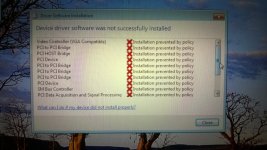
When you see the error for Malwarebytes Anti-Malware
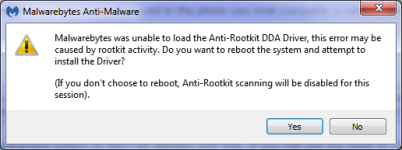
Note: You may see the following message, "Could not load DDA driver". Click Yes, allow your PC to reboot and continue afterwards.
~~~
For problems with Kaspersky 2016, they have a help forum https://forum.kaspersky.com/ and http://support.kaspersky.com/
I've never used this product and would think your probably not the first user who has run into issues and there your more likely to get help much better then what I can suggest.
~~~~
Many people run into the same issue. Why it does this, first thought is security software but, just a thought.
You know, if at any time you feel you need a different or better malware tech, I can refer you to a different help forum or ask a different helper to try and step in, let me know.
~~~~
I have a question
Did you set a new group policy or allow software on the machine to set new Policy restriction on software:?
****
Please open Notepad *Do Not Use Wordpad!* or use any other text editor than Notepad or the script will fail. (Start -> Run -> type notepad in the Open field -> OK) and copy and paste the text present inside the quote box below:
To do this highlight the contents of the box and right click on it and select copy.
Paste this into the open notepad. save it to the Desktop as fixlist.txt
NOTE. It's important that both files, FRST/FRST64 and fixlist.txt are in the same location or the fix will not work.
It needs to be saved Next to the "Farbar Recovery Scan Tool" (If asked to overwrite existing one please allow)

Open FRST/FRST64 and press the > Fix < button just once and wait.
If for some reason the tool needs a restart, please make sure you let the system restart normally. After that let the tool complete its run.
When finished FRST will generate a log on the Desktop (Fixlog.txt). Please post it to your reply.
~~~~
Note: You may see the following message, "Could not load DDA driver". Click Yes, allow your PC to reboot and continue afterwards.
~~~
I had no idea what I was looking at to give any kind of comments on what was displayed in the photo you took Currports. I cannot give you instructions to remove or stop what it located.Hm I guess you don't know enough to tell me which of those processes from for/using Currports look suspicious...
I also tried running KIS 2016 last night to do a full scan but it appears it's now morning and is taking its sweet ass time to load because I can see the load mouse cursor, but where's KIS 2016?? Checking Task manager, I see that AVP.exe *32 has loaded, but where's the GUI?
For problems with Kaspersky 2016, they have a help forum https://forum.kaspersky.com/ and http://support.kaspersky.com/
I've never used this product and would think your probably not the first user who has run into issues and there your more likely to get help much better then what I can suggest.
~~~~
The settings I suggest will also show us items located in quarantine folders so don't be alarmed with this. If you still feel the need to contact Eset support they may be able to help, no idea.As I was saying about ESET picking up said items and other's not pick jack(since I can't edit my previous post), assuming these aren't false positive, then ESET is the only program(that we've tried so far) to detect these new threats but for some reason or another, ESET fails to complete the scan and show us what it found......coincident that I happen to be scanning for malware/viruses and ESET fails, no? I will contact ESET now to see what the problem is, and also link them to this thread.
Many people run into the same issue. Why it does this, first thought is security software but, just a thought.
You know, if at any time you feel you need a different or better malware tech, I can refer you to a different help forum or ask a different helper to try and step in, let me know.
~~~~
I have a question
Did you set a new group policy or allow software on the machine to set new Policy restriction on software:?
Your newest FRST log shows these are now different from your originals.HKLM Group Policy restriction on software: *.JSE <====== ATTENTION
HKLM Group Policy restriction on software: *.JS <====== ATTENTION
HKLM Group Policy restriction on software: *.VBE <====== ATTENTION
HKLM Group Policy restriction on software: *.VBS <====== ATTENTION
HKLM Group Policy restriction on software: *.WSF <====== ATTENTION
HKLM Group Policy restriction on software: %userprofile% <====== ATTENTION
HKLM Group Policy restriction on software: C:\Windows\System32\VSSAdmin.exe <====== ATTENTION
HKLM Group Policy restriction on software: %appdata% <====== ATTENTION
HKLM Group Policy restriction on software: *.WSH <====== ATTENTION
HKLM Group Policy restriction on software: %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRoot% <====== ATTENTION
HKLM Group Policy restriction on software: C:\Program Files (x86)\ProcessExplorer\ <====== ATTENTION
HKLM Group Policy restriction on software: C:\Users\Electrike\Desktop\Group Policy.msc <====== ATTENTION
HKLM Group Policy restriction on software: C:\Windows\system32\cmd.exe <====== ATTENTION
HKLM Group Policy restriction on software: C:\Windows\system32\taskmgr.exe <====== ATTENTION
HKLM Group Policy restriction on software: %HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ProgramFilesDir% <====== ATTENTION
HKLM Group Policy restriction on software: %userprofile%\Downloads <====== ATTENTION
****
Please open Notepad *Do Not Use Wordpad!* or use any other text editor than Notepad or the script will fail. (Start -> Run -> type notepad in the Open field -> OK) and copy and paste the text present inside the quote box below:
To do this highlight the contents of the box and right click on it and select copy.
Paste this into the open notepad. save it to the Desktop as fixlist.txt
NOTE. It's important that both files, FRST/FRST64 and fixlist.txt are in the same location or the fix will not work.
It needs to be saved Next to the "Farbar Recovery Scan Tool" (If asked to overwrite existing one please allow)
start
CreateRestorePoint:
CloseProcesses:
HKLM\SOFTWARE\Policies\Microsoft\Internet Explorer: Restriction <======= ATTENTION
HKU\.DEFAULT\SOFTWARE\Policies\Microsoft\Internet Explorer: Restriction <======= ATTENTION
HKU\S-1-5-21-2798084944-1211984927-2140173799-1000\SOFTWARE\Policies\Microsoft\Internet Explorer: Restriction <======= ATTENTION
SearchScopes: HKLM -> {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL =
SearchScopes: HKLM-x32 -> {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL =
SearchScopes: HKU\S-1-5-21-2798084944-1211984927-2140173799-1000 -> DefaultScope {B0C9ACC6-6B01-470F-B98A-DCC12B58795A} URL =
SearchScopes: HKU\S-1-5-21-2798084944-1211984927-2140173799-1001 -> {B0C9ACC6-6B01-470F-B98A-DCC12B58795A} URL =
BHO: No Name -> {9030D464-4C02-4ABF-8ECC-5164760863C6} -> No File
BHO-x32: No Name -> {9030D464-4C02-4ABF-8ECC-5164760863C6} -> No File
C:\ProgramData\DP45977C.lfl
C:\Users\Electrike\AppData\Local\Temp\procexp64.exe
CustomCLSID: HKU\S-1-5-21-2798084944-1211984927-2140173799-1001_Classes\CLSID\{162C6FB5-44D3-435B-903D-E613FA093FB5}\InprocServer32 -> C:\Users\Electrike\AppData\Local\Microsoft\OneDrive\17.3.6281.1202\amd64\FileCoAuthLib64.dll => No File (the data entry has 3 more characters).
CustomCLSID: HKU\S-1-5-21-2798084944-1211984927-2140173799-1001_Classes\CLSID\{71DCE5D6-4B57-496B-AC21-CD5B54EB93FD}\localserver32 -> C:\Users\Electrike\AppData\Local\Microsoft\OneDrive\17.3.6281.1202\FileCoAuth.exe => No File
CMD: netsh winsock reset catalog
CMD: netsh int ip reset
CMD: ipconfig /release
CMD: ipconfig /renew
CMD: netsh int ipv4 reset
CMD: netsh int ipv6 reset
CMD: ipconfig /flushdns
CMD: bitsadmin /reset /allusers
Reg: reg delete HKLM\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local /f
Reg: reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local /f
EmptyTemp:
End
Open FRST/FRST64 and press the > Fix < button just once and wait.
If for some reason the tool needs a restart, please make sure you let the system restart normally. After that let the tool complete its run.
When finished FRST will generate a log on the Desktop (Fixlog.txt). Please post it to your reply.
~~~~