finished in 92.13s --
- Need to Restart -
I restarted.
- As has been the case earlier, MalwareBytes window showed, inviting me to update.
- I clicked on Install
- It offered Browser Guard
- I declined the offer because I am running AdBlockPlus in Firefox: the two may conflict
- "Installing" showed, then Installation failed. Please restart your system then try running the installer again".
- Early in this thread, I had to work around Win 7 not being fully patched.
- What, if anything, should I do further?
- Should I be running Malwarebytes regularly?
BTW I remember Opening an email in Pegasus back in March. The text was in green, not the normal black. The window blurred for several seconds then the email disappeared from the screen, and was not in any likely Pegasus folder. Perhaps this was Pegasus successfully defeating the ransomware? I think that the rest of the screen stayed in focus.
Here are SS&D's current schedule settings.
View attachment 13304
View attachment 13305
Do these look reasonable? I thought I had set Scan to once a week.
I don't know what is going on with MalwareBytes, trying to download and install over an older version? You may need to completely uninstall then reinstall.Happy Easter!
- As has been the case earlier, MalwareBytes window showed, inviting me to update.
- I clicked on Install
- It offered Browser Guard
- I declined the offer because I am running AdBlockPlus in Firefox: the two may conflict
- "Installing" showed, then Installation failed. Please restart your system then try running the installer again".
- Early in this thread, I had to work around Win 7 not being fully patched.
- What, if anything, should I do further?
- Should I be running Malwarebytes regularly?
BTW I remember Opening an email in Pegasus back in March. The text was in green, not the normal black. The window blurred for several seconds then the email disappeared from the screen, and was not in any likely Pegasus folder. Perhaps this was Pegasus successfully defeating the ransomware? I think that the rest of the screen stayed in focus.
Here are SS&D's current schedule settings.
View attachment 13304
View attachment 13305
Do these look reasonable? I thought I had set Scan to once a week.
There is a MalwareBytes support forum that can probably give answers as to why it's not updating or installing, you'll need to register and then create a new topic.
https://forums.malwarebytes.com/forum/41-malwarebytes-for-windows-support-forum/
The email, when it opened, could you read what it said?
Typically with a ransomeware note, it remains on desktop so there is no avoidance that it's hit your machine. And the computer will act very un-normal.
I can't say 100% there is not that sort of infection on here but I can say there is/was no evidence that i found.
I can also say that in todays world there is a lot of criminal/hacking activity happening world wide to the point it's scary.
In case or for safe practices, change all your passwords from a known secure computer.
The attachments you posted would not only me to open. You should scan your computer often and follow safe online practices.
- Answers to common security questions - Best Practices by quietman7, MVP
- How Malware Spreads - How did I get infected? by quietman7, MVP
- Simple and easy ways to keep your computer safe and secure on the Internet by Lawrence Abrams, MVP
- How to Prevent Malware by miekiemoes, MVP
- How to backup and restore your data using Cobian Backup by YourHighness
- Slow Computer/browser? It May Not Be Malware by quietman7, MVP
Chris Haslam
New member
About the odd email:
There was no ransomware note. I only know about it because a Spybot scan showed it. When I fixed it there, its "cousin" showed in the next scan.
We are very careful about passwords. We never accept offers from Firefox to remember them. We do change them.
Using a small program that I wrote, I back up incrementally at least daily. It:
My wife and I share an email address. On her PC, Pegasus is set to receive emails. Mine is set not to check for incoming emails. When an email arrives for me, she moves it to New email on my PC. (I can also move an email from her PC to mine, in Pegasus Mail.)
I also backup using Acronis True Image weekly.
BTW I note, thanks to your guidance, on my PC, Firefox's favicons file has dropped from 34MB to 4MB. On my wife's PC, which also showed the ransomware in a scan, Firefox crashes several times a day, causing her to open links again. Which tool cleaned up Firefox for me?
- I was not yet fully awake when it arrived in my inbox.
- I can add that it had what looked like a PDF button
- The email had shown in New email. I clicked on it, then on Open (rather than just seeing it in Preview).
- The email disappeared from New email.
There was no ransomware note. I only know about it because a Spybot scan showed it. When I fixed it there, its "cousin" showed in the next scan.
We are very careful about passwords. We never accept offers from Firefox to remember them. We do change them.
Using a small program that I wrote, I back up incrementally at least daily. It:
- looks for the archive bit being set,
- selects files based on rules in a metadata file,
- gives me, at run time, the ability not to back up a file,
- backs up to a USB stick that is otherwise offline.
My wife and I share an email address. On her PC, Pegasus is set to receive emails. Mine is set not to check for incoming emails. When an email arrives for me, she moves it to New email on my PC. (I can also move an email from her PC to mine, in Pegasus Mail.)
I also backup using Acronis True Image weekly.
BTW I note, thanks to your guidance, on my PC, Firefox's favicons file has dropped from 34MB to 4MB. On my wife's PC, which also showed the ransomware in a scan, Firefox crashes several times a day, causing her to open links again. Which tool cleaned up Firefox for me?
I can't say for sure which command aided in helpingBTW I note, thanks to your guidance, on my PC, Firefox's favicons file has dropped from 34MB to 4MB. On my wife's PC, which also showed the ransomware in a scan, Firefox crashes several times a day, causing her to open links again. Which tool cleaned up Firefox for me?
Below is the list of items to fix by script
It was a tidy up of empty files and a couple of policy restrictions
CreateRestorePoint:
Policies: C:\ProgramData\NTUSER.pol: Restriction <==== ATTENTION
HKLM\SOFTWARE\Policies\Mozilla\Firefox: Restriction <==== ATTENTION
HKLM\SOFTWARE\Policies\Google: Restriction <==== ATTENTION
HKU\S-1-5-21-4166634823-2150066620-1418166359-1000\SOFTWARE\Policies\Google: Restriction <==== ATTENTION
Hosts:
CMD: netsh int ip reset
CMD: ipconfig /flushDNS
EmptyTemp:
Chris Haslam
New member
In a SS&D scan yesterday, VxLock didn't show, but it shows in a scan done today.
Chris Haslam
New member
How do I do that?
I used FileFinder to look for file names containing VXLOCK everywhere on my PC. The only files it found are in Spybot's Quarantine folder. They are .zip files
The scan log is:
Search results from Spybot - Search & Destroy
2022-04-20 18:00:42
Scan took 00:10:21.
6 items found.
MS Direct3D: [SBI $C2A44980] Most recent application (Registry Change, nothing done)
HKEY_USERS\S-1-5-21-4166634823-2150066620-1418166359-1000\Software\Microsoft\Direct3D\MostRecentApplication\Name
Category=Tracks
ThreatLevel=2
Weblink=http://forums.spybot.info/forumdisplay.php?54
Windows: [SBI $1E4E2003] Drivers installation paths (Registry Change, nothing done)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\Installation Sources
Category=Tracks
ThreatLevel=2
Weblink=http://forums.spybot.info/forumdisplay.php?54
Cookie: [SBI $BCOOKIES] Browser: Cookie (1) (Browser: Cookie, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
Cache: [SBI $BCACHE00] Browser: Cache (54) (Browser: Cache, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
History: [SBI $BHISTORY] Browser: History (9) (Browser: History, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
Generic.Ransom.VxLock.886DC9DE;Generic.Ransom.VxLock.886DC9DE: [SBI $SpybotAV] Executable (File, nothing done)
<System>
Category=Viruses
ThreatLevel=5
Weblink=http://forums.spybot.info/forumdisplay.php?54
Properties.size=0
Properties.md5=D41D8CD98F00B204E9800998ECF8427E
--- Spybot - Search & Destroy version: 2.9.82.132 DLL (build: 20211105) ---
...
I used FileFinder to look for file names containing VXLOCK everywhere on my PC. The only files it found are in Spybot's Quarantine folder. They are .zip files
The scan log is:
Search results from Spybot - Search & Destroy
2022-04-20 18:00:42
Scan took 00:10:21.
6 items found.
MS Direct3D: [SBI $C2A44980] Most recent application (Registry Change, nothing done)
HKEY_USERS\S-1-5-21-4166634823-2150066620-1418166359-1000\Software\Microsoft\Direct3D\MostRecentApplication\Name
Category=Tracks
ThreatLevel=2
Weblink=http://forums.spybot.info/forumdisplay.php?54
Windows: [SBI $1E4E2003] Drivers installation paths (Registry Change, nothing done)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\Installation Sources
Category=Tracks
ThreatLevel=2
Weblink=http://forums.spybot.info/forumdisplay.php?54
Cookie: [SBI $BCOOKIES] Browser: Cookie (1) (Browser: Cookie, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
Cache: [SBI $BCACHE00] Browser: Cache (54) (Browser: Cache, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
History: [SBI $BHISTORY] Browser: History (9) (Browser: History, nothing done)
Category=Browser
ThreatLevel=1
Weblink=http://forums.spybot.info/forumdisplay.php?54
Generic.Ransom.VxLock.886DC9DE;Generic.Ransom.VxLock.886DC9DE: [SBI $SpybotAV] Executable (File, nothing done)
<System>
Category=Viruses
ThreatLevel=5
Weblink=http://forums.spybot.info/forumdisplay.php?54
Properties.size=0
Properties.md5=D41D8CD98F00B204E9800998ECF8427E
--- Spybot - Search & Destroy version: 2.9.82.132 DLL (build: 20211105) ---
...
Generic.Ransom.VxLock.886DC9DE;Generic.Ransom.VxLock.886DC9DE: [SBI $SpybotAV] Executable (File, nothing done)
<System>
Category=Viruses
ThreatLevel=5
Weblink=http://forums.spybot.info/forumdisplay.php?54
Properties.size=0
Properties.md5=D41D8CD98F00B204E9800998ECF8427E
Something I pick up on is that it has it listed as a ThreatLevel 5
That's odd to me, if anything I think it should say a ThreatLevel 10 with sirens and whistles going off.
I can't tell if it's picking something up in your browser, temps, or cookies.
I'm going to attempt to contact another advisor and see if she can make heads or tails of this.
- Status
- Not open for further replies.